Ransomware attacks continue to grow across organizations. According to “The State of Security 2023,” 43% of respondents had data/systems held hostage; of those, 75% paid off the ransom (or their insurer paid it) with the cost, on average of the largest ransom paid to attackers being $430,978. And according to the “”Doubling Down” report, in 2023, ransomware payments surpassed $1 billion.
Preventing an attack is no easy feat, and knowing how to respond if you’re targeted is equally daunting. Dive into our blog to gain insights on ransomware attacks and bolster your organization’s cybersecurity measures.
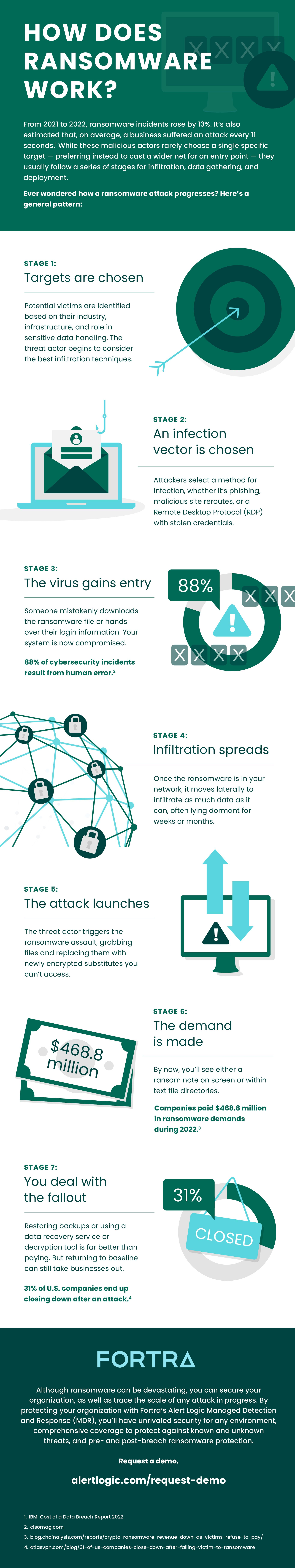
What is Ransomware and How Does it Work?
Ransomware is a cyberattack in which threat actors gain access to an individual or organization’s private data information. The threat actor then encrypts the data and demands a ransom payment to restore access via a decryption key. Attacks have ballooned since COVID-19, as an unprecedented volume of personal and business is now virtual.
Contrary to what some believe, attackers don’t necessarily target the most lucrative enterprises. Instead, they cast a wide net, attacking several organizations of varying sizes at once, and exploit whichever one(s) they can access.
Free Report: Ransomware in Focus
The most common attack vectors:
- Email phishing: Phishing is one of the most common ransomware attack vectors. It occurs when a threat actor sends bogus emails to users containing prompts, attachments, or links from what is purported to be a trusted source. The email copy encourages unsuspecting users to either divulge sensitive personal information or download malware directly to their computers.
- RDP protocol: Remote desktop protocols (RDPs) enable multiple Microsoft Windows devices to connect over the internet without needing a physical connection. Without controls in place to ensure all RDP ports are closed after they are no longer operable, ransomware actors can easily gain access and encrypt exposed data.
- Software vulnerabilities: When system administrators don’t update their firewalls and patch security vulnerabilities, harmful actors can penetrate systems and steal key data. Once a ransomware attacker breaches your security, they have access to an enormous volume of your sensitive information.
How Can Ransomware Attacks Affect a Business?
Ransomware attacks can have a tremendous financial impact on your business. While direct ransom payouts to attackers account for a huge portion of financial losses, they don’t end there. Systems and processes usually shut down temporarily after an attack, making it impossible to continue running business as usual. You’re unable to deliver for your clients, and that can lead to further financial losses and damage to your brand.
A survey from TechRepublic found that 66% of surveyed businesses experienced “huge revenue losses” due to ransomware attacks.
Take note of some of the most damaging effects ransomware can have on your business:
- Hurts brand recognition: Ransomware is bad for everybody involved, and that includes customers. When operations go offline, customers can’t get the products and services they paid for in a reasonable timeframe. That can lead to anger and resentment, and your brand’s reputation may be the main casualty.
- Damages trust: Data is the engine that drives the digital economy forward. Customers and companies exchange thousands of pieces of data daily, an activity that depends on a substantial degree of trust. When your organization is the subject of a ransomware infection, customers may see you as careless with their personal information. That can cause permanent damage to their trust in you.
- Disrupts your organization: Ransomware attacks are serious. At times, executive teams dole out punishments to help heal the brand’s image. Oftentimes, that means senior-level personnel who bore some responsibility for failing to prevent the attack must step down or leave. Loss of revenue also may force executives to terminate junior-level staff.
- Forces permanent closure: In a worst-case scenario, ransomware attacks are so financially damaging that an organization closes their doors permanently. While these instances are somewhat rare, a report from Atlas VPN found that 31% of U.S. companies end up going out of business after a ransomware attack.
How to Protect Yourself from a Ransomware Attack
Take these recommended actions before, during and after an attack to protect your organization:
Monitor and identify
Hackers’ capabilities evolve constantly. Consequently, you need a program that monitors and identifies vulnerabilities and implements a patching program to reduce the attack surface. It is also important to pinpoint the latest developments in ransomware campaigns. This threat intelligence helps you understand the capabilities of malicious actors so you can prioritize assets needing patching.
Detect and contain
Even the best security systems are unable to stop all attack. Therefore, you must have a way to recognize indicators of compromise (IOC) once a cybercriminal penetrates your networks. Specifically, establish a robust monitoring system to continuously analyze log data from across your applications and systems. These help you identify attacks as soon as they open, helping you take immediate action.
Once you identify a ransomware threat, your critical infrastructure needs to be properly equipped to limit the spread of the attack, localizing it and preventing it from gaining access to system files in other parts of your organization. Collecting threat data not only helps you mitigate the damage a current threat causes, but it also helps you learn about ransomware trends and better plan for future attacks.
[Related Reading: Hunting Ransomware with Threat Detection]
Respond and mitigate
Carry out a full assessment of the attack to better understand its modes of operation. Gather information including which hosts were infected, how the attack happened, and the degree of damage sustained.
Once you analyze this information, you can harden other targeted assets. Any remedial action should involve multiple teams, partners, and users, ensuring that every stakeholder affected by the attack has input on your response plan.
Should you pay the ransom?
Law enforcement officials in the FBI urge organizations not to pay ransom in exchange for the decryption key. Paying the hacker encourages future attacks against other organizations, and it won’t guarantee that you regain access to your data.
How to Prevent Ransomware Attacks
One of the simplest yet most important measures to preventing ransomware attacks is educating your employees. In fact, CISO MAG found that 88% of security breaches were the result of human error. Train employees in recognizing and reporting any online activity that looks suspicious. Employees should not give personal information away unless they are certain they completely trust the source they’re sharing it with.
While this isn’t exactly a way to prevent a cyberattack, it’s important to have data backups stored in a secure, off-site backup facility. Backups provide a safety recourse in the event of a security breach, helping you restore any data that’s lost to attackers.
A hacker can gain access to IT assets that have not been properly disposed of at the end of their lifecycle. When replacing legacy components with new hardware or software, it’s critical that you destroy all stored data and work with a licensed third party to properly retire existing products.
Attackers are constantly developing new hacking capabilities, and that means they can identify new security vulnerabilities your current firewall may not be equipped to handle. The right security will also inspect your entire IT network infrastructure to identify any possible security vulnerabilities, giving you the information you need to patch those weak points. You need to constantly update your security to be better prepared against emerging threats.
Partnering with the Right Security Provider
Cybersecurity incidents are on the rise, and it’s critical that your systems, networks, and processes are properly secured to ensure long-term growth and stability. That starts with having the right security professionals on your side.
Fortra’s Alert Logic’s team of security experts makes cybersecurity easy and effective. We work with you to gain an intimate understanding of your business and security needs to provide you with the tools and expertise to protect your organization’s data 24/7. All of this helps us develop an effective rapid response plan in the event of an attack.
Connect with us today to start on the journey to a stronger cybersecurity strategy.