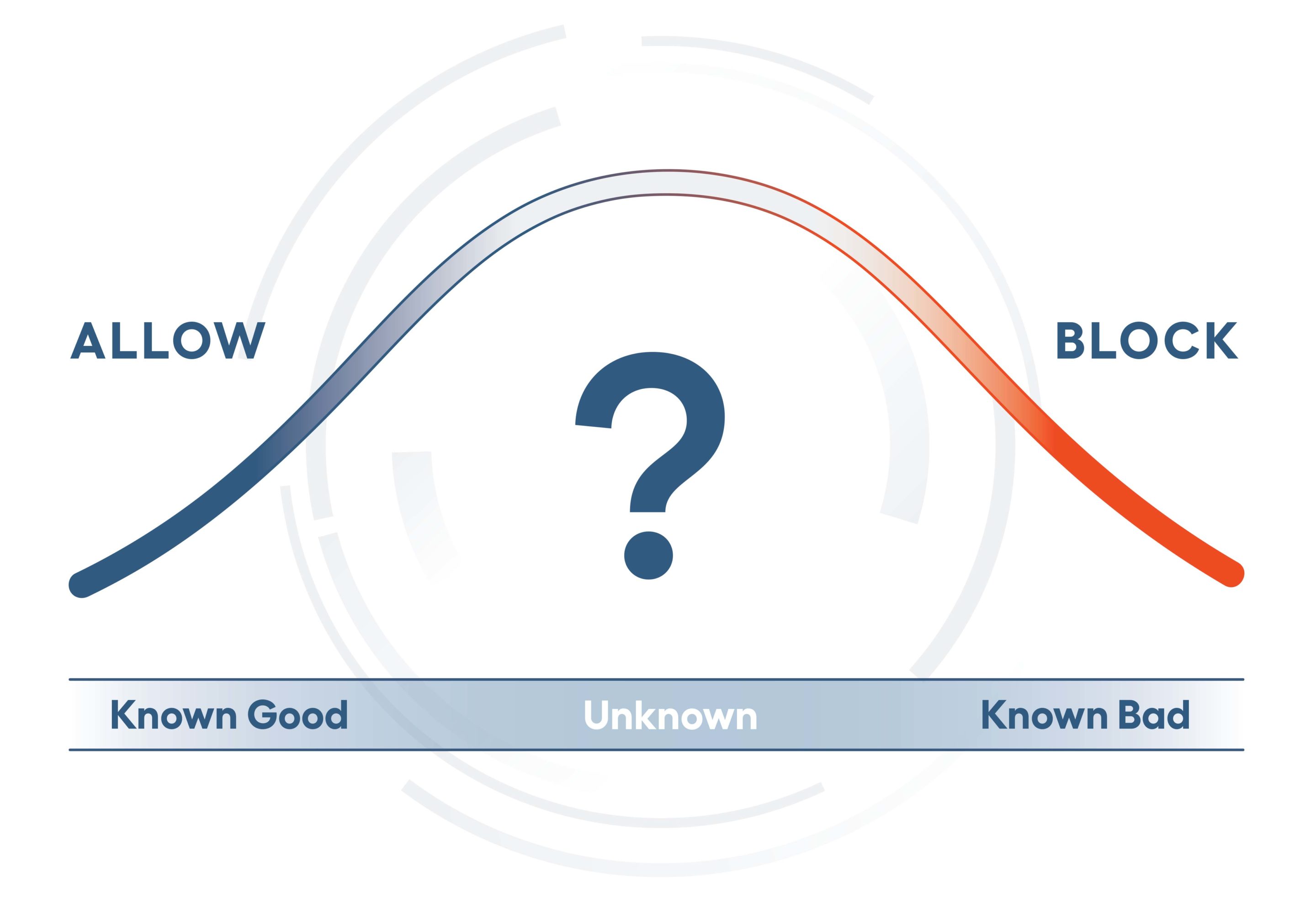
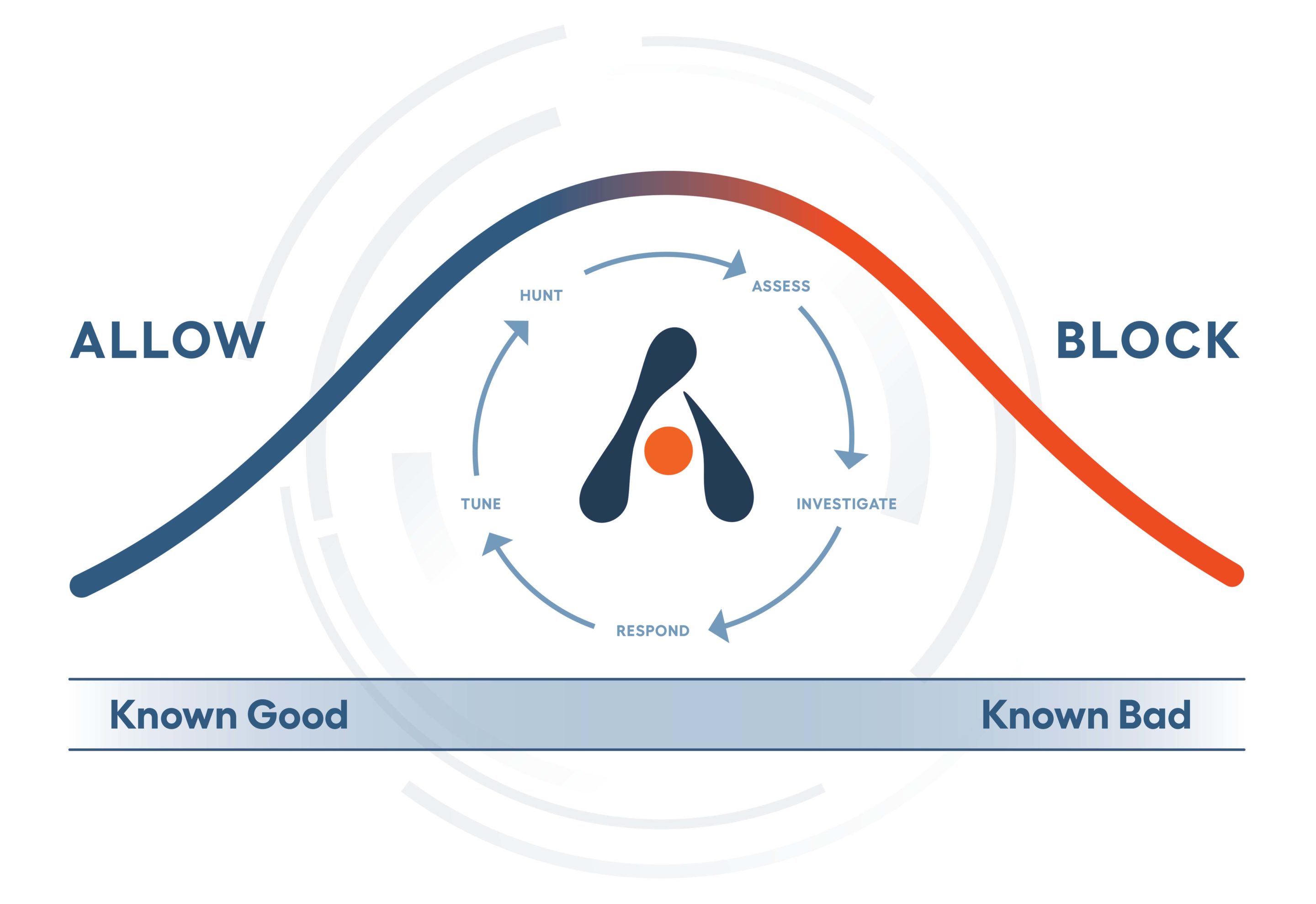
At Alert Logic, our SOC analysts, data scientists, and security researchers continuously hunt for the latest emerging threats and campaigns. This human-led process serves as an essential component to complement automated detection as threat actors adapt and try to evade the latest developments in detection, constantly trying to find a way to operate in the unknown activity that sits between known good and bad.
The Challenge
Throughout this process, we have amassed a wealth of knowledge and understanding of distinctive threat actor groups. Keeping track of the tactics and techniques used has increased our effectiveness and efficiency in identifying emerging campaigns and zero-day exploits, as threat groups tend to favor their own tactics, techniques, and procedures (TTPs). In other words, even when threat groups evolve their campaign by including a shiny new exploit, other TTPs and indicators remain consistent. This way, we know where to look next when we see new activity bearing similarities to previous campaigns, increasing our detection and response times.
All our customers’ benefit, both directly and indirectly, from this process and knowledge. Those targeted receive early warning, and we work with them to remediate the compromise before any real damage can be done. Our broad understanding of persistence mechanisms means we can address the entirety of a compromise and not just the glaring symptom.
Those who have not been targeted directly benefit from the lessons learned from targeted customers, as we document relevant indicators and devise a unified approach to disrupt the campaign and accumulate targeted remediation advice. This indirect benefit is often referred to as “community immunity.”
Human-led threat hunting is an integral part of our security analytics development, both to continuously improve coverage of the ever-expanding attack surface while also eliminating false positives. This approach enables us to detect new signs of compromise in a network manually, while we review the suitability of raised incidents for creating automated detection. This means our customers are covered while we responsibly develop analytics that produce low false positives and low false negatives, meaning we can catch the next occurrence as and when it happens. Over time, we have developed a deep understanding of threat activity clusters that have improved analysis time and informed comprehensive remediation plans.
The Threat Activity Clusters
This series shines a light on some of the great work of our hunters and researchers by sharing threat activity clusters observed in the Alert Logic dataset.
We will share a narrative on the threat activity clusters involved in finding and exploiting zero-day vulnerabilities and those who use novel tactics or techniques in an attempt to circumvent standard breach detection and prevention solutions. While our Threat Intelligence teams subscribe to numerous public and private intelligence feeds, this blog series is Alert Logic’s assessment of threat activity clusters, ultimately based on our unique insight into the 40+ PBs of monthly threat data we collect from our 4,000+ customers.
Naming Convention
As part of our MDR service, we track and combat these threat activity clusters daily, and our experts wanted to give them a suitably un-intimidating identifier. As well as being fun, ice cream flavors allow us to group related and evolved campaigns with iterations of documented flavors.
For example, the Vanilla group may disappear into temporary obscurity, re-emerging with recycled IP addresses and new techniques, but still including common indicators from their previous campaign. In this case, we can be confident that they are one and the same, or at least linked. Where the evolution is significant enough, we can refer to this “new” campaign as Vanilla with Sprinkles. A superficial difference that changes how they operate and how we track them, but ultimately it is the same ice cream underneath.
This means that when the hydra grows another head, you know from which neck it has (likely) grown.
Ice cream flavors also allow us to steer clear of geographical implications in the naming convention. While it is useful for analysis to understand where attacks, CnC servers and the like originate from, it is unwise to attribute campaigns to regions with certainty. Spoofing an IP address is incredibly easy, and it has been widely reported how nation states have masqueraded as other nations for geo-political benefit.
The Details
For the benefit of our customers and the wider security community, we will share as many campaign–specific indicators as we can, without compromising the effectiveness of our hunters. You can expect to see information on CVEs, filetypes, ASN/ASO, preferred targets, and general tactics/techniques. Shared data will be summarized under:
- Exploits used
- TTPs
- Targets
- Flavor Infrastructure
- Actions on Objectives
We will not share some specific IoC/IoAs when they are still being actively used to identify malicious actions, where sharing would alert the threat actors of our knowledge and make hunts less effective.
If you are an Alert Logic customer, be assured that we are constantly hunting for signs of these activity clusters daily. We will raise any malicious activity to you and work with you to disrupt the attack, remediate elements of compromise and persistence, and ultimately leave you with a better security posture.
If you are not an Alert Logic customer, this series could be beneficial to your cybersecurity practices or your own threat hunts.
We hope by sharing this information with the wider community, we can contribute toward the shared understanding of our common enemy and foster further security discussions and successful hunts.
Find out how Alert Logic can support your organization in tackling existing and emerging threats by scheduling a personalized MDR demo.
Additional Resources
Explore our Project Ice Cream threat activity clusters series: