Protect Your Cloud, On-Premises, and Hybrid Environments
Alert Logic provides flexible security and compliance offerings that seamlessly connect platform, threat intelligence, and expert capabilities to deliver optimal coverage across your environments.
- Capabilities by Design: Only Alert Logic owns all three components necessary to deliver seamless security – and internally organizes them to work together seamlessly.
- Security Complexity Made Simple: Our platform, expert defenders, & threat intelligence improve your security and compliance posture, defend you 24/7, and absorb complexity from threat identification to the board room.
- Better Security at Lower Total Cost: Alert Logic enables the right level of coverage for the right resources. This ensures an optimal cost of security and compliance (compared to point product providers) with a better solution experience.
- Flexibility for Any Environment: Alert Logic supports the environments you have (cloud, on-premises, hosted, and hybrid), giving you the flexibility to securely compute where you want for business success.
- Continuously Advancing: Alert Logic stays on the cutting edge of threat intelligence and uses machine-learning that builds on data from our customers to enable ever-smarter, ever-stronger security coverage.
Alert Logic provides flexible security and compliance offerings that seamlessly connect platform, threat intelligence, and expert capabilities to deliver optimal coverage.
Alert Logic Solution Benefits
SECURITY PLATFORM
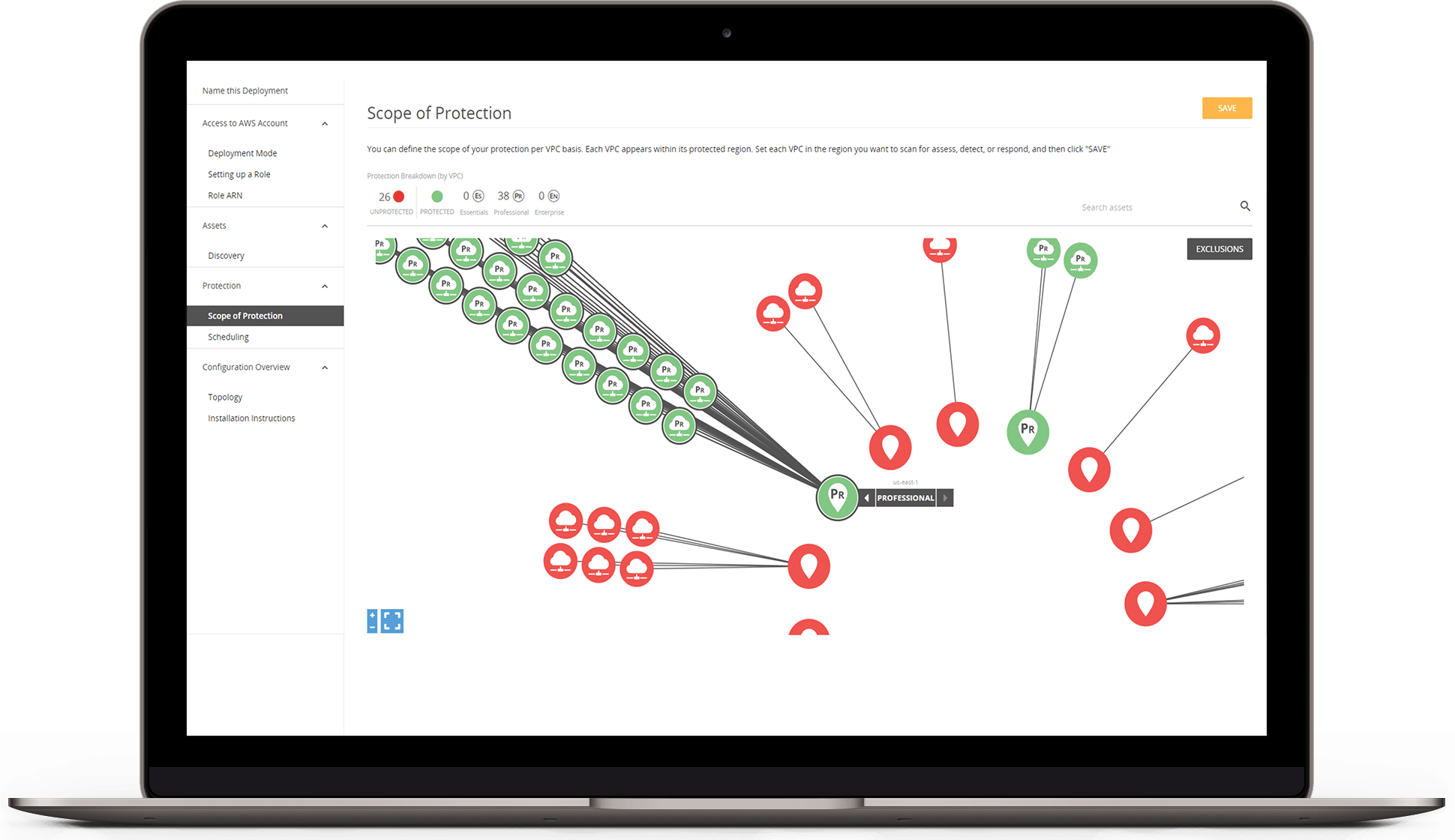
- Asset discovery
- Vulnerability Scanning
- Threat monitoring and visibility
- Intrusion detections
- Security analytics
- Log Collection and Monitoring
- Always-on WAF defense against web attacks
THREAT INTELLIGENCE
- Threat Risk Index
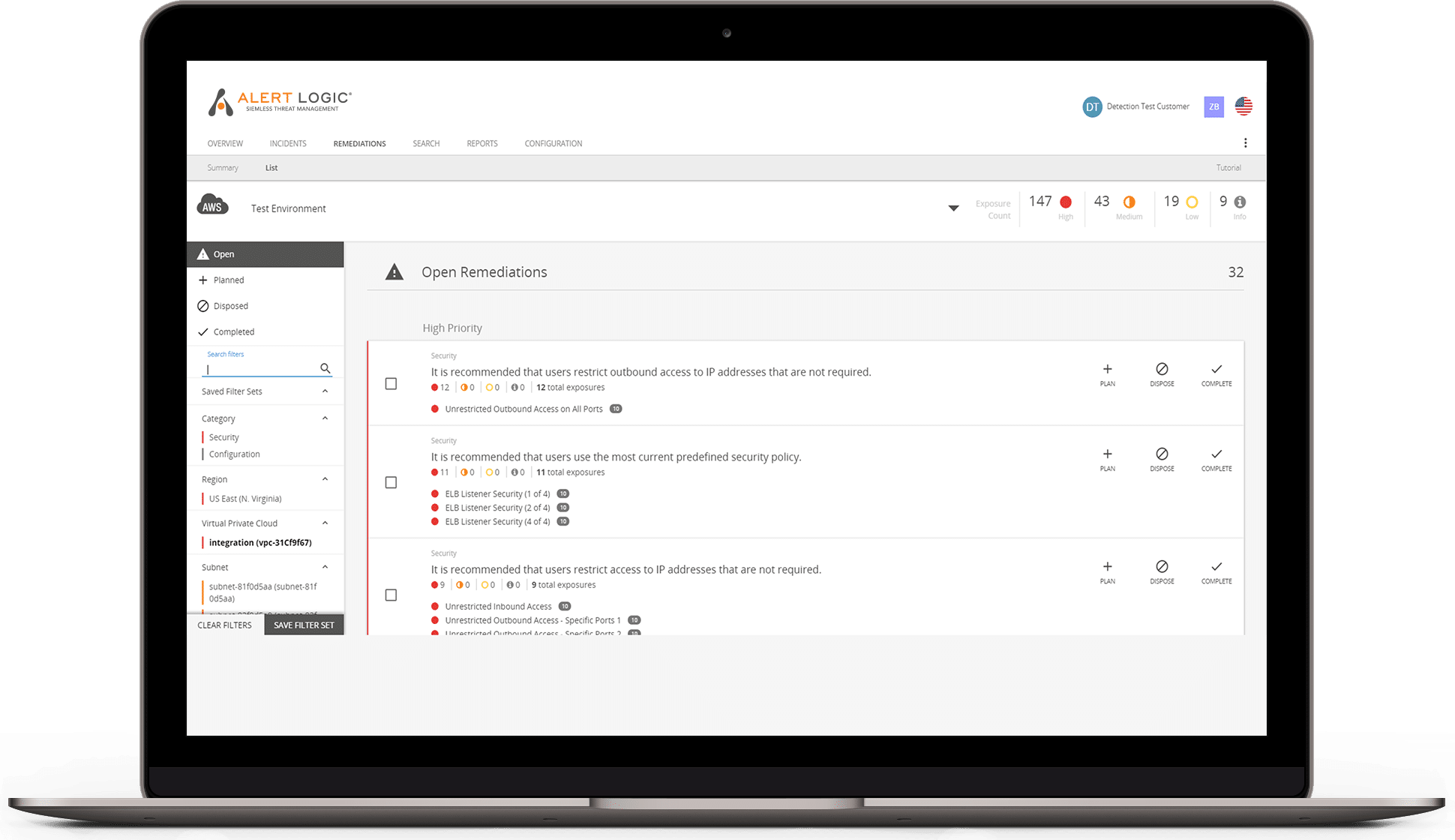
- Remediation guidance
- Comprehensive vulnerability library
- Event insights and analysis
- Threat frequency, severity, and status intelligence
- Attack prevention capabilities
- Verified testing 2.1 million + web application attacks
EXPERT DEFENDERS
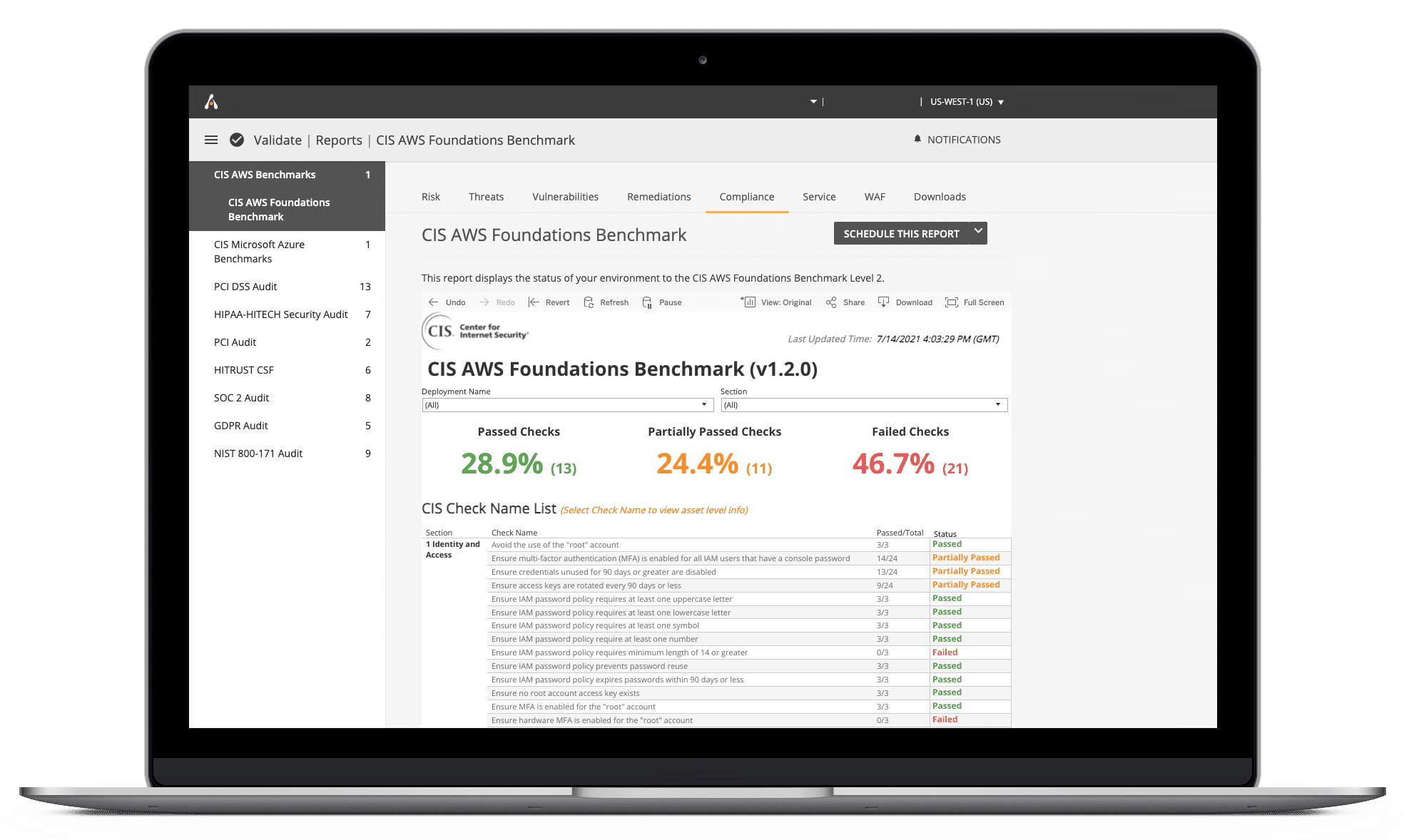
- 24/7 SOC with incident management, escalation, and response support
- PCI Scanning and ASV support
- Service health monitoring
- Incident response assistance
- Threat hunting
- Help with tuning strategies, customized policies, and best practices