This is a continuation of my blog series on Alert Logic’s full stack security approach to protecting your web applications in the cloud. In this post, I’m going to discuss how Alert Logic protects your development platform.
PHP has been around since the mid-1990s and quickly proliferated on the web as an easy-to-use server-side and command line scripting language, allowing users to build dynamic web pages and applications. PHP remains one of the most in-demand programming languages today, mostly due to its use in the internet’s most popular content management systems (WordPress, Drupal), e-commerce platforms (Magento, OpenCart), and popular web development frameworks (Laravel, CakePHP).
On a related note, Alert Logic’s Joe Hitchcock is kicking off an excellent blog series on language-based vulnerabilities. In the first post, he’s doing a technical deep dive on PHP execution. In addition to command injection, here are some other common PHP vulnerabilities, which we’ll discuss in this article:
- SQL Injection
- Cross-site scripting
- File Inclusions (Remote & Local)
So, let’s take a look at how a full stack security approach can help protect your PHP applications against these common attack vectors.
Command Injection
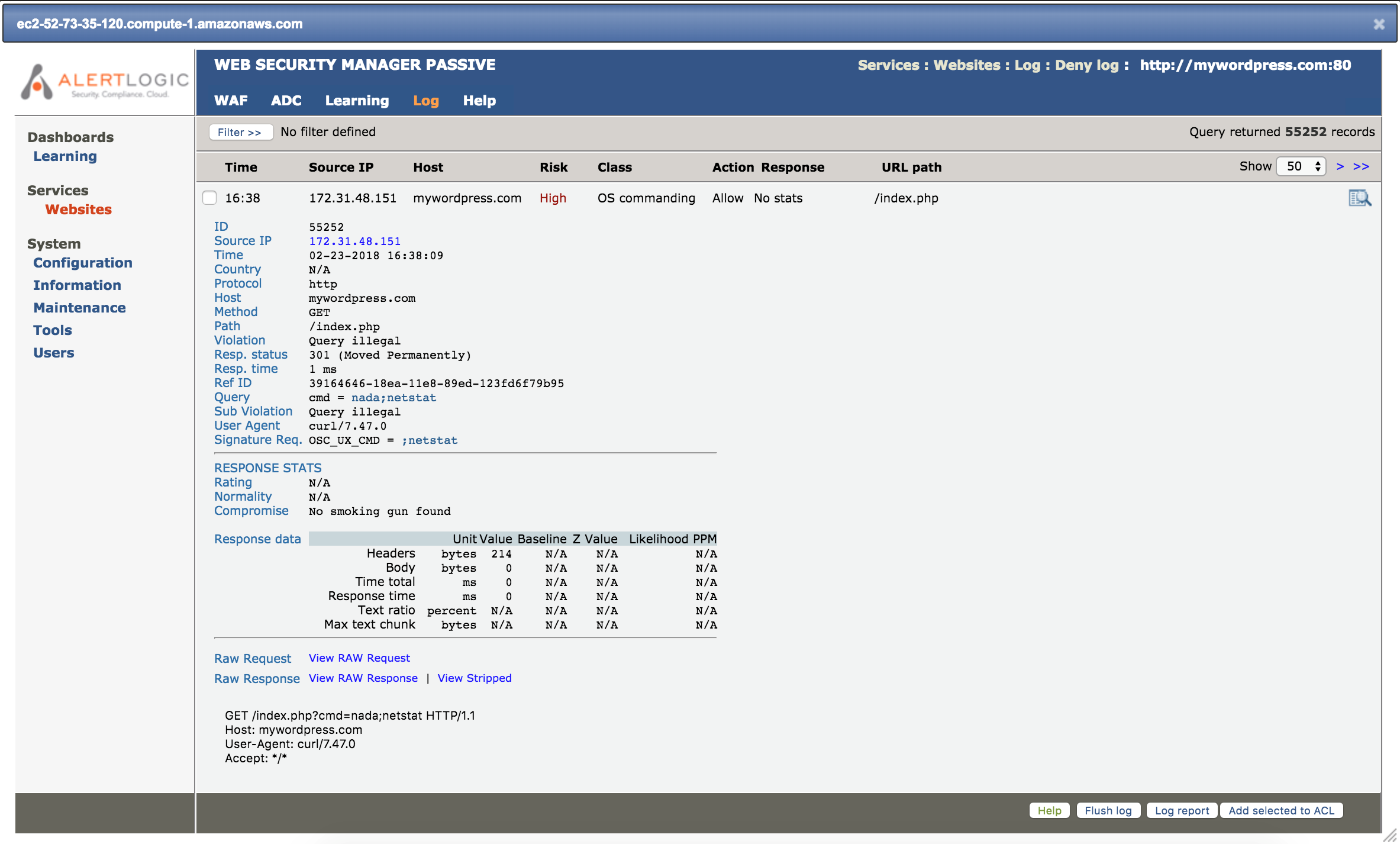
A command injection attack takes advantage of unsanitized PHP input validation, giving malicious users the opportunity to pass in arbitrary commands to the host system. Because the input is unsanitized, the attacker can pass in additional system commands that will be executed as system command functions of PHP, such as system or shell exec. Below we see Alert Logic’s web application firewall, Web Security Manager (WSM) detects and alerts on my command injection attempt. Check out the “Raw Request” at the bottom, and you can see the netstat command “piggybacked” onto the valid system command string of the GET request.
SQL Injection
A common error administrators make is to store PHP session IDs in a database in order to further validate user actions post-login. If the session ID isn’t sanitized properly, it leaves an opportunity for a malicious attacker to attempt a SQL injection. Here’s an example of a blind SQL PHP sessionID injection:
GET /page.php
host: site.com
UserAgent: Mozillla/5.0
Cookie: PHPSESSID=764EFA883DDA1E11DB47671C4A3BBD9E’ and (Select 1)=1—+
Referer: site.com/index.php
It’s a common example of the types of attacks our certified SOC analysts see on a daily basis. Anytime an analyst works an incident, all supporting data of that case get fed into our security analytics platform. This unique combination of human expertise and sophisticated machine learning has allowed Alert Logic to develop world-class in-house threat research using real-world signatures, rather than simply relying on public CVEs. Anytime our SOC discovers a new vulnerability, such as the SQL injection attempt above, we leverage our integrated security model to roll out that protection to all other customer environments via Threat Manager, Alert Logic’s IDS Software and vulnerability management platform.
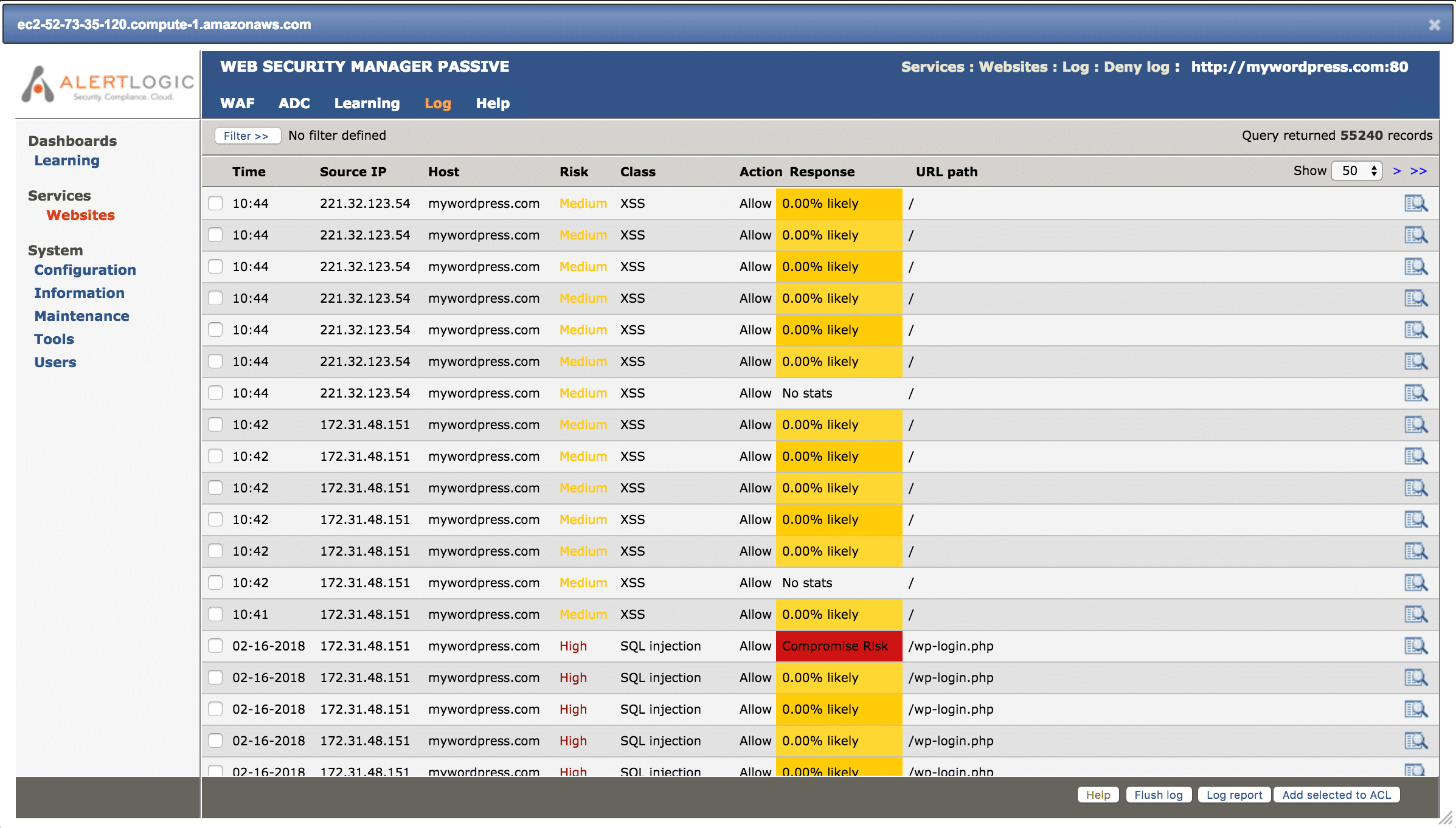
Cross-site scripting is still popular for attackers
Another popular type of injection attack is cross-site scripting, where a would-be cyber attacker injects client-side code, commonly Javascript, into a URL or form that echoes the data of form results through the PHP interpreter without adequate sanitization. Alert Logic has nearly 100 IDS signatures specifically looking for PHP-related cross-site scripting attacks.
Here’s an example from the WSM console:
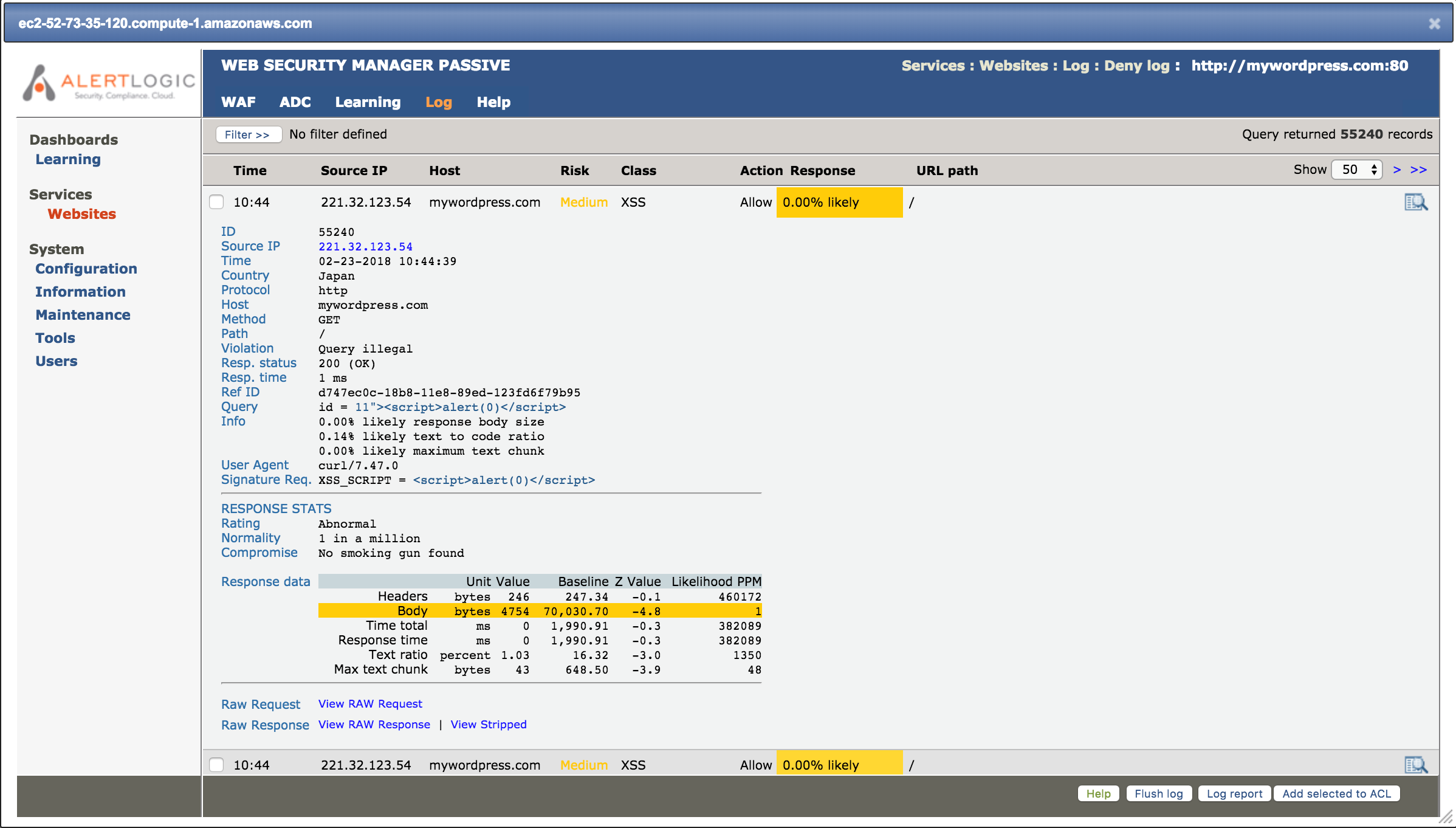
Clicking on the expanded view gives the details of the XSS attack:
File Inclusion vulnerabilities still persist
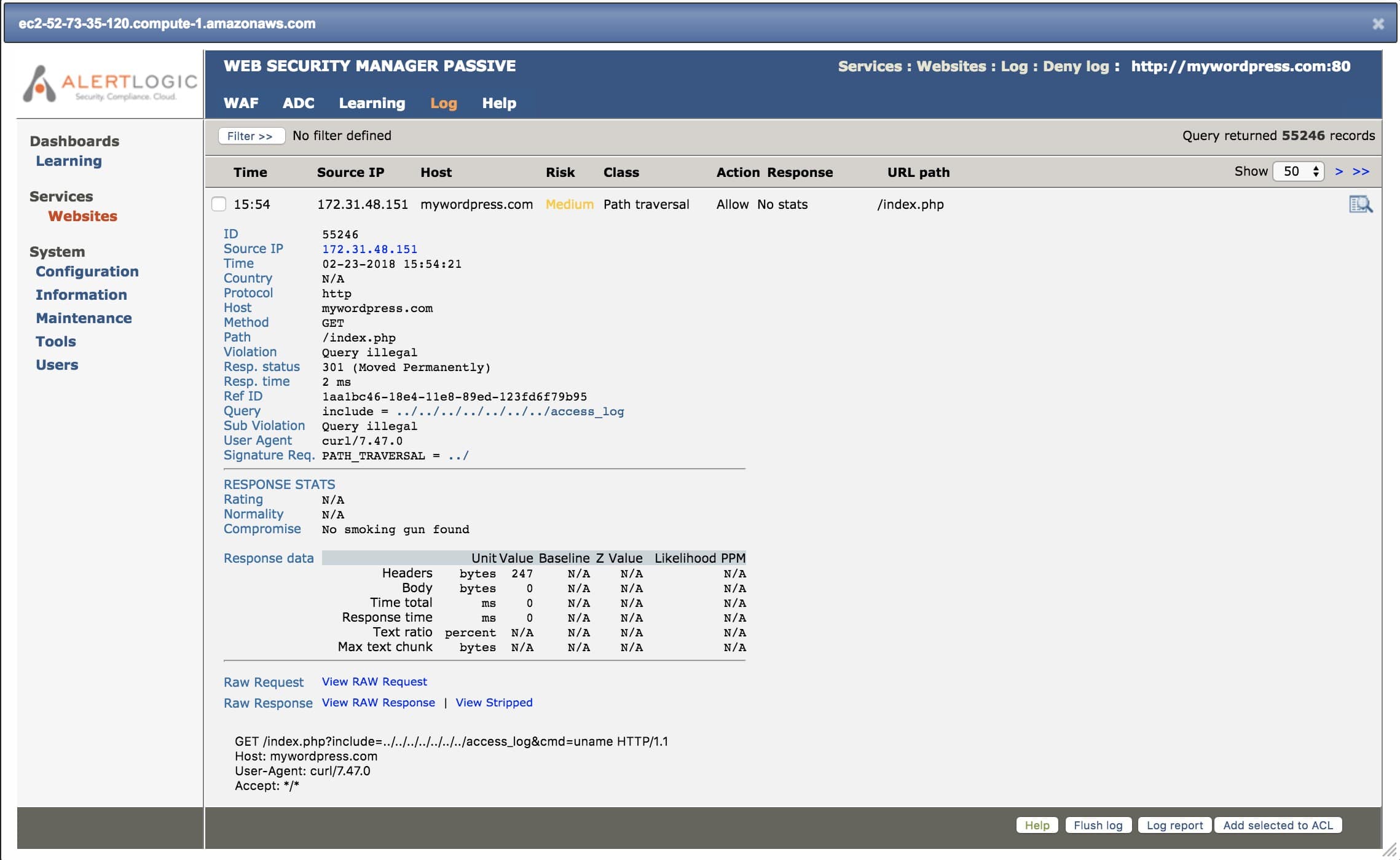
Similar to a command execution attack, file inclusions take advantage of a PHP script with no or improperly sanitized input. File inclusions can be characterized as remote or local. A remote file inclusion allows a malicious attacker to take advantage of the allow_url_fopen() or allow_url_include() directives in a PHP script in order to force the loading of a text file with malicious PHP code in it from a remote URL, which will be executed locally upon loading.
A local file inclusion is a similar vulnerability in which the above directives are off. Essentially, a malicious user gains access to a local file on the server using directory traversal (../..) or executes code by accessing a resource that logs user-controlled data.
These examples have been shown using Alert Logic’s Web Security Manager. WSM is a web-based IDS that alerts on layer-7 attacks, which is where we’ll see common PHP vulnerabilities, such as command and SQL injections, cross-site scripting, and local and remote file inclusions. In a future blog post, we’ll dig into Alert Logic’s SaaS-based managed web application firewall (WAF), which takes application protection a step further by proactively blocking attacks after they have been detected.
For PHP alone, Alert Logic has over 1,800 scan checks and 3,800+ IDS signatures and log message types built from years of threat intelligence research and managing a security operations center (SOC) in support of more than 4,000 customers. However, PHP is just one example of the many the popular development platforms in use on the web today. Regardless of your choice of development platform, rest assured that Alert Logic has you covered. In the next full stack post, we’ll dive into protecting databases.
Check out the complete series on full stack security: