Today’s Attacks Leverage
Multiple Techniques
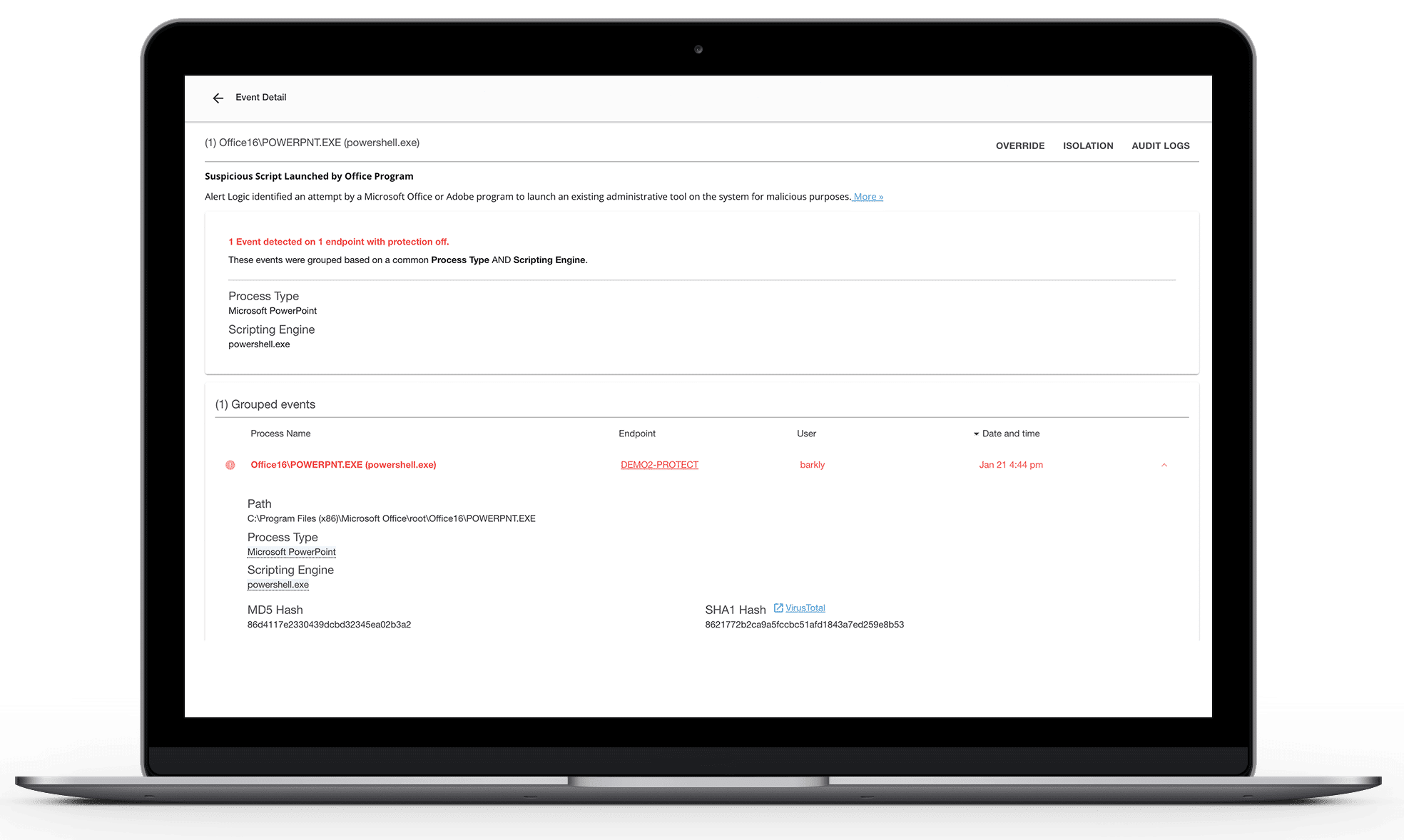
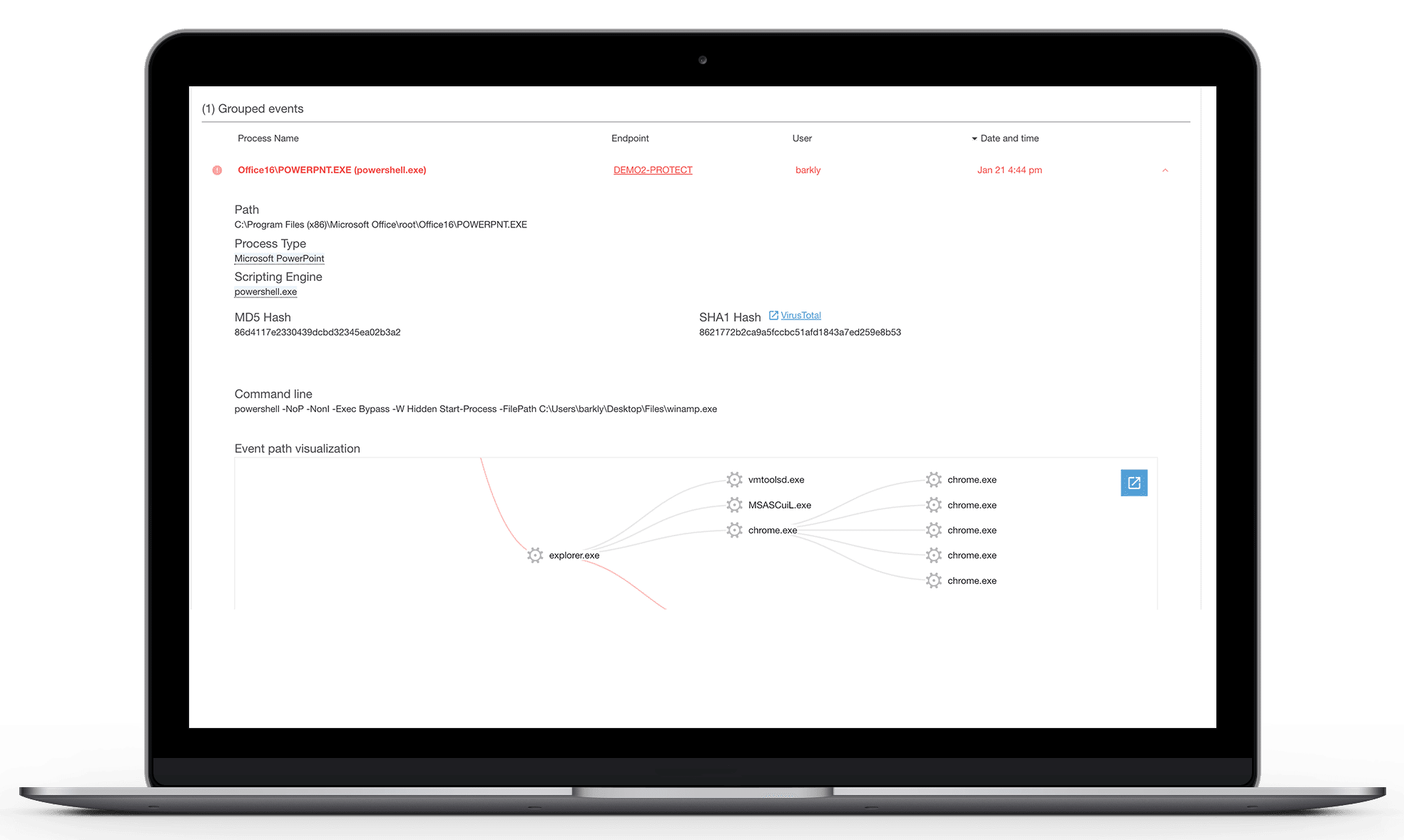
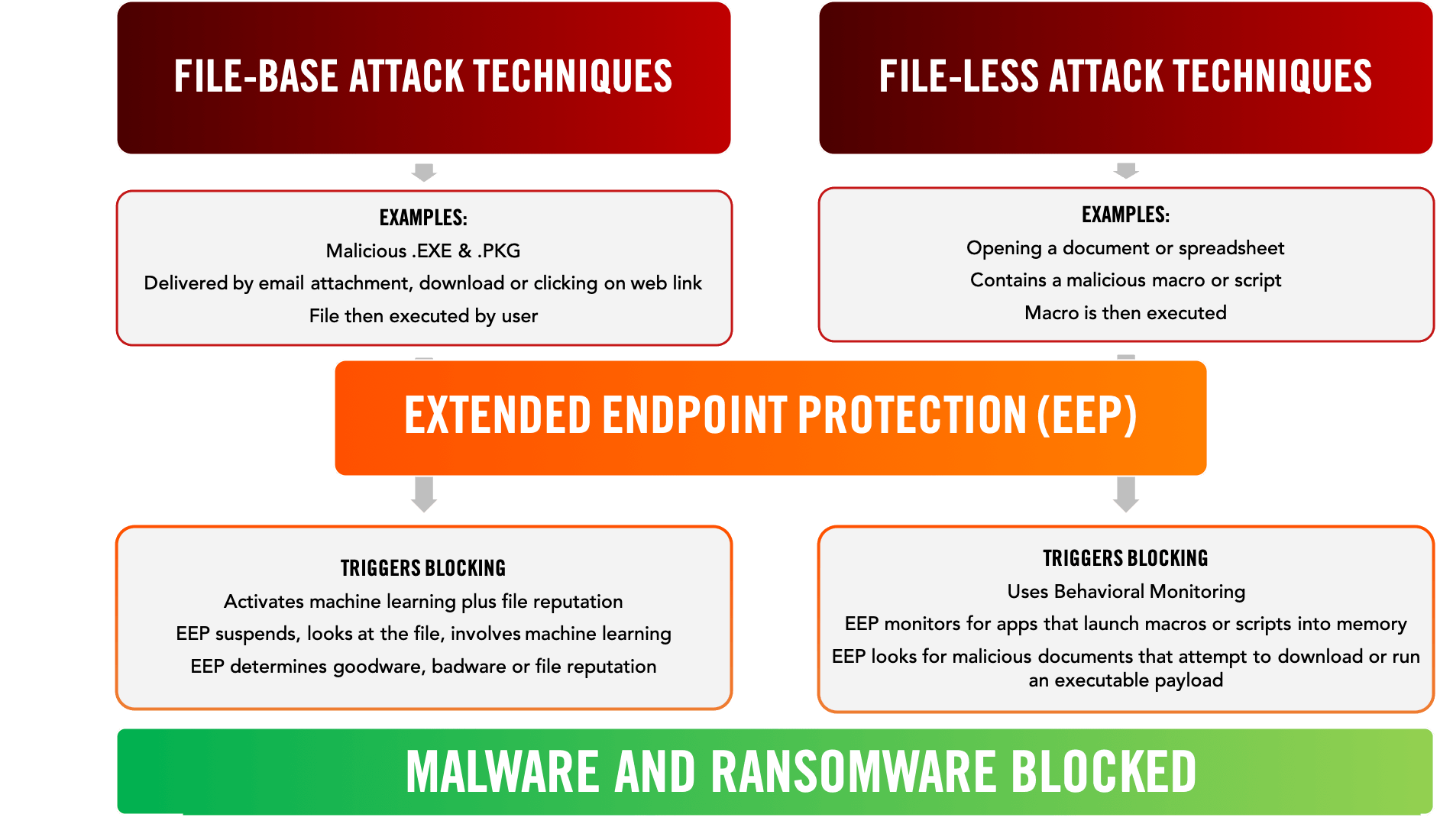
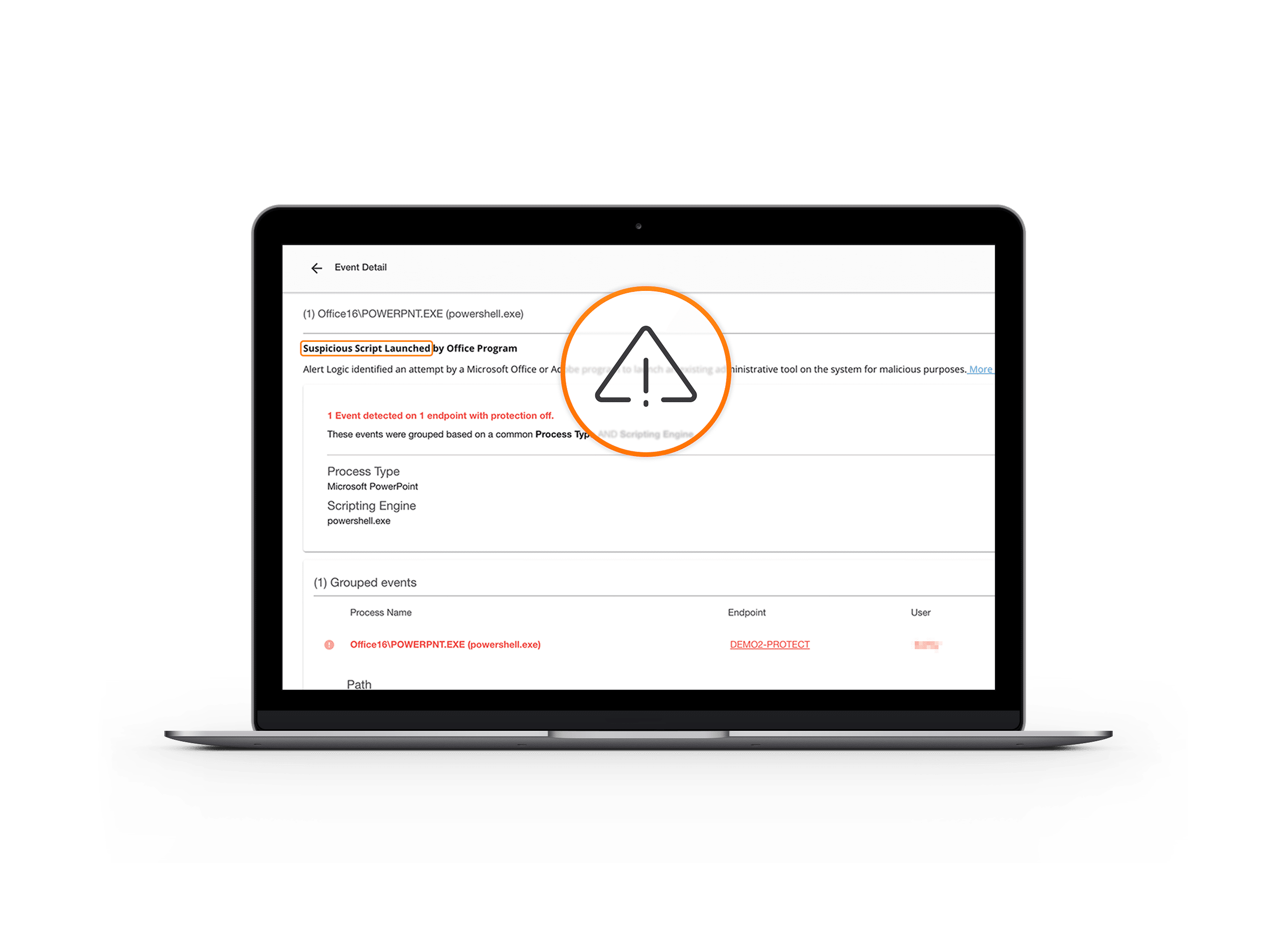
Attackers try to get on the endpoint, gain access to resources, and detonate their payloads. Endpoint detection helps thwart multiple attack techniques that try to compromise Windows and macOS endpoints. Our multi-vector attack monitoring and isolation recognizes these techniques and stops them early before any damage is done. Our managed detection and response platform can work alongside of existing antivirus tools to provide an additional layer of defense.
Alert Logic Endpoint Security
Protect sensitive data against multiple attack techniques.
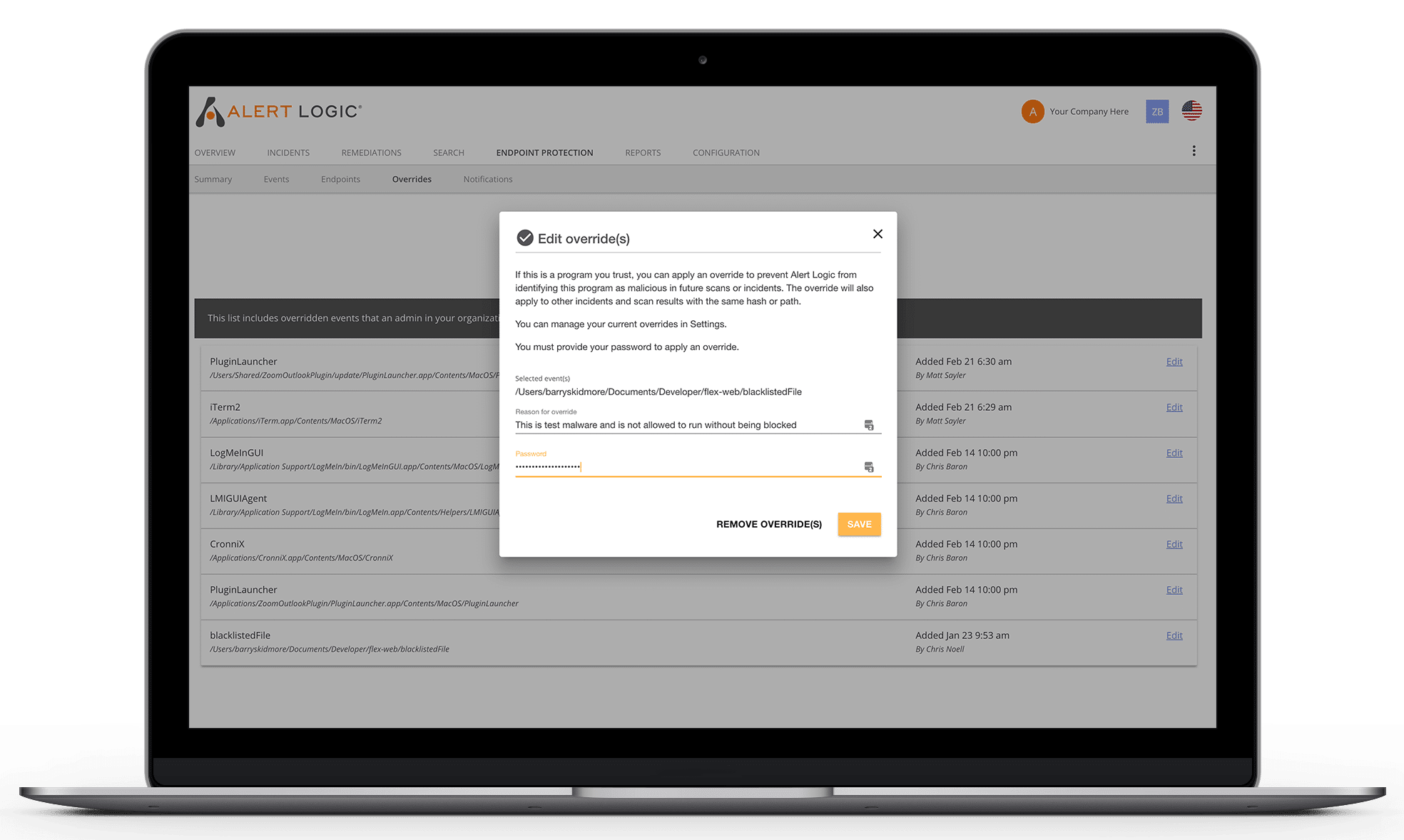
- Use machine learning to stay ahead of attackers and zero-day attacks
- Identify malicious techniques and ransomware in real-time
- Isolate compromised devices
- Gain deep visibility across endpoints
- Cover endpoint devices whether online or offline
- Designed to be fast with low overhead (1% CPU utilization)
- Recognize new threats faster because it is signature-less
Securing Endpoints Using Machine Learning and Analytics
Alert Logic provides coverage for laptops and desktops as a first line of defense against attacks.
You get endpoint security and active blocking capabilities for the following exploitation techniques:
You get endpoint security and active blocking capabilities for the following exploitation techniques:
Alert Logic Solution Benefits
Alert Logic delivers a comprehensive solution that provides asset visibility, vulnerability assessment, threat detection and response, and web application security to provide the right level of coverage at the right cost. We enable broader detection and response with less effort and lower cost.
SECURITY PLATFORM
- Asset discovery
- Extended endpoint protection
- Vulnerability scanning
- Threat monitoring and visibility
- Intrusion detections
- Security analytics
- Log collection and monitoring
- Always-on WAF defense against web attacks
THREAT INTELLIGENCE
- Threat Risk Index
- Verified testing 2.1 million + web application attacks
- Remediation guidance
- Attack prevention capabilities
- Extensive log search capabilities
- User behavior anomaly detection
- Event insights and analysis
- Threat frequency, severity, and status intelligence
- Comprehensive vulnerability library
EXPERT DEFENDERS
- 24/7 SOC with incident management, escalation, and response support
- PCI scanning and ASV support
- Service health monitoring
- Incident response assistance
- Threat hunting
- Help with tuning strategies, customized policies, and best practices
Need to Schedule A Demo?
For the US call 844.816.1051 and for the UK call +44 (0) 203 011 5533