Cyber threats are on the rise. More businesses have moved their operations online, and hackers are fine-tuning their capabilities to breach even the tightest security operation. All of this necessitates adopting highly sophisticated threat detection and response procedures to protect against these cyber threats and safeguard critical systems.
SOAR (security orchestration, automation and response) security tools are some of the cybersecurity industry’s most effective solutions. Automation and orchestration are at the heart of SOAR capabilities, enabling SOC teams to streamline their most time-intensive tasks to optimize response efficiency and craft more effective approaches to any potential threat facing their organizations.
What is SOAR and Why Is It Important?
A SOAR solution employs automation, orchestration, artificial intelligence/machine learning, and other analytical tools to enable organizations to centralize critical information about any potential threat facing their systems and create fast, efficient, and effective responses to them.
The efficiencies gained from automated response allow organizations to decrease their mean time to respond (MTTR) to security incidence, which helps reduce the potential impact of a security incident.
Why is SOAR Security Important?
Implementing SOAR technology helps strengthen your security posture, which is critical in the current cybersecurity landscape as threats have grown exponentially in recent years. As organizations continue to digitize their operations and move more of their activity online, new attack vectors have been created, giving hackers more openings to exploit.
The risk of a security incident is severe. Cybersecurity attacks can create a host of problems for organizations, financial loss chief among them. Sophos found that organizations subject to ransomware attacks paid an average of $1.54 million in 2023 almost doubling from $812,380 in 2022. It doesn’t end there. Beyond the financial damage, cybersecurity incidents also can lead to:
- Loss of consumer trust
- Damage to brand reputation
- Permanent data loss
- Slowed business operations
Equipping security systems with the most advanced software is critical to limiting exposure and preventing damage from taking place.
The Key Features of SOAR
A SOAR platform is grounded in the same three core components that constitute the SOAR acronym. These are:
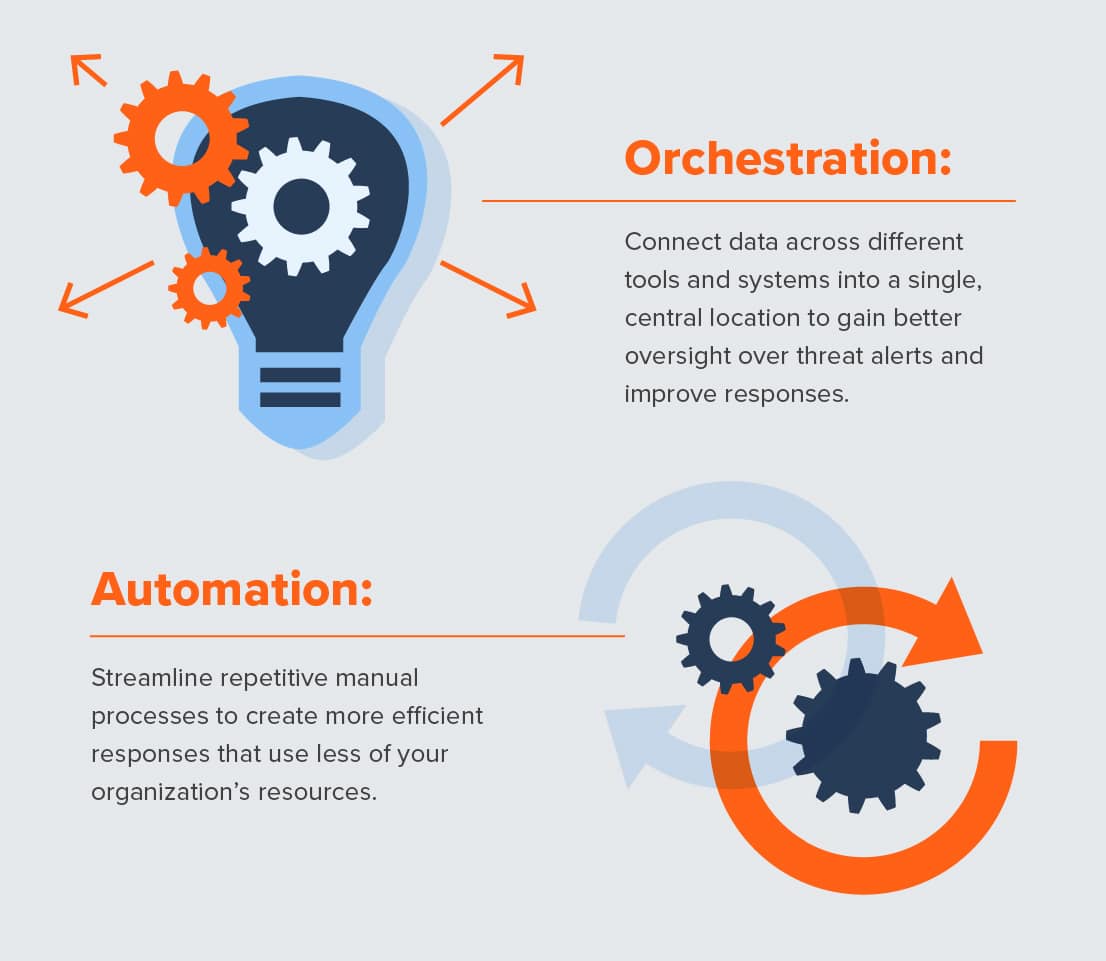
Security orchestration
API-driven platforms connect security data from disparate tools and systems into a central location. This gives the security team greater oversight and access to conduct threat analysis.
Security automation
Orchestration means more data for security personnel to collate. Backed by artificial intelligence, a SOAR platform optimizes an organization’s threat data by automating core processes like vulnerability scanning and log analysis. This creates more efficient responses that use less of an organization’s resources.
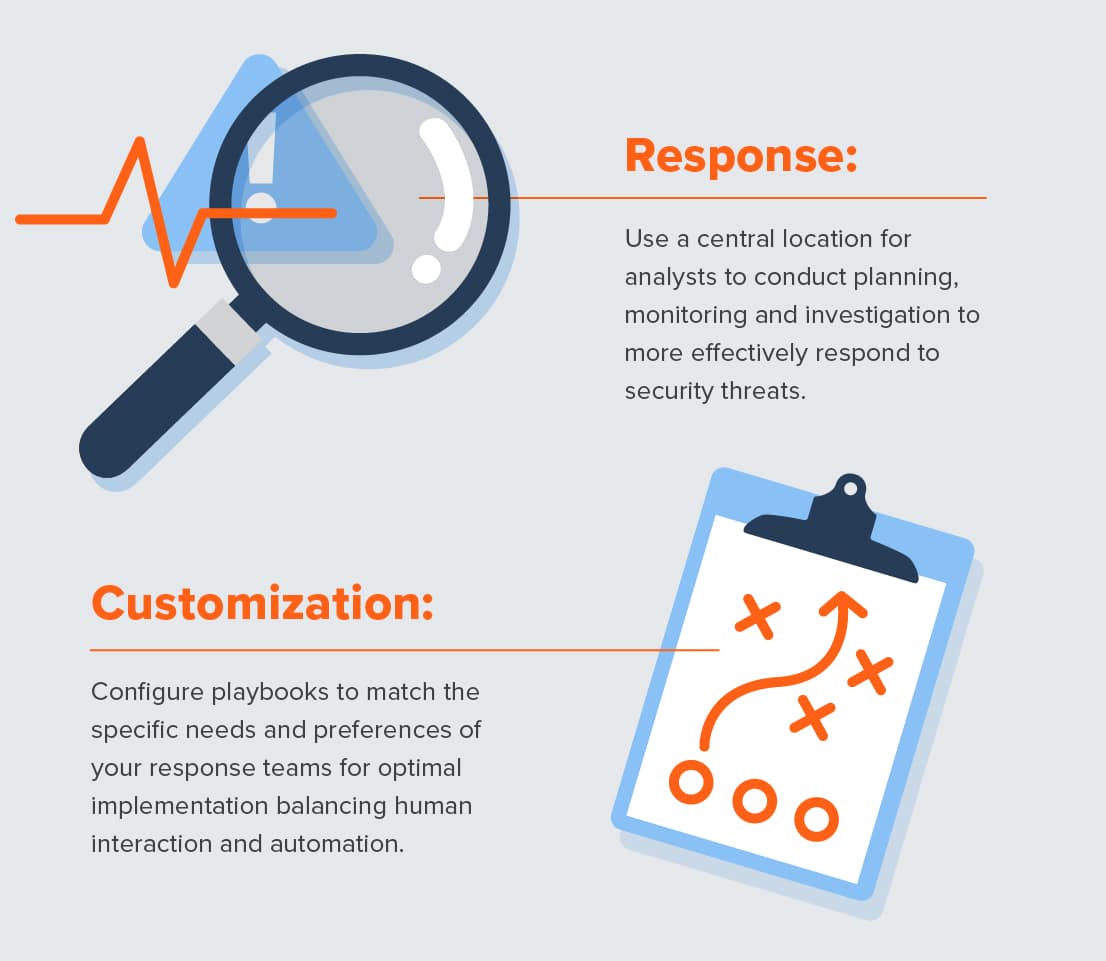
Security response
Many standard security response activities are automated by SOAR technology. This means even this stage of the process doesn’t require full human intervention. For incidents that do, a SOAR system provides a central location for analysts to conduct planning, monitoring, and investigation of security alerts to build their response.
How SOAR Security Can Benefit an Organization
As cybersecurity threats become a greater priority for organizations, there is an acute need to unite disparate security information into a single location to consolidate all threat data and coordinate responses. Here are some of the top ways organizations can benefit from SOAR software:
Cost savings
One of the main benefits of SOAR security is the cost-savings opportunity. Automation and orchestration reduce the amount of time security personnel spend on repetitive tasks. This saves organizations huge amounts of resources they can devote to other areas of their business.
Streamline operations
SOAR automates many time-consuming administrative tasks commonly associated with security assessment and response. By drastically reducing the amount of time every security analyst spends on mundane manual processes, organizations redirect their teams’ focus to more involved threat response procedures. It also empowers analysts to take preapproved response actions in confidence.
Faster security incident response
Cybersecurity threats are constantly evolving and becoming better able to breach security infrastructure and penetrate critical systems. Timely incident response is an essential component of effective security systems. Automation and orchestration give SOC teams the resources to reduce their MTTR, enabling them to craft appropriate remediation plans before attackers can cause damage. It also allows responses to be taken outside of working hours if organizations do not have a 24/7 response team.
Better threat response
A security system is ultimately judged by how effectively it detects potential threats and facilitates responses to them. A SOAR tool enables organizations to build a complete overview of the security threat landscape. Additionally, you develop coordinated approaches that minimize mistakes, maximize timeliness, and ultimately leverage security resources in the most efficient way possible.
Organizations today are much more likely to experience a security event, meaning they have to prioritize cybersecurity to protect their critical systems, networks and processes from long-term damage. However, knowing where to start can be a daunting task for many executives.
With Fortra’s Alert Logic managed detection and response (MDR), your organization’s security will be strengthened by our SOAR tool, Alert Logic Intelligent Response. Intelligent Response enables organizations to minimize the impact of a breach before damage occurs. It prevents the lateral movement of a cyberattack, disrupts reconnaissance by blocking the attacker, and disables compromised credentials.
Ready to learn more? Schedule a demo today.