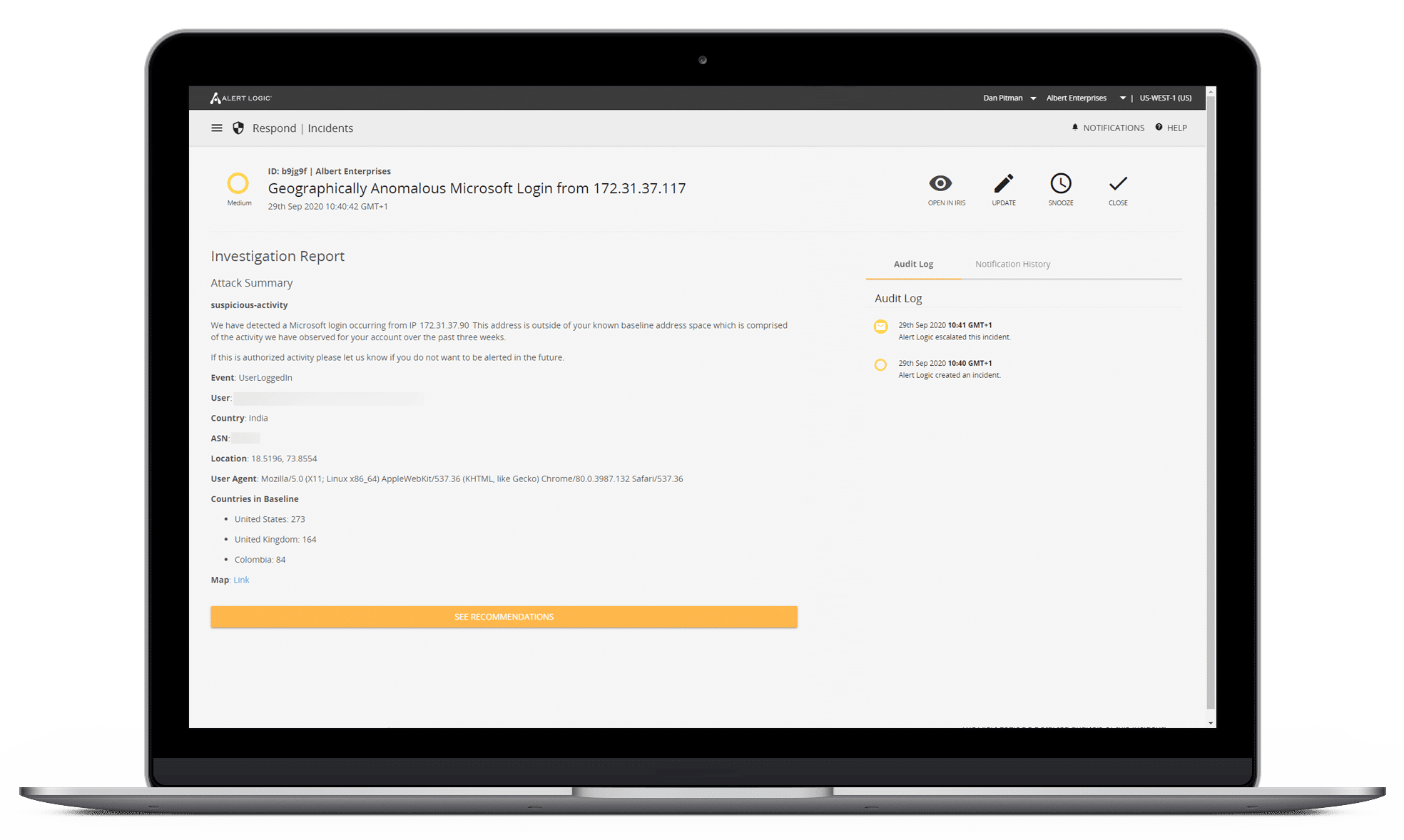
Azure Security Monitoring Made Simple
Alert Logic offers an integrated suite of managed infrastructure and workload security and compliance controls for your Azure environment, all delivered to you as a single service. Providing you with:
- Intrusion detection systems (IDS) to detect a wide array of attack methods of security threats lurking in your network traffic, including exploits in web app frameworks, containers, app stack components and attack methods included in the OWASP Top 10
- Log management to meet compliance requirements and to identify suspicious behavior from a comprehensive group of sources, including Azure Monitor and Azure Storage Accounts (Blobs or Tables), and Azure-deployed containers
- Vulnerability Management and security configuration management to assess your security posture and identify vulnerabilities hidden at all layers of your application stack
- The industry’s first network-level container security intrusion detection for Azure-deployed Kubernetes
- Expert incident analysis and live notifications of critical attacks from one of our GIAC-certified security analysts within 15 minutes
- A broad set of security compliance controls for GDPR, PCI DSS Compliance, HIPAA HITECH, SOC 2, and SOX COBIT—including PCI ASV attestation reporting and fully managed and centralized logging
- Azure Event Hubs integration with machine-learning analytics for behavior and anomaly detection
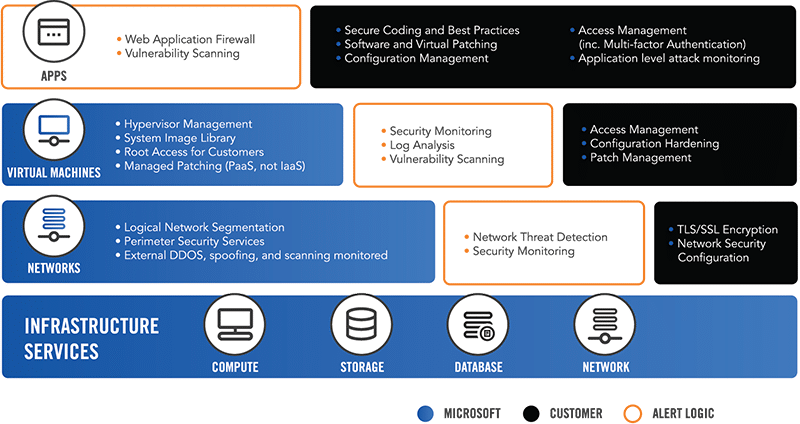
Azure Shared Responsibility Model
How We Do It
Designed for Microsoft Azure
Alert Logic has designed security for applications and other workloads running on Azure from the ground up for agility and scale. Our microservices architecture and RESTful API are combined with advanced logic that natively understands Azure API outputs including Azure Monitor and Azure Storage Accounts (such as Azure SQL or IIS logs from App Services workloads), blending security seamlessly into your CI / CD pipeline and dynamic production environment.
Benefits of Azure Security with Alert Logic
Quickly find unauthorized activity from the Azure Event Hubs without having to hire security experts to investigate alerts, remove noise, analyze and prioritize incidents.
Actionable Threat Detection and Response
Security data is collected, aggregated, and analyzed to identify attacks. High-priority threats are verified and you quickly notified with remediation recommendations to address the attack.
Monitored by Security Experts
GIAC-certified security experts identify, review, investigate and escalate incidents to proactively protect against cyber threats 24/7.
Add Additional Security Context
With Azure Event Hubs integration, we add additional security context to web application security, network vulnerability scanning, log correlation and reporting.
Benefits of Azure Security with Alert Logic
Alert Logic provides agile security services that scale with native API-driven automation and templates for Azure and DevOps tool chains, all delivered as a single subscription. This allows you to:
- Focus on the most cloud-relevant threats with full-stack protection of your full application and infrastructure stack
- Accelerate production with API-driven automation and elasticity
- Add cyber security experts to your team overnight without hiring staff
- Preserve application performance with lightweight agents and auto-scaling support
- Simplify with one service that works across all your Azure, on-premises and hybrid environments.
Capabilities
Threat Management
Seamless integration of platform, threat intelligence, and expert services.
Cybersecurity Monitoring
Alert Logic provides the security platform, up-to-date threat intelligence and expert defenders to deliver round-the-clock network security monitoring against threats, attacks, and potential risks to your business.
Web Application Firewall (WAF)
Our managed WAF is your frontline defense against attacks. Deployment models match your requirements and offer 24/7 monitoring for solid protection against compromises.
Network Intrusion Detection System (IDS)
Our IDS and vulnerability assessment services monitor your network, identify suspicious activity, and provide verified alerts and recommended remediation steps.
Vulnerability Scanning & Assessment
Alert Logic helps you reduce your attack surface by finding vulnerabilities before your adversaries do with cloud native vulnerability and configuration capabilities.
Log Management
Our log management solution collects and normalizes your log data, while our 24/7 expert monitoring and analysis adds human intelligence to find key insights.