You may be used to hearing that cyberattacks are becoming more widespread and destructive every year. That’s still true, but recent world events are underscoring the point. COVID-19, for instance, has left a lasting mark on our working lives. Remote or hybrid work is now the norm, which means you’re much more likely to use the cloud for secure flexibility, tossing a wider net over remote devices at risk of a data breach.
Meanwhile, geopolitical tensions are simmering more ferociously. Russian hackers are a serious threat to public and private organizations in the West. China, for its part, engaged in “record levels” of cyber-attacks throughout 2021, The Guardian shared. This gives some hacking groups extra reach and resources for large-scale data damage. IBM reports that the price of breaches within the U.S. hit the highest average in 17 years.
Whether you’re keeping an eye on advanced phishing, DDoS attacks, malware infections, or preventable cracks in data compliance, there’s much to anticipate for your own cybersecurity. So, let’s put the current trends in perspective. We’ve drawn together some cybersecurity statistics that show the threats against us now – and what you can do to stop them.
Trends in Cybersecurity for 2022
Same as always, some industries are larger targets for a cybersecurity breach. But the focus is narrowing on something that runs through commerce as a whole: the supply chain.
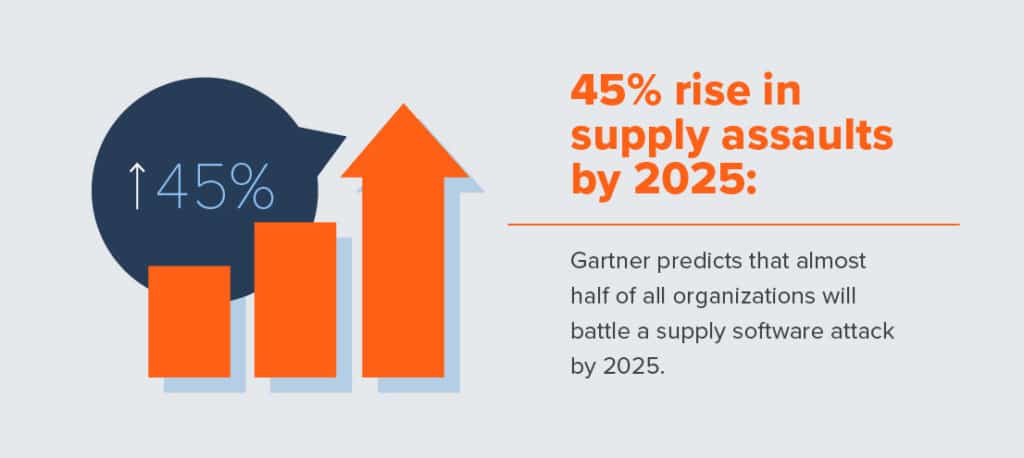
Gartner predicts that by 2025, 45% of organizations will have experienced an attack on their supply software. Why? Because there are many weak entry points – usually smaller, inexperienced companies that don’t have adequate protection. If a bad actor manages to infiltrate one system, grabbing countless pieces of consumer data, they can work their way through the chain and disrupt every organization linked to it.
The 2020 SolarWinds Orion debacle – in which hackers modified raw software code, compromising roughly 100 companies and a dozen government agencies – proved that digital management tools can be a powerful Trojan Horse. The attack installed temporary update files within the software and imitated regular network traffic to cover their tracks. According to Cybersecurity Dive, “in the first nine months of 2021, the Orion breach cost SolarWinds $40 million.” This is meant to shake out to $20 million annually as ‘security by design’ is developed.
Given the dependent nature of supply chains, we cannot ignore this new menace to software that seems safe. One infection may take an astonishingly short amount of time to spread and wreak havoc. Supply chains will feel the pressure to evolve with the tools they rely on, as more software providers rethink their signed-and-sealed coding architecture.
However, if we turn to industry threats, some areas of activity are in the spotlight for data breaches and ransomware demands:
Healthcare
Packed with extremely sensitive information, healthcare databases are one of the top targets for malicious agents. The U.S. Department of Health & Human Services has revealed that 82 ransomware attacks harmed global healthcare provision from January to May 2021. On home turf, hackers waged war against hospitals, surgeries, rehab centers, and other treatment spaces, and 19% of incidents in the U.S. report affected the clinical space.
Telecommunications
Telecom businesses continue to be some of the worst hit with cybersecurity attacks. Ernst & Young’s annual risk report claims that operators saw attacks increase by 75% over 2021. 47% say “they’ve never been more concerned about their own ability to manage cyber threats.” This may be down to the additional time people are spending online, solving queries through live chat rather than phone conversations.
Education
By September 2021, it emerged that educational institutions were hit by 5.8 million cyber-attacks around the world – 63% of every ransomware attack. Referring to Microsoft’s Security Survey, writer George Lamont, from Real Clear Education, has called for treating cybersecurity just like a company does. “The real way to improve security across the education sector,” he says, “is through a Collective Defense model: requiring schools, like private-sector companies, to proactively defend with their peers up and down the vertical supply chain.”
Cybersecurity stats show these industries are especially exposed. If you work within them, there should be no delay for a full security audit, unmasking the weak spots in your business model, user privileges, firewalls, encryption techniques, and remote management.
But what about other, more general trends guiding cybersecurity? What can they teach us about modern threats and responses?
- Small businesses are very vulnerable: As we alluded to in the supply chain discussion, small and medium-sized enterprises (SMEs) are at particular risk of cyber assault. Hackers know they are most likely to have immature security measures in place, if any at all. According to insurance experts Advisor Smith, 42% of small businesses suffered a cyber-attack last year. It’s worth noting that only 72% have locked their cybersecurity into place. That means more than a quarter of SMEs have no cybersecurity to speak of.
- Quantum computing will change everything: We may still be a decade or so away from quantum computers entering the mainstream, but this technology is already fraught with cybersecurity risk. Chiefly, it reads data on a quantum level, just like particle physics (i.e., the smallest possible scale, called a ‘qubit’). 1s and 0s are analyzed for every potential combination simultaneously, improving calculations by an untold degree. Yet more encryption challenges will follow. Quantum secure distribution is under development to catch unauthorized observers as the qubits are translated.
- CISOs are becoming more independent: Typically, a CISO reports to their CIO, making cybersecurity subservient to IT concerns rather than an extension of them. But this is changing too. “A growing trend,” explains Alex Cunningham, a cyber expert, “is for the CISO to report to the chief executive officer, which makes a lot of sense given the CISO’s unique viewpoint across the entire enterprise.” It’s a critical distinction between keeping tech up and running versus making those tools and the culture surrounding them safe.
Standout Cybersecurity Stats Today
How rampant is cybercrime today? The full extent may surprise you. With a broader attack surface – the consequence of remote working – cybersecurity ventures are feeling the strain of more ground to cover.
Prevalence
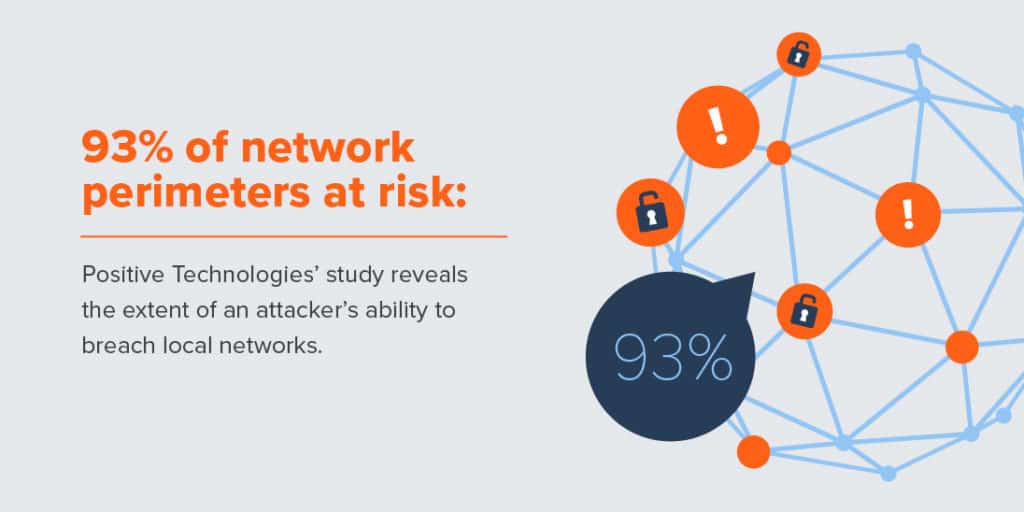
- Network perimeters are at risk 93% of the time (Positive Technologies).
- More than one-third of organizations have seen an uptick in cyber-attacks over 2021 (ISACA). Social engineering, at 14%, remains their biggest concern.
- The retail sector loses $38,052 every minute from cybercrime, while healthcare organizations spend $13 a minute on data breaches (RiskIQ).
What about patterns for different types of attacks, sensitive data breaches, and information security concerns? They have a lot to teach us about the forces arrayed against you.
Phishing
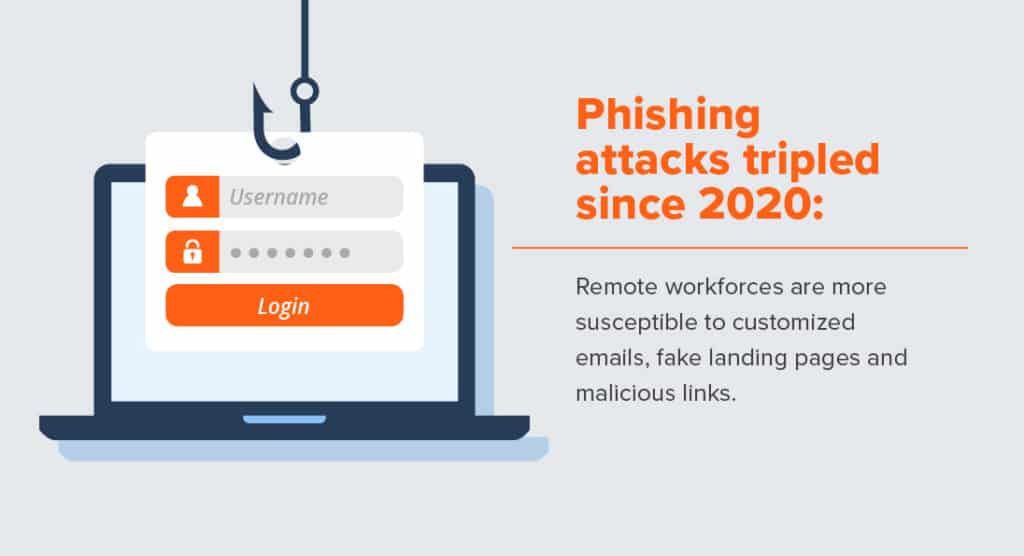
- The number of phishing attacks has tripled compared to 2020 (APWG). Cybercriminals are more likely to use customized emails, dangerous links, and other methods that fool your teams into handing the keys over.
- The most common topics for a phishing attack are by far related to business, e.g., purchase orders, invoices, and shared files (KnowBe4).
- 82% of employees take 0-59 minutes to flag a phishing email (Cofense). Only 9%, however, sit on something suspicious for more than half an hour.
- Attackers are most likely to phish for credentials – 57% compared to 12% for malware delivery (Cofense). Startlingly, 45% of phishing attempts are now themed around Microsoft.
- The biggest phishing targets in Q4 2021 were SaaS and webmail companies at 19.5%, just trailed by retail and ecommerce at 17.3% (APWG).
Remote access
- 50% of breaches are down to insecure remote access and web applications (Verizon). Verizon’s 2022 Data Breach Investigations Report was very clear about the cost of stale passwords, stolen credentials, severe malware, and open back doors.
- Since the pandemic began, 20% of business leaders have borne the effects of a data breach caused by a remote worker (Malwarebytes Labs).
- 26% of security professionals don’t have an automated tool to spot and stop endpoint attacks (Check Point).
Ransomware
- Ransomware attacks increased by 13% this year, more than the last five years combined (Verizon).
- When it comes to ransomware demands, we’re seeing huge inflation. The average payment from significant attacks grew fivefold to over $812,000 from 2020 to 2021. Meanwhile, there was a threefold increase in organizations paying more than $1 million for a single ransom (Sophos).
- Global ransomware damage costs are predicted to grow at an extraordinary rate: $256 billion annually by 2031, based on 30% yearly growth (Cybersecurity Ventures).
- Financial services still rate ransomware their #1 information security threat (IBM). However, it’s showing a 9% year-on-year decrease for cybersecurity risk.
- Saudi Arabia, Turkey, and China hold first, second, and third place respectively for countries suffering ransom demands (Safety Detectives).
DDoS
- Q1 of 2022 witnessed more application-layer attacks than any other period in the preceding 12 months (Cloudflare).
- DDoS interruption costs US companies $218,000 on average, before we factor ransomware demands (Corero).
- One of the longest DDoS attacks early in 2022 lasted for an incredible 549 hours (Kaspersky).
- The telecoms industry has been struck by the most network-layer assaults (Cloudflare).
What’s Behind the Numbers?
Finding these cybersecurity statistics is one thing, but digging past them is quite another. We must try to understand trends as best we can to stay a few steps ahead of anyone looking to harm you.
Aside from the political instability and remote working behaviors we mentioned at the start of this piece, the simple fact is that ransomware attacks – huge ones – have been successful.
Payouts are getting more substantial
Let’s take another example from the supply chain: The Colonial Pipeline Co. hack. On April 29th, 2021, cybercriminals pierced the network of the U.S.’ largest fuel pipeline. A single password leaked on the dark web; that’s all it took to bring down a company that had been on top of its sector for 57 years. A week later, a note appeared on a screen, demanding cryptocurrency. The hackers held the whole East Coast hostage. Colonial had no choice but to shut off the gas. Per Bloomberg, Chief Executive Officer Joseph Blount says their hands were tied: “It was absolutely the right thing to do. At that time, we had no idea who was attacking us or what their motives were.”
The eventual cost of the hack? $4.4 million. Not only was the gas supply plugged, but 100 gigabytes of sensitive data were on the line. Colonial couldn’t risk it all. And when we gaze from this case to other front-page cybersecurity breaches, there’s no wonder ransomware is on the rise. It’s effective. It inspires assaults on even grander scales.
IoT devices are spreading
Smartphones and laptops are merely the core of connectivity for a modern organization. Tablets, trackers, sensors, wearables, and autonomous equipment are broadening the reach and complexity of data transfer, helping the Internet of Things meet its potential. But just as the cloud itself carries more security pressures, so do IoT devices make the business of policing your network that much harder. You may not know how users interact with their devices, and how behaviors from one may impact another in myriad ways.
According to IoT Analytics’ Spring 2022 report, global IoT connections expanded by 8% in the last 12 months, totaling 12.2 billion active endpoints. Hackers are well aware of it. Anything that uses an app – from connected printers to coffee machines – is vulnerable to attack. When we consider the evolving insidiousness of cybercrime, we must think beyond common screens and smart devices. Online safety should grow with the solutions you’re using for faster, more convenient tasks and insights.
Social media phishing is getting worse
You may have come across terms such as ‘spear phishing’ and ‘whaling,’ which are well-circulated in cybersecurity. However, more scammers are using social media to collect sensitive data. They might set up a clone account for a real company and hide a malicious link on a webpage. Or instead, they can imitate a recruiter on LinkedIn, tempting a victim with an unmissable role. There’s so much more to be wary of in 2022, when traditional phishing attempts are probably a cornerstone of your information security training.
That’s why it’s vital to research social phishing tactics and update your guidance. Educate employees on legitimacy: whether an account has plenty of followers, for instance, or the fact that no one should message them on LinkedIn for login details.
It’s easy to feel overwhelmed by everything under the microscope. Yet with advanced threat detection and a MDR solution, you’ll cut past the fear, straight to the best protection you can find. Speak to the Alert Logic team today for 24/7 cybersecurity.