Unrivaled Security for Any Environment
24/7
Security Monitoring
120+
Expert SOC Analysts
20+ years
Cybersecurity Experience
Cybersecurity Made Easy
Reach your defined security outcomes with our industry-leading SaaS-enabled MDR, XDR, and WAF solutions. Experience round-the-clock security expertise, unparalleled threat intelligence, and extensive coverage across any environments.
- The Most Comprehensive Detection
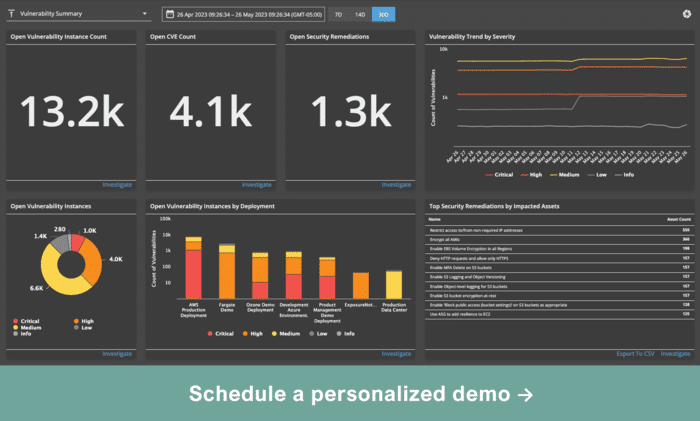
& Response CoverageFortra’s Alert Logic MDR and XDR solutions offer comprehensive visibility across public cloud, hybrid, and on-premises environments. Gain vital insights into your security posture and detect and respond to potential threats to safeguard your business.
- Web App and API Protection
Fortra Managed WAF delivers a robust solution designed to thwart web app and API attacks through advanced threat protection, optimized by our security experts.
- Compliance Simplified
Our solutions empower and accelerate your security
compliance processes. - 24/7 Security Operations Center Expertise
Our global SOC is on the forefront of our customers’ defense, providing expertise that measurably improves security posture.
- Exceptional Threat Intelligence
Enhance your defense against evolving threats in today’s changing landscape with our proven technology, advanced analytics, and expert-guided response.
Your Trusted AWS Partner
Since 2011, Alert Logic has been an AWS Partner, pioneering security ISVs responsible for protecting AWS customer workloads. For more than 10 years, our strategic relationship with AWS has flourished as we consistently deliver measurable service value to customers.
As an inaugural member of the Amazon Partner Network (APN) and participant in the ISV Accelerate Program, Alert Logic is a security category leader in co-launched AWS initiatives. We are proud to be an AWS Level 1 Managed Security Service Provider (MSSP) with specialization designations in Modern Compute and Digital Forensics & Incident Response as well as AWS Security competencies, integration, and launch partners for AWS WAF, Amazon GuardDuty, AWS Control Tower, AWS CloudTrail, AWS Container deployment, and many others.
A Key Part of Fortra
Alert Logic is proud to be part of Fortra’s comprehensive cybersecurity portfolio. Fortra simplifies today’s complex cybersecurity landscape by bringing complementary products together to solve problems in innovative ways. These integrated, scalable solutions address the fast-changing challenges you face in safeguarding your organization. With the help of the powerful protection from Alert Logic and others, Fortra is your relentless ally, here for you every step of the way throughout your cybersecurity journey.
Award-Winning
Cybersecurity Expertise & Solutions



See Why Security Leaders Choose Alert Logic
Blog
Latest from Alert Logic
Navigating the World of Security as a Service
Thinking of partnering with a Security as a Service (SECaaS) provider? Here’s what you need to know.
XDR vs. Antivirus: Understanding the Key Differences
Discover the critical disparities between Extended Detection and Response (XDR) and antivirus solutions in our latest blog. Explore their functionalities, capabilities, and effectiveness against modern cyber threats to empower informed security decisions for your organization.
The 12 PCI DSS Compliance Requirements
Are you ready for PCI DSS 4.0? Gain insight into the PCI DSS requirements to safeguard sensitive data throughout its lifecycle, ensuring robust protection for organizations in handling data collection, storage, transmission, and processing.
Ready to Protect Your Business with Alert Logic?
MANAGED DETECTION AND RESPONSE
Delivering peace of mind from threats by combining 24/7 SaaS security with visibility and detection coverage wherever your systems reside.
EXTENDED DETECTION AND RESPONSE
MANAGED WEB APPLICATION FIREWALL
Block attacks targeted at your web applications and APIs with advanced threat protection, optimized by our team of web security experts.