Since the U.S. federal government commissioned the non-regulatory federal agency National Institute of Standards and Technology (NIST) to develop a set of cybersecurity best practices to bolster the nation’s critical infrastructure, the NIST Cybersecurity Framework (CSF) has spread to an estimated one out of every two companies and expanded to include all sectors.
Given that the NIST CSF is entirely voluntary, that’s an impressive feat.
Created in 2013 in response to Presidential Executive Order (EO) 13636, the framework is in its second iteration as NIST CSF 2.0 was released in February of this year. NIST 2.0 comes with modern additions suited for the security needs of a new decade, and openly offers its guidance to companies beyond those involved in “essential government functions.”
As NIST CSF 2.0 adoption continues to spread, so does public interest surrounding how best to leverage it. Following are some of the internet’s most pressing questions about one of cybersecurity’s most popular frameworks, and answers that can help every organization take advantage of it.
1. Do I need a NIST assessment?
If you want your organization’s security strategy to be grounded on a NIST framework, you have to do a NIST assessment. What is a NIST assessment? A NIST assessment is your first initial level-setting exercise to see where your current systems stand in relation to NIST compliance and safety standards. The assessment can be done against any one of the NIST standards, and while it can be done by your own in-house team, it is typically outsourced to an external MSP or cybersecurity provider that offers NIST guidance.
2. How many controls does NIST CSF 2.0 have?
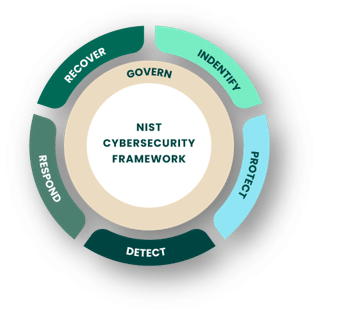
Whereas NIST CSF had five key functions or controls, NIST CSF 2.0 has six. These controls combine to provide comprehensive coverage of the cybersecurity risk management lifecycle and protect crucial information. The inclusion of the new Govern function expands the overall framework to include:
Govern
Establish your cybersecurity policy, expectations, and strategy.
Identify
Discover any elements currently causing risk to your business (vulnerabilities and security weaknesses).
Protect
Implement safeguards to reduce cybersecurity risks.
Detect
Discover any exploits that could potentially cause risk in the future, or are causing risk now (zero days, in-progress attacks).
Respond
Take action against discovered areas of compromise.
Recover
Restore operations to a pre-incident state using a disaster recovery or business continuity plan.
3. Why the new Govern function?
For 10 years, NIST CSF was known for its “five key functionalities.” So why add Govern, and why add it now? NIST defines the Govern function as “Policies, processes, procedures and practices across the organization related to the mapping, measuring and managing of AI risks are in place, transparent, and implemented effectively.” Govern was added to provide clarity, focus, and cohesion to the five other functions and establish the priority of the security goals they seek to achieve. It provides context around what the other functionalities can crystallize on and helps align outcomes at the start.
As Daniel Dukic, Cyber Security Technology Specialist at Microsoft, noted, “The purpose of this update seems [sic] to emphasize the significance of formulating suitable policies and procedures, evaluating and prioritizing potential risks, and outlining the roles and responsibilities within a cybersecurity program. This resonated with me as I have seen firsthand the impact of not having these foundational elements in place.”
The new function is so integral that it replaced “Identify” as the head of the function list. The arrangement places an overarching cybersecurity structure around the subsequent pillars (Identify, Protect, Detect, Respond, and Recover) and emphasizes the importance of knowing where you’re going before taking action.
4. Is NIST 800-53 the same as NIST CSF?
Not exactly.
NIST 800-53 is a very specific set of regulations for federal agencies and contractors and is considered by many to be the gold standard of international cybersecurity regulations (despite its having been commissioned by and for the U.S. government). It is comprehensive, intricate, and popular with larger enterprises with unique compliance requirements, and comprises 1,077 total controls.
NIST CSF, on the other hand, is a more general set of guidelines designed for simplicity, cost-effectiveness, and adaptability, making it perfect for widespread use and smaller companies looking to align with a set of industry-recognized cybersecurity best practices. It has a relatively shorter list of 108 security controls.
5. Are NIST standards mandatory?
Some. And it depends on who you are.
NIST 800-53: Yes, for federal agencies and contractors
Executive Order 13800, Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, mandated NIST 800-53 compliance for all federal agencies since its issuance in 2017, and NIST 800-171 is now mandatory under Cybersecurity Maturity Model Certification (CMMC) guidelines.
This goes for federal contractors, as well. Anyone doing business with the U.S. federal government must comply with NIST cybersecurity standards. In addition, government agencies and their contractors are typically held accountable for complying with all NIST Special Publications as well. This includes:
- NIST 800-53 | Guidelines for privacy and data security controls
- NIST 800-171 | This Special Publication underpins the CMMC, a mandatory security standard for all Department of Defense (DoD) contractors and any organizations in their supply chain.
NIST CSF 2.0 — No, optional for all
For everyone else, NIST CSF 2.0 compliance is voluntary. Even at its initial release in 2013, the NIST Cybersecurity Framework was an optional guideline for organizations within the U.S.’ critical infrastructure sectors. However, the framework proved so useful that only two years later, it was estimated that one in three of all U.S. organizations adopted it – even those outside the scope of critical infrastructure.
Part of the mass appeal of this voluntary framework is that you don’t have to start from scratch when building out your cybersecurity strategy. Organizations that adopt NIST CSF 2.0 have a flexible, government-level security standard on which to model their security controls, build out their policies, and prevent against advanced exploits like never-before-seen emerging threats and advanced persistent threats (APTs).
6. What is the difference between NIST CSF and RMF?
These two separate, but dually useful, frameworks are designed to support each other and not compete.
The NIST Risk Management Framework (RMF) focuses exclusively on risk management practices and is mandatory for federal agencies and any organization that handles federal data. It presents a comprehensive, systematic approach to managing risks based on business objectives, risk appetite, and specific requirements, and focuses on six key areas:
Categorize
Define and prioritize your risks from greatest to least.
Select
Find which security controls are right for the job and will minimize those key risks.
Implement
Decide how those controls are going to be actioned and action them.
Assess
Make sure the controls are doing their job and fix any errors.
Authorize
Give your newly risk-protected system permission to operate.
Monitor
Collect regular data on how the system, your policies, and the overall risk management program is achieving its goals.
By comparison, NIST CSF is a more general approach to improving an organization’s cybersecurity posture in general and can be used in conjunction with the more risk specific NIST RMF.
7. How does NIST define a Privacy Impact Assessment (PIA)?
Generally, a PIA determines how Personally Identifiable Information (PII) is used, stored, and managed within an organization. It should accomplish three things:
- Ensure the entity conforms to all privacy requirements
- Identify the risks and effects of handling said sensitive data
- Look at any other ways of handling the private data that could mitigate risk further
NIST notes that PIAs can be submitted as supporting references to security and privacy plans required under the “Authorization” stage of its Risk Management Framework.
8. Can you map NIST to compliance controls like PCI DSS?
Yes. In fact, you should.
The PCI Security Standards Council said they and NIST “share the common goal of enhancing data security” and released an instructional guide to help organizations through the process of mapping PCI DSS v3.2.1 to NIST CSF. The document covers which PCI DSS requirements coincide with NIST CSF outcomes under the Identify, Protect, Detect, Respond, and Recover functions. As it states, “the mapping can help identify where the implementation of a particular security control can support both a PCI DSS requirement and a NIST Framework outcome.” While that document was the latest published content for mapping, third-party mappings of PCI DSS 4.0 to NIST CSF are currently available in private offerings or via vendor compliance consultations.
9. How does CIS Controls v8 compare to NIST CSF 2.0?
The Center for Internet Security (CIS) has a resource mapping NIST CSF to CIS Controls v8. In essence, the two frameworks are highly similar, as the documents suggest, and overlap on a number of key issues including maintaining a detailed inventory of assets, keeping a software inventory, establishing a secure data management process, and implementing a secure configuration process.
However, in practice, the two frameworks have their differences. The CIS Controls are viewed as more prescriptive, and so may work better for smaller organizations looking for general “foundational security measures … to achieve essential [cyber] hygiene.” NIST CSF 2.0, while more flexible than NIST 800-53, is still a systematic methodology of specific practices that is customizable based on the needs of an organization, making it ideal for larger, more established organizations looking to cater to custom sector needs, budgets, and risk tolerances.
Fortra Supports NIST CSF 2.0
Both Fortra’s Alert Logic and other Fortra solutions offer services to help organizations Govern, Identify, Protect, Detect, Respond, and Recover as related to NIST CSF 2.0. For more information, request an Alert Logic demo to see our security solutions for yourself.
The NIST Risk Management Framework (RMF) focuses exclusively on risk management practices and is mandatory for federal agencies and any organization that handles federal data. NIST CSF is a more general approach to improving an organization’s cybersecurity posture in general and can be used in conjunction with the more risk specific NIST RMF." } }, { "@type": "Question", "name": "How does NIST define a Privacy Impact Assessment (PIA)?", "acceptedAnswer": { "@type": "Answer", "text": "Generally, a PIA determines how Personally Identifiable Information (PII) is used, stored, and managed within an organization. It should accomplish three things: 1. Ensure the entity conforms to all privacy requirements 2. Identify the risks and effects of handling said sensitive data 3. Look at any other ways of handling the private data that could mitigate risk further." } }, { "@type": "Question", "name": "Can you map NIST to compliance controls like PCI DSS?", "acceptedAnswer": { "@type": "Answer", "text": "Yes. In fact, you should.
The PCI Security Standards Council said they and NIST “share the common goal of enhancing data security” and released an instructional guide to help organizations through the process of mapping PCI DSS v3.2.1 to NIST CSF. The document covers which PCI DSS requirements coincide with NIST CSF outcomes under the Identify, Protect, Detect, Respond, and Recover functions. As it states, “the mapping can help identify where the implementation of a particular security control can support both a PCI DSS requirement and a NIST Framework outcome.”" } }, { "@type": "Question", "name": "How does CIS Controls v8 compare to NIST CSF 2.0?", "acceptedAnswer": { "@type": "Answer", "text": "The CIS Controls are viewed as more prescriptive, and so may work better for smaller organizations looking for general “foundational security measures … to achieve essential [cyber] hygiene.” NIST CSF 2.0, while more flexible than NIST 800-53, is still a systematic methodology of specific practices that is customizable based on the needs of an organization, making it ideal for larger, more established organizations looking to cater to custom sector needs, budgets, and risk tolerances." } } ] }