With Alert Logic MDR, you get the industry’s only network intrusion detection solution and log management for containers – with support for AWS, Azure, hybrid, and on-premises environments.
Your technology stack most likely consists of a broad array of systems and applications. These would range from end user apps, to app hosting on servers and containers, to third-party SaaS applications. Many different applications will be dependent on these systems, including authentication technologies, web apps, anti-virus and more—all critical business and customer technology that drives your operation.
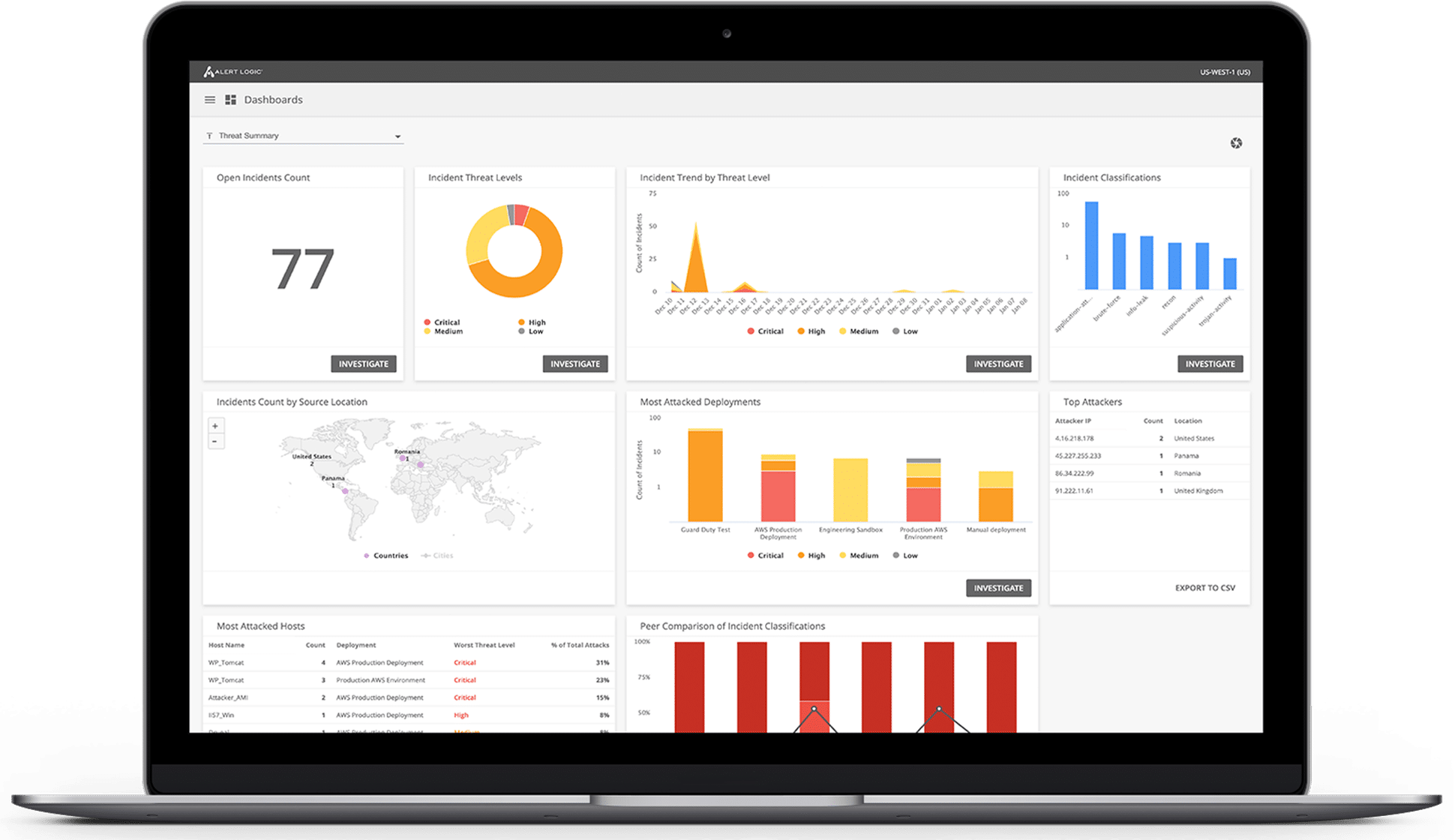
Data is constantly collected for all your systems and applications, through traditional or cloud-ready methods, and fed into our single threat detection and analysis platform.

Log Sources and Integrations
Our MDR solution ingests hundreds of log types for collection, incident generation and/or compliance purposes.
Applications
Containers
Our security solution aligns with your strategy, protecting your data and assets regardless of where they are located or what technologies you use.
Servers
Endpoints
Business SaaS Applications
SaaS Platform
Our platform integrates with common business SaaS applications, providing comprehensive visibility. Alert Logic’s security researchers and other experts are continually focused on the development of new and innovative technology, to maintain pace with the ever-changing threat landscape. Because our platform is SaaS-delivered, these innovations are usually included at no additional cost to customers.