Updated 4/27/18 to confirm Microsoft has released two new updates designed to mitigate Spectre variant 2.
The security world is spinning over the disclosure of two critical CPU vulnerabilities called Meltdown and Spectre. Here’s what you need to know (scroll to the bottom for latest updates).
Key Details
- What’s happening: Severe design flaws in modern CPUs were officially disclosed on Wednesday, triggering a wave of urgent security advisories and patches.
- Two bugs, not one: The two vulnerabilities — named Meltdown and Spectre — are hardware bugs that can allow attackers to steal information from the memory of other programs (note: NOT launch malware). They work in different ways, affect different processors to varying degrees, and require different fixes (more info on each here and below).
- Not just an Intel problem: Attention was originally focused on Intel chips, but ARM and AMD processors are also affected to some extent. As such, researchers have pointed out this puts an extremely wide variety of systems at risk, from desktops and laptops to mobile devices and servers.
- Patches released: The bugs had originally been reported privately back in June, with an embargo set for January 9 to give vendors time to work on patches. As details of the flaws began leaking on Tuesday, however, vendors were forced into early action. Microsoft issued an emergency update to Windows systems on Wednesday. Patches to macOS and Linux systems are also available.
- Additional fixes to come: Microsoft and Amazon have also announced scheduled downtime and updates of their cloud services so that clients can focus on securing AWS and Azure security. Additional updates from a wide range of products and services are expected to be rolled out. A list of advisories and notices can be found at Bleeping Computer.
- What to do now: Don’t panic. Take the time to properly assess, test, and carefully implement OS and firmware updates as they are made available. Microsoft has also issued guidance for Windows users here). In addition, experts are advising turning on-site isolation in Chrome and Firefox to prevent malicious websites from exploiting these flaws.
- UPDATE: AV incompatibility with Windows 10 patch: Microsoft is reporting compatibility issues with a number of antivirus products. To help prevent errors, the company is only rolling out the Windows security update to devices with AV software that is confirmed to be compatible.
- ” v:shapes=”Text_x0020_Box_x0020_2″>More to come: This post will be updated as new information arrives. Scroll to the bottom of the post for the latest updates.
After rumors began circulating and initial details were leaked, on Wednesday cybersecurity researchers officially disclosed details surrounding two critical vulnerabilities affecting Intel, AMD, and ARM processors (CPUs).
Dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), these hardware bugs can allow malicious programs to steal data from the memory of other programs, potentially putting a wide variety of sensitive information such as stored passwords, crypto-keys, and files at risk.
Understanding Meltdown and Spectre
Technical details on the vulnerabilities can be found on the dedicated site meltdownattack.com and in this write up by Google’s Project Zero team, which was partially responsible for their discovery.
In short, the problem lies in the way most modern processors have been built to rely on “speculative execution,” a technique which helps them optimize performance. Essentially what the processors do is try to predict the instructions they’re going to be asked to carry out next. They then queue up and execute the necessary next bit of code so they’re ahead of the game. There are times when they guess wrong, however. In these cases, they undo the speculative code, but they don’t completely roll back every step they’ve taken, and they can leave remnants of data they weren’t actually meant to fetch in caches that can be accessed later.
Meltdown and Spectre are closely related vulnerabilities that can be exploited to abuse this process in different ways, allowing malicious programs to get access to data they shouldn’t have. This thread by researcher Graham Sutherland is a great explainer that goes into more detail.
In addition, The Register has published a good, thorough breakdown of the differences between the two vulnerabilities, which I’ll summarize below:
Meltdown
Rogue data cache load — CVE-2017-5754
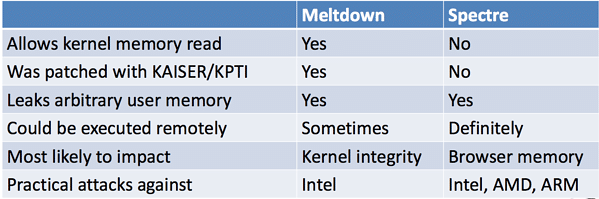
- Can be exploited to: Read the contents of private kernel memory from an unprivileged user process.
- Processors affected: All out-of-order Intel processors released since 1995 with the exception of Itanium and pre-2013 Atoms. A list of vulnerable ARM processors and mitigations is listed here. No AMD processors are affected by Meltdown.
- Fixes: Workaround patches have been released for Windows and Linux (in the latter case with KAISER/KPTI, which results in a “non-negligible” hit to performance). Apple’s macOS has been patched since version 10.13.2, and iOS since version 11.2. According to Intel, Meltdown can be mitigated by OS updates with no additional firmware updates necessary.Note: Windows Server admins must enable the kernel-user space splitting feature once the update is installed. Amazon has issued updates to its AWS Linux guest kernels and Microsoft is rolling out fixes to Azure, as well. A good list of vendor advisories and updates is available here. For more details on Meltdown, see the technical whitepaper.
Spectre
Variant 1: bounds check bypass — CVE-2017-5753
Variant 2: branch target injection — CVE-2017-5715
- Can be exploited to: Extract information from other running processes (ex: stealing login cookies from browsers).
- Processors affected: Intel, ARM, and AMD processors are all reportedly affected to some degree. See this post for more specifics.
- Fixes: Experts have universally described Spectre as being tougher to patch than Meltdown, though thankfully it is more difficult to practically exploit, too. According to researchers, the most likely exploitation of Spectre would be using JavaScript (say in a malicious ad) to leak information, session keys, etc. cached in the browser. Mozilla, Google, and Microsoft have all issued browser updates to make that scenario exponentially more difficult, though not impossible. Experts also recommend turning on-site isolation in Chrome and Firefox as extra precautions.Apple has issued Spectre mitigations in iOS 11.2.2, and the macOS High Sierra 10.13.2 supplemental update.Note: While Spectre variant 1 (bounds check bypass) can be mitigated with OS updates, Spectre variant 2 (branch target injection) requires firmware/microcode fixes. Processor makers have said they will be issuing microcode updates, accordingly. Intel has released new Linux Processor microcode data files that can be used to add mitigations without having to perform a BIOS update, though some issues have been reported with Broadwell and Haswell CPUs. A microcode update from AMD addressing CVE-2017-5715 is also available now, and the company says it will be introducing additional fixes starting with Ryzen and EPYC processors.It’s also worth noting Google has announced a new technique for mitigating Spectre it’s calling Retpoline. For more details on Spectre, see the technical whitepaper.
The following is a handy comparison table provided by researcher Jake Williams as part of a presentation provided by SANS and Rendition Infosec:
Source: SANS / Rendition Infosec.
It’s important to note that both vulnerabilities put information disclosure at risk. Neither are remote execution vulnerabilities — in other words, they don’t allow attackers to run malware. So, the silver lining here is this all could be much worse.
What to do now
For now, the best course of action is not to panic and instead take the time to properly assess, test, and carefully implement OS and firmware updates as they are made available — especially since there have been a variety of widespread compatibility issues.
It’s also important to note that there have been a variety of complaints regarding the performance impacts of the patches, though vendors have insisted they should not be significant or noticeable to the average user. According to the Register, hits to performance are “highly variable and depend on a number of factors such as the workload in question and the technology involved.”
Microsoft has issued specific guidance for Windows users here. In the meantime, experts are also advising turning on-site isolation in Chrome and Firefox to prevent malicious websites from exploiting these flaws.
Information around these major vulnerabilities is still being circulated, debated, and processed, so there is likely much more to come. We’ll be following closely and providing updates as they become available.
In the meantime, Stu Sjouwerman at KnowBe4 has a good write-up of how to explain Meltdown and Spectre to your C-level execs and end users.
Update (1/5/18): Microsoft warning users’ AVs may prevent them from receiving the update
Microsoft is reporting its security update is resulting in compatibility issues with a number of antivirus products. To help prevent errors, the company is only rolling out the Windows security update addressing Meltdown to devices with AV software confirmed to be compatible.
Per Microsoft:
Note: Customers will not receive these security updates and will not be protected from security vulnerabilities unless their anti-virus software vendor sets the following registry key:
Key=”HKEY_LOCAL_MACHINE” Subkey=”SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat” Value=”cadca5fe-87d3-4b96-b7fb-a231484277cc” Type=”REG_DWORD”
Data=”0x00000000”
If you’re not using a third-party antivirus product but Windows Defender is disabled, you may also need to manually set the registry key before applying the patch. If you are not provided with the Windows update automatically you can download the update packages directly from Microsoft here.
Update (1/9/18): Microsoft has stopped delivering security update to AMD machines
As first reported at the Verge, Microsoft has received numerous reports of PCs running AMD processors not booting after installing the latest Windows security update. After investigating, the company confirmed there are issues, and has stopped delivering the update to AMD devices. Affected users need to visit Microsoft’s support site for instructions on getting their machines back up and running.
Update (1/17/18): Microsoft has released new patches that appear to apply specifically to AMD devices
KB4073578 for Windows 7 SP1 and Windows Server 2008 R2 SP1 and KB4073576 for Windows 8.1 and Windows Server 2012 R2 seem to be specifically developed for AMD devices. But, some experts are scratching their heads at the lack of clear installation instructions and the absence of an update for Windows 10.
Update (1/10/18): Microsoft has shared details on potential performance impact
As with the other operating systems, Windows patches addressing Meltdown and Spectre are expected to take a non-insignificant toll, with older devices and operating systems suffering bigger hits. In a blog post, Microsoft Executive VP Terry Myerson explains the impact of these fixes can vary as follows:
- Windows 10 on 2016-era PCs with Skylake, Kaby Lake, or newer CPU: Single-digit slowdowns, which most users won’t notice.
- Windows 10 on 2015-era PCs with Haswell or older CPU: Slowdown can be more significant. Some users may notice a decrease in performance.
- Windows 8 or Windows 7 on 2015-era PCs with Haswell or older CPU: Most users will likely notice a decrease in system performance.
- Windows Server (any CPU): Mitigations to isolate code within a Windows Server instance result in a more significant performance impact. According to Myerson, “This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance and balance the security versus performance tradeoff for your environment.”
The note of caution regarding the impact on Windows Server performance is especially noteworthy. Microsoft is essentially recommending that admins consider holding off on updates on machines that don’t run untrusted code.
Update (1/12/18): Intel releases microcode updates, Microsoft clarifies registry key requirement
After promising firmware updates for 90 percent of affected processors made in the past five years by January 12, Intel has now released new Linux Processor microcode data files that can be used to add Meltdown and Spectre mitigations without having to perform a BIOS update.
These microcode fixes apply to a specific list of processors, which Bleeping Computer has provided here, along with instructions and a video example that walks through the install process.
Intel is already confirming reports of glitches, however, specifically on updated systems running Intel Broadwell and Haswell CPUs.
UPDATE 1/18/18: Intel is now confirming reboot issues are not confined to Broadwell and Haswell chips
Machines with newer CPUs such as Ivy Bridge, Sandy Bridge, Skylake, and Kaby Lake processors are experiencing more frequent reboots, too.
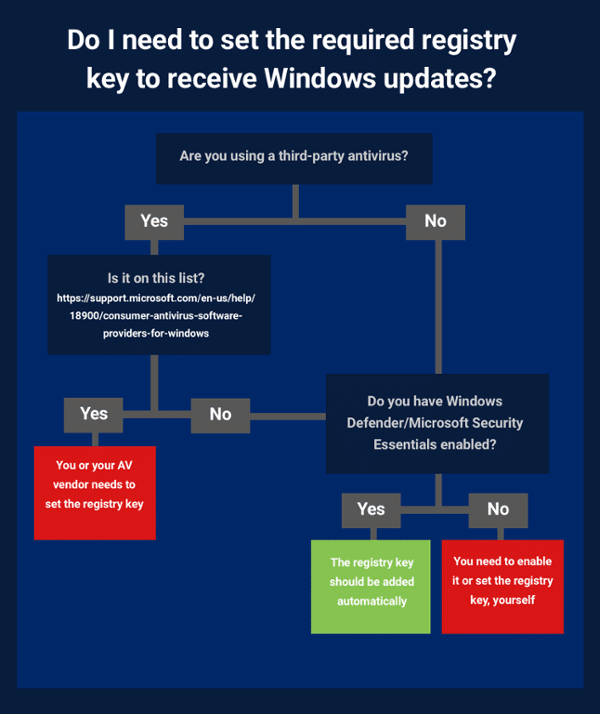
In other news, Microsoft has clarified that Windows Defender Antivirus, System Center Endpoint Protection, and Microsoft Security Essentials are compatible with the update and do set the required registry key.
That means as long as you have one of these built-in Microsoft protections enabled the registry key should be set automatically — no further, manual action should be necessary.
Big caveat: If you’re using third-party software that Microsoft officially recognizes as AV, it is important to note that Windows Defender and Microsoft Security Essentials will turn themselves off by default. That means the registry key won’t be added unless you or your AV actively do it.
To provide additional clarity, here is a flow chart that can help you determine your situation:
If you are using an AV and still haven’t received the Windows patch yet, you are advised to wait until your AV vendor either issues an update that sets the registry key for you or specifically recommends that you do so, yourself.
Update (1/17/18): Windows security updates leave 32bit (x86) systems vulnerable to Meltdown
Just when it seemed like Meltdown had at least been dealt with, several readers pointed out that it appears Windows patches for 32-bit systems (x86-based systems) do not provide Meltdown mitigations. Per Microsoft:
The existing 32-bit update packages listed in this advisory fully address CVE-2017-5753 and CVE-2017-5715, but do not provide protections for CVE-2017-5754 at this time. Microsoft is continuing to work with affected chip manufacturers and investigate the best way to provide mitigations for x86 customers, which may be provided in a future update.
No word yet from Microsoft on when additional OS patches for 32-bit Windows systems will be available, or whether Meltdown will have to be addressed by firmware updates on those machines.
In addition, Microsoft has also issued an alert that Group or MDM policy configurations may be disabling updates for some customers. According to the company, if you have Group or MDM policy settings configured to disable preview builds, your machines may not be receiving updates (see what those settings are here). To fix that, Microsoft recommends temporarily changing Group/MDM policy settings to “Not Configured” and changing them back once the updates have been installed.
Update (1/18/18): Microsoft resumes rolling out updates to AMD devices
Microsoft has announced it will resume rolling out patches for AMD devices running Windows 7 SP1 and Windows Server 2008 R2 SP1, Windows 8.1 and Windows Server 2012 R2, and Windows 10, version 1709. Updates for four versions of Windows 10 — 1511, 1607, and 1703 — are still paused, as the update for Windows Server 2016 and Windows 10 Enterprise.
UPDATE (1/22/18): Intel now recommending customers NOT apply the firmware update
The company has reportedly discovered the root cause of the Broadwell and Haswell boot issues and is testing an updated patch. In the meantime, it is recommending customers stop deployment of the current patch to avoid reboots and other “unpredictable system behavior.”
UPDATE 1/29/18: Microsoft issues an emergency update to disable Intel’s Spectre variant 2 mitigation
Microsoft has issued an emergency out of band update (KB4078130) that disables the mitigation for Spectre variant 2 (branch target injection) that was included in Intel’s buggy microcode updates. Microsoft justified the move by pointing to reports that Intel’s new microcode can cause higher than expected reboots which may result in data loss or corruption (confirmed in Intel’s Q4 2017 financial results statement).
Microsoft’s update is available for Windows 7 (SP1), Windows 8.1, and all versions of Windows 10. It can be downloaded here. Alternatively, the company has also provided instructions to help customers manually disable and enable Spectre variant 2 mitigation via registry setting changes. You can find the instructions for server customers here, and for all other customers here.
UPDATE 2/7/18: New microcode update for Skylake processors released
Intel has issued a new microcode update for Skylake processors that addresses Spectre variant 2. Skylake system owners should expect firmware updates soon. Fixes for other chips remain in beta testing.
UPDATE (2/13/18): Microsoft unveils new dashboard to track update process
Microsoft has added capabilities to its free Windows Analytics service to help IT pros better track and manage their Meltdown and Spectre patching process. The new features include a dashboard that highlights the status of antivirus compatibility, Windows security updates, and firmware updates — all in one place for every Windows device you manage.
UPDATE 2/21/18: Additional microcode updates addressing Spectre variant 2 available
Intel reports its microcode update for Skylake processors is stable, and additional updates for Kaby Lake and Coffee Lake are being rolled out, as well. Considering the problems experienced with the initial firmware updates, many experts are advising caution and careful testing before installing the new updates, however. According to Intel, fixes for Sandy Bridge, Ivy Bridge, Broadwell, and Haswell processors are still in beta. You can find the micocode patch update schedules for all Intel chips here.
UPDATE 3/2/18: Microsoft includes microcode fixes for Intel Skylake processors in the latest Windows update
While that update (KB4090007) only applies to Windows 10 version 1709 and Windows Server version 1709, the company has also announced it is working with Intel on future updates for additional Windows versions and Intel processors.
UPDATE 3/14/18: Microsoft has removed AV registry key requirement for Windows 10 users, and is offering additional Intel microcode fixes in March Windows update
Windows 10 users who have third-party antivirus software installed no longer need to make sure their AV vendors have set a special registry key in order to receive Windows updates. That requirement does still apply to all other versions of Windows. In addition, Microsoft is now including microcode fixes for Intel Skylake, Kaby Lake, and Coffee Lake processors in the March Windows update (KB4090007). Once again, these fixes are only currently available for Windows 10 version 1709 and Windows Server version 1709.
UPDATE 4/5/18: Intel reveals list of processors that won’t receive Meltdown and Spectre patches
The company has confirmed the following families of older processors won’t receive microcode updates designed to mitigate the vulnerabilities: Bloomfield, Bloomfield Xeon, Clarksfield, Gulftown, Harpertown Xeon C0 and E0, Jasper Forest, Penryn/QC, SoFIA 3GR, Wolfdale, Wolfdale Xeon, Yorkfield, and Yorkfield Xeon. More info here.
UPDATE 4/26/18: Windows 7 and Windows Server 2008 R2 64-bit systems at risk
Researchers have discovered that Microsoft inadvertently introduced an even bigger security flaw trying to fix Meltdown in Windows 7 and Windows Server 2008 R2 64-bit systems. The flaw, dubbed “Total Meltdown” can give attackers complete read/write access to any memory on a compromised system. If you have installed any updates in January, February, and March you are advised to install April updates (KB4093118 or KB4088881) as quickly as possible to mitigate this new flaw.
UPDATE 4/27/18: Microsoft has released two new updates mitigating Spectre variant 2 for Windows 10 and Windows Server 2016 systems
The first, KB4078407, is available as a manual update only and is positioned as a “do-over” of sorts to Microsoft’s original mitigations included in its January 4 updates. The second update, KB4091666, is also available as a manual download and is for Intel systems only. It includes microcode fixes for additional Intel models not included in the previous March updates.
Stay informed
Get new updates on Meltdown and Spectre sent directly to your inbox when you subscribe to the Alert Logic blog.