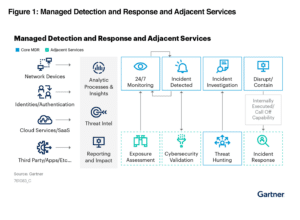
What is MDR?
A curated set of technologies, advanced analytics, and security operations experts integrated into a single managed service, MDR’s primary goal is reducing the likelihood and impact of successful cyberattacks. MDR solutions identify and rapidly respond to anomalies and potential breaches — this quick detection of incidents allows MDR to contain, investigate, and remediate issues, ultimately minimizing any damage.
Essential components of MDR include 24/7 threat monitoring, vulnerability scanning, integrated detection (endpoint, network, cloud), log management, automated response, guided remediation, real-time reporting and dashboards, analytics, and threat hunting.
What Challenges Does
MDR Solve?
Today, organizations are under constant threat of compromise and disruption due to security breaches. And these threats are increasingly more sophisticated attacks with nuanced social engineering tactics.
According to Gartner,
“By 2025, 60% of organizations will be actively using remote threat disruption and containment capabilities delivered directly by MDR providers, up from 30% today.”
Is MDR right for you?
Learn if your organization could benefit from MDR by requesting a demo.
MDR — and threat detection solutions in general — has increased in priority as organizations realize no level of investment provides 100% protection against threats. Add in the scale and complexity of the current environment and many organizations of all sizes cannot combat security challenges with their internal resources.
MDR addresses common challenges such as:
 Evolving
Evolving
Threat Landscape
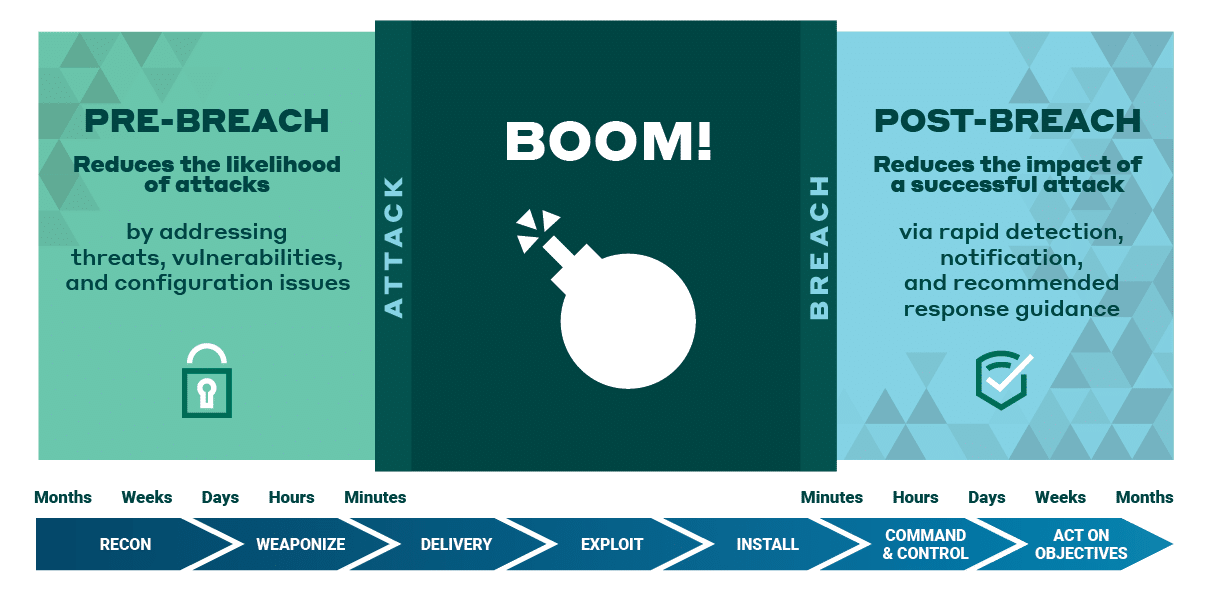
Increasingly sophisticated attack methods that are growing in frequency makes detection and protection even more difficult. MDR addresses both pre- and post-breach concerns as it reduces the likelihood of an attack and minimizes the impact if (or when) a breach occurs.
 Lack of
Lack of
Security Expertise
While organizations often have skilled IT staff to run their businesses, these internal resources tend to not have the security expertise needed to respond to the ever-changing threat landscape. By leveraging an MDR vendor’s expertise, organizations add a fully staffed and experienced security operations center (SOC) providing 24/7 monitoring. Your team, then, can focus on their job duties, while the MDR vendor focuses on security.
 Dynamic
Dynamic
Environments
As organizations adapt their infrastructures to accommodate new and changing business needs, securing their environments — from cloud workloads to on-prem networks — can be challenging. Lack of visibility across the infrastructure may create blind spots to potential threats. MDR provides visibility across the environment – from endpoint to networks to cloud workloads – via a single console to quickly identify, detect, and respond to threats.
 Prioritizing
Prioritizing
Risk
Today’s security teams use numerous security tools on a daily basis, often with unique consoles and no ability to correlate, analyze, or prioritize the activities and threats that pose the greatest risk to their environment. MDR provides a single pane-of-glass of the environment with real-time threat risk and vulnerability dashboards to identify and focus on the activities and areas that pose the greatest risk, from known threats to unpatched servers.
 Unrealized
Unrealized
Security Outcomes
After significantly investing in tools and people, organizations often fall short of realizing the security posture they need. They either lack the expertise to gather actionable insights or make actionable decisions from the multiple sources of data and alerts now at their fingertips. MDR provides a holistic view of the customer environment, powered by threat intelligence and analytics from thousands of customers and feeds, and monitored by a team of security operations experts with unparalleled years of expertise and whose primary focus is to help organizations achieve their intended security outcomes.
 Regulatory
Regulatory
Compliance Requirements
Ensuring compliance to multiple regulations is no easy task. Organizations often are overwhelmed with the manual and time-consuming task of preparing for and demonstrating adherence to specific regulations. MDR simplifies this process by enabling you to advance your security compliance strategy with visibility into the current state of adherence to compliance mandates, guidance to improving your environment, and ongoing monitoring of adherence via audit-ready reporting.
How Does MDR Work?
MDR works by integrating a security platform with analytics and expert-led services to provide threat detection and response recommendations across cloud, hybrid, and on-premises environments and endpoints. This is done by identifying all of an organization’s assets, profiling their risks, and then collecting activity information from logs, events, networks, endpoints, and user behavior. Threats and vulnerabilities are researched in the wild and codified so as to be quickly recognized when seen by the MDR provider. MDR analysts then take over to validate incidents 24/7, escalating critical events and providing recommended response actions so threats can be remediated.
Integrating technology and analytics with human expertise to provide MDR services to protect the entire attack surface.
| MDR Platform Technology to collect and analyze security data |
MDR Services Experts augment the technology, validating, and provide human expertise to effectively remediate |
|||
| Collect | Analyze | Validate & Augment | Report & Inform | Respond |
| Assets | Correlation | 24/7 Monitoring | Escalate Incidents by Phone, Email, Ticketing, or Messaging Integration | Incident Review |
| Logs | Behavior | Investigation | Periodic Security Value Review | Remediation |
| Events | Anomalies | Validate Incidents | Custom Event and Log Reports | Response Automation |
| Network Activity | Parsing | Qualify Threat Severity | Provide Security Context | |
| Endpoint Telemetry | Threat Hunting | |||
| Cloud Workloads/Activity | Tuning | |||
| User Behavior Activity | Security Content | |||
| File Creations/ Deletions/Modifications |
||||
| Security Control Telemetry | ||||
| 3rd-party Integrations & Sources | ||||
See how MDR works: Watch a short demo video to see MDR in action >
MDR Benefits
Benefits of securing your IT estate with MDR include:
- Continuous monitoring of the entire environment
- Visibility across an organization’s IT estate, including network, endpoints, and cloud
- Minimizing the likelihood of successful attacks due to vulnerabilities in the environment
- Reducing the impact of an attack as the time in which a successful attack goes undetected is minimized
- Improving security posture
- Having designated security resources who are intimately familiar with an organization’s environment and specific business outcomes
- Team of security experts who serve as an extension to your organization
- Actionable insights and remediation guidance from highly experienced security experts
What Leads to Effective MDR?
An effective MDR solution provides protection for on-prem, cloud, and hybrid environments. MDR should include easy deployment, scalability, and integration of network, log, and endpoint-based detection technologies with threat intelligence and active threat hunting.
As a managed service, MDR must provide 24/7 support and offer organizations’ designated analysts and customer success managers. Additionally, it should offer flexible pricing and licensing options that adapt to a customer’s changing needs.
24/7 Monitoring
Active monitoring and threat detection with around-the-clock visibility across the entire environment, leveraging technology and augmented with human insights to deliver actionable guidance.
Human Expertise
A global security operations center with a team of security experts who provide remediation guidance and insights to proactively protect against threats and improve your overall security posture.
Threat Intelligence and Analytics
Includes information from third-party feeds, platform technology, and attempted attacks to develop insights and implement new techniques for continuous protection against known and unknown threats.
Continuous Research
Performed by experienced analysts to augment security tools and technology, security content is continuously refreshed with research on new and emerging threats and vulnerabilities.
Response Automation
Balance automation with human guided response, enabling organizations to adopt automation at their own pace.
Continuous Innovation
A rapidly changing and dynamic threat landscape requires that technology be continuously innovated. Vendor should have an unwavering commitment to innovation, including feature enhancements made available to customers at no additional cost.
Audit-ready Reporting
Easy reporting for audit and regulatory compliance purposes, with self-serve reports and security benchmarks that simplify the audit process and measure continued security progress and posture.
Quite simply, not all MDR solutions or their providers are created equal. Each varies significantly in services offered, security expertise, depth of threat intelligence and analytics, and customer experience.
See how Alert Logic MDR can help your organization achieve the desired security outcomes you have set.
Considering MDR for Your Organization?
If you’re evaluating MDR vendors, there are things you should consider for each potential MDR service provider. Check out our blog on MDR Vendor Evaluation Tips to learn what “good” MDR looks like and the questions you need answered.
For more guidance on MDR vendor selection, consider the following resources:
MDR Buyer’s
Guide
How to choose an effective managed
detection and response (MDR) provider
2023 Gartner®
Market Guide
for Managed Detection and
Response Services
2023 Bloor Research MDR Market Update
Key developments in the
maturing MDR market
MDR vs. MSSP, SIEM, XDR and More
MDR vs MSSPs
Managed detection and response service vendors deliver comprehensive detection and response services to their customers. MDR integrates a curated set of technologies, advanced analytics, and human expertise in a single service they manage, ensuring all the components remain current, updated, functioning, and working seamlessly together.
In contrast, managed security service providers’ (MSSP) range of services includes third-party security tool installation, administration, monitoring, and reporting. Typically, their focus is on operating multiple security toolsets and they do not invest heavily in specific areas which an MDR provider does such as threat research, threat intelligence, or threat analytics. MSSP is most successful when integrating third-party tools into processes for which they cannot control the roadmap. As this solution centers on prevention, they do not focus nor adequately invest in the research or staffing required to perform managed detection and response. Some MSSPs recognize this and outsource the detection and response aspects of their service to MDR vendors.
Continue learning: MDR vs. MSSP: 6 Major Differences
MDR vs. SIEM
SIEM (security information and event management) is a security solution that gives organizations insights into potential security threats across business networks via centralized collection and analysis of normalized security data pulled from a variety of systems. Whereas SIEM aims to detect attacks, MDR goes further as the solution exposes vulnerabilities within a system, application logs, analyzing user behavior and activity which can lead to early indications of an attack.
One notable difference between MDR and SIEM is in the approach taken to cybersecurity. Unlike SIEM, MDR takes a proactive stance in safeguarding against threats. While SIEM typically just prioritizes threats detected, MDR moves the needle forward by actively diving into the threat landscape through comprehensive exploration of attacker activities across a more extensive spectrum.
Continue learning: Head-to-Head: MDR vs. SIEM
MDR vs. EDR
EDR (endpoint detection and response) is a software focusing on the detection of and response to cybersecurity threats on an endpoint (the physical devices connected to a network such as servers, laptops, and mobile devices.) EDR can provide threat detection, prevention, and the ability to quarantine compromised assets.
MDR is a service that continuously monitors, prioritizes, and responds to cybersecurity threats by using both technology and human expertise. MDR often is augmented with EDR solutions by empowering analysts to act on the endpoint. By leveraging the principles of network security monitoring coupled with detection and prevention solutions, MDR service providers can offer improved security posture and threat coverage from network to EDR.
MDR vs. XDR
XDR (extended detection and response) extends detection and response capabilities beyond the endpoint, gathering and correlating data from endpoints, emails, servers, apps, clouds, and networks for better visibility across the attack surface. XDR functionality varies substantially between vendors as the definition of and requirements for XDR can differ significantly.
For an XDR solution to be successful, there must be internal team members who have security knowledge and/or expertise, which many organizations are lacking. With MDR, you receive a high level of human expertise around alert data, the managed component that XDR is missing. XDR is best viewed as complementary to MDR, rather than an alternative to it, and may be included as part of a managed detection and response solution.
Continue learning: What is XDR Security?