Introduction
Over the last several years, broad public cloud adoption has exploded. One of the main reasons for this is the need for increased flexibility for organizations (e.g., ability to deploy software remotely, bring new environments online more quickly, and have them more accessible in public cloud environments).
Multi-cloud adoption also can be the natural result of your cloud journey. As your organization adapts, grows, and business requirements change, adopting more than one public cloud may be necessary to help you reach the performance, scale, redundancy, and reliability goals of your cloud environment.
This guide was created to help you:
- Understand the drivers for multi-cloud adoption
- Identify key challenges you may encounter in creating your multi-cloud strategy
- Use best practices for adopting and implementing a multi-cloud strategy
- Become aware of key security considerations that impact multi-cloud adoption
Multi-Cloud Drivers
For mid-size businesses, there are three primary drivers for multi-cloud adoption:
- Cost optimization: Most mid-sized organizations are already leveraging multiple cloud vendors to support different areas of their business (e.g., Active Directory for IT, O365 for remote working, AWS for DevOps teams). A multi-cloud strategy can be the fastest, least resistant path without significantly impacting the budget. Cost-savings benefits can be experienced when shifting from on-premises to public cloud or hybrid infrastructure to address needs for resiliency, space, and backup.
- Application or licensing affinity: It comes as no surprise that people are comfortable with the types of applications with which they typically work. Some work better within specific public cloud environments (e.g., Microsoft for database users, AWS for DevOps). This familiarity can drive organizations to move to multi-cloud. Additionally, license portability may be another factor as cost versus refactoring is evaluated, with a goal of finding the most cost-effective solution.
- Delivery model adaptation: Organizations looking to scale may need to adjust their delivery model to accommodate anticipated growth.
“89% of respondents reported having a multi-cloud strategy with
76% of organizations utilizing two or more cloud providers.”
4 Key Multi-cloud Challenges
Security: There are two primary reasons for this challenge:
- Often, security gets bolted on at the end the process.
- The assumption is adopted that native security controls for point products and tools will suffice. In reality, they lack the underlying security coverage needed to operate and manage the entire environment.
Inconsistencies between cloud service providers (CSP): Each CSP has a distinct set of tiers and requires a contract. The differences between each CSP’s tiers, applications, and services can contribute to inconsistency from a management, cost, and operational perspective.
You already are multi-cloud and just don’t know it: Operating a remote workforce results in a heavy use
of cloud applications for employees to get their jobs done. It also means individual employees are likely using several unsanctioned cloud applications or that project teams have adopted cloud services without notifying necessary stakeholders, thus driving a multi-cloud approach without a strategy in place to establish guidelines and controls.
Talent shortages: Identifying and maintaining the right talent with the right skillset is no easy task. In a recent report, 44% of respondents indicated lack of qualified staff is the biggest operational headache when protecting workloads.1 Having a cloud architect’s perspective on the design, implementation, and deployment of your cloud is ideal but can be costly and in high demand.
“Overall, 85% of respondents indicated that security is a top cloud challenge, followed by 83% for lack of resources/expertise, and 81% for managing cloud spend.”
2022 Flexera State of the Cloud Report
“Overall, 85% of respondents indicated that security is a top cloud challenge, followed by 83% for lack of resources/expertise, and 81% for managing cloud spend.”
Getting Started on Multi-cloud Adoption
Early in your planning process, make sure to address these four areas:
Define a clear strategy: The omission of a strategy is a deal breaker for multi-cloud adoption. Without a clear strategy, the adoption process can quickly be derailed or set up for failure.
Don’t forget about security: Unfortunately, security continues to be addressed at the tail end of deployment, much too late in the conversation — contributing to hurdles (e.g., project delays, costly add-ons, vulnerabilities) as additional public clouds are adopted. Organizations do not have the luxury to ignore security. As ransomware attacks increase, cybercriminals become more sophisticated and a larger remote workforce demands that organizations make security a top priority.
Understand the drivers: While every organization is different, there are similar drivers for multi-cloud adoption across mid-size organizations. These drivers may impact the business objectives, the strategy defined, and the cloud provider that ultimately is adopted. As such, being clear on the drivers can help organizations focus attention on achieving their objectives to deliver desired outcomes.
Involve the appropriate stakeholders: Adopting multi-cloud is not just an IT or security decision. There are dependencies between the two groups that will directly impact the ability to successfully (or unsuccessfully) deploy your multi-cloud environment. Engaging multiple stakeholders — including IT, security, C-level, and operations — ensures you’re addressing the business requirements and desired outcomes that drive your organization.
2 Minute Cloud Security Assessment
Answer a few of short questions to understand your cloud security gaps and identify what is needed to move forward.
Best Practices for Secure Multi-Cloud Adoption
Follow these set of principles to ensure your strategy and approach are secure.
Prioritize security: This has been mentioned several times but cannot be overstated: Security must be central to the design of your multi-cloud strategy. It is the single most critical element with the potential to impact every aspect of your multi-cloud adoption — from cost and resources to execution timelines and long-term sustainability.
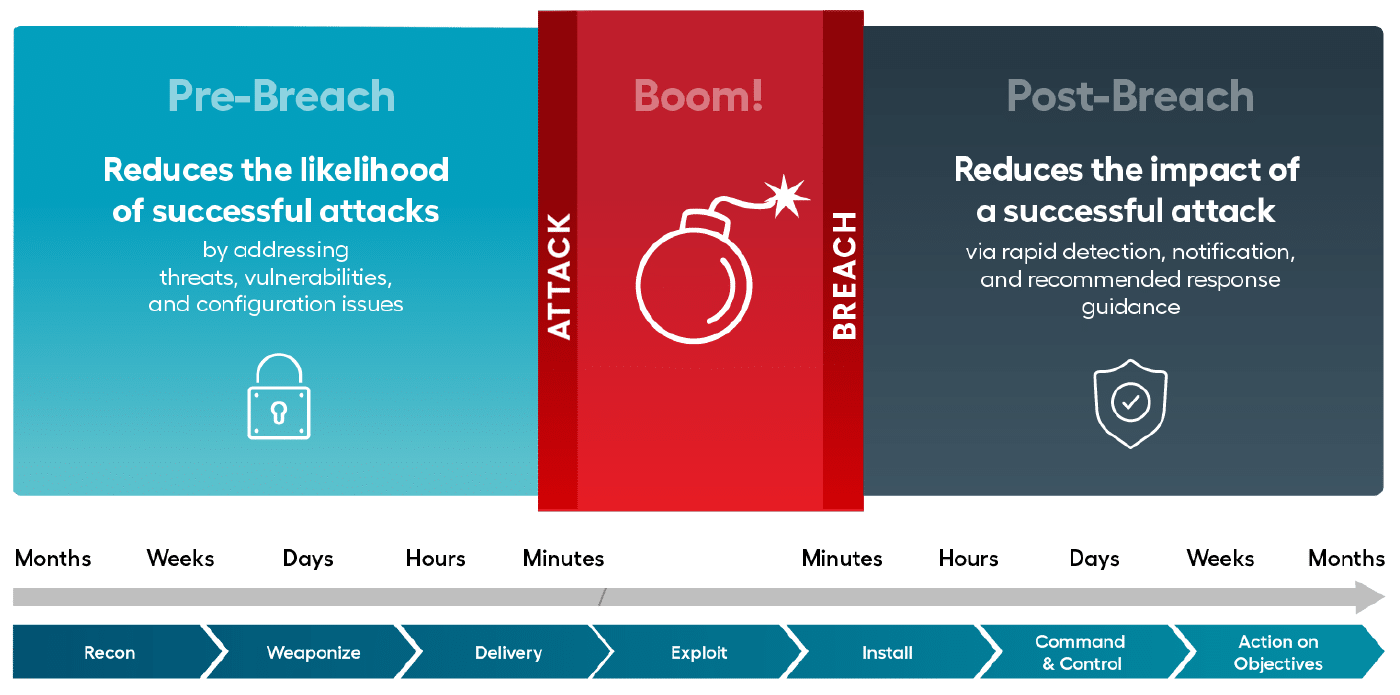
Address pre- and post-breach security: Most organizations adequately address pre-breach security but tend to de-emphasize post-breach security:
- Pre-breachfocuses on having visibility to and an understanding of what is happening in your environment, then building on it to harden your posture and minimize risk. Vulnerabilities do not always happen in the places you would expect. The ability to scan across the environment to identify vulnerabilities is imperative. Most often, human error or oversight (e.g., a misconfiguration, lack of appropriate access controls in place) are the cause of pre-breach compromises
- Post-breach focuses on reducing the amount of time that a breach is successful to minimize its impact. It is a sobering realization that your preventive technologies will fail at some point, especially if you’re dealing with unknown threats. You cannot stop what you do not know.
Ask the right question
As you approach the security element of your strategy, it is important to note the conversation around the strategy has shifted. Historically, discussions have centered around the question: How do you secure the cloud? As cloud environments have become more complex and dynamic, the conversation has shifted to an application-centric discussion with the central question being: How do you secure each application wherever it is hosted?
Be prepared
You must address pre- and post-breach security because attacks do not happen all at once. It can take weeks or months to identify a breach; according to a recent report, on average, it takes 278 days to identify and contain a data breach.2 Your goal should be to reduce the likelihood of a breach (where possible) and detect breaches as quickly as possible when they do occur to minimize harm to your assets and environment.
Ensuring Visibility
For 40% of organizations, lack of visibility is one of their biggest cloud security concerns.3 To effectively address it, you need a single pane of glass view of your entire environment. Additionally, visibility should extend to discovery as you can’t protect what you can’t see. Visibility should include the ability to perform vulnerability scanning, and asset and workload discovery, regardless of IS platform. Ideally, this should be done via a consolidated view.
The reality is that most providers lack the ability to view and monitor your environment in one place. Fortunately, Fortra’s Alert Logic Managed Detection and Response® (MDR) enables you to pull logs, data, and activity across public and hybrid environments. With a comprehensive view of threat activity, Alert Logic MDR provides 24/7 security monitoring and dedicated security experts to help prioritize where you and your team focus your attention when it comes to security threats.
Securing Known and Unknown Threats
Known threats are predictable because you can implement preventive measures — such as proper configurations, patching, and known ransomware — to minimize the potential for a breach. Unknown threats require threat intelligence and research to proactively gather insights on the threat behavior, understand what is happening with other companies, and create an analytic rule to detect against this. It allows you to hunt for this behavior and scan to minimize post-breach impact if/when the vulnerability is exploited.
The reality is many vendors can address known threats; it is significantly more complex to address unknown threats and not all vendors have the team to do so. Having a highly skilled Security Operations Center (SOC) (such as Alert Logic’s SOC) that conducts data analysis and threat hunting to proactively warn customers with recommendations on how to respond and offer remediation steps to address these unknown threats is key.
Maintaining Controls & Processes
In any cloud environment, maintaining visibility across all applicable environments is a must. Establishing and implementing controls in the environment also is crucial. However, consistently monitoring adherence to those policies, such as identifying when workarounds are attempted and/or successfully executed, is equally important.
“A majority of organizations (70%) rate their security readiness
as average or below average.”
Key Considerations
In addition to the aforementioned best practices, there are several key considerations to keep in mind as you build your multi-cloud strategy. Each represents critical elements to incorporate into your strategy.
Shared Security Responsibilities: When it comes to the shared security responsibility model (SSRM), the obligations of the cloud provider and organization are well defined. When working in one cloud environment, it is clear how to manage your responsibilities; the challenge increases when you are working in a second or multiple cloud environments. An organization’s confidence of achieving SSRM for different cloud services may differ. Consider:
- The impact of adopting a new delivery model — you may need to adapt your approach to each public cloud provider
- The maturity levels for each public cloud provide
- Building your in-house expertise through a cloud architect or dedicated training
- Leveraging a third-party service to assist with ensuring adherence to shared responsibility requirements
More Tools Do Not Equal Easier or Better
It should come as no surprise that there are numerous tools when it comes to multi-cloud. For example, each public cloud vendor has a portfolio of tools. There are also many tools on the market designed for specific functions and capabilities but require a significant effort to get the same level of information and insights across all of them. More tools translate to more raw data — if you cannot interpret and act on that data, then you have not addressed your original problem. Consider a single tool or service that gives you visibility across your entire IT estate for a more comprehensive view of your environment.
If you’re like the 63% of organizations using native cloud provider security tools4 to provide coverage, do you know these tools may not be providing sufficient security for your organization? While they are designed to provide security for their respective cloud environments, that coverage does not necessarily extend to other public cloud providers. If you’re building a multi-cloud strategy, you will need to incorporate other services and/or tools to close the security gap.
Role of People & Processes
People, process, and tools are the trifecta to tackling any cloud environment. Each plays a critical role in ensuring the security of your enterprise. We have already explored tools, now let’s dive into people and process.
People: Identifying and maintaining the right talent with the necessary skill set is no easy task. Having a cloud architect’s perspective on the design, implementation, and deployment of your cloud is ideal but can be costly since these professionals are in high demand. Be realistic about your ability to operate and manage at the skill and process levels required for your environment.
Additionally, ask yourself if you have the existing people resources to maintain and can get the most out of your cloud environments. Your processes and controls will help, but you need resources to monitor, identify, and respond to threats that may affect your environment. Third-party services and expertise are a great option to fill this gap and providers ranging from EDR, XDR, and MDR are plentiful. When considering what service is ideal, look for a provider that checks all the boxes of your multi-cloud strategy (e.g., pre- and post-breach coverage, a single platform to help reduce the burden of secured shared responsibility, etc.).
Process: Security has become both a top priority and mandatory element of how many organizations build their cloud and IT processes. For some organizations, security teams are more involved with IT, resulting in the transformation of traditional roles and interactions.
When security and IT teams work closely together, teams are better informed on processes such as patching schedules, DevOp cycles, and processing of employee separation. In many cases, security teams now have a seat at the table when it comes to influencing traditional IT processes and areas of ownership. As a result, changes are made to pro-cesses to incorporate aspects such as security. Checks and balances then are integrated to ensure avoidable mistakes — such as misconfigurations, granting too much access, or not performing regular patching — are not overlooked.
Do NOT Do It Alone
Some mid-sized organizations are mature in one public cloud environment and can execute effectively in that environment but are resource or skills lacking in a second public cloud. For these organizations, it is important to evaluate if you have the internal resources that can be developed to learn and manage the different services of various public cloud providers.
Ask yourself how long it will take and how much expertise can your current resources acquire in the timeframe you have. With that information, does it make more sense to partner with a provider that can cover the shifts and leverage the collective expertise to manage and maintain a second or multiple cloud environment’s complexities? If the latter is a better fit for your organization, Fortra’s Alert Logic is the answer. Take advantage of Alert Logic’s team of cloud and security experts to gain 24/7 threat detection and response across your entire multi-cloud environment.
Rely on Fortra’s Alert Logic
As the industry’s first SaaS enablement managed, detection, and response provider, Fortra’s Alert Logic has unparalleled coverage for any environment — protecting your most critical assets with purpose-built technology and security expertise to strengthen your security posture.
To learn more about managing shared responsibilities in a multi-cloud environment, check out our guide on Key Steps in Defining a Shared Responsibility Model for Public Cloud Environments. Take our 2-minute Cloud Security Assessment to understand your cloud security gaps.
- ISC2 2022 Cloud Security Report
- 2021 Ponemon Cost of a Data Breach Report
- 2021 Flexera State of the Cloud
- ISC2 2022 Cloud Security Report