Data security is critical to doing business in the digital economy. Companies are legally required to comply with a number of different data protection frameworks to handle customer data, including HIPAA, GDPR, and PCI DSS. However, most of those enterprises, don’t move past baseline requirements. This leaves data exposed to risk and can even damage the confidence of their customer base.
Service Organization Control 2 (SOC 2) compliance is a voluntary system that enables companies to take additional steps to protect client data. It signals to customers a willingness to invest more than they need to keep data safe and secure.
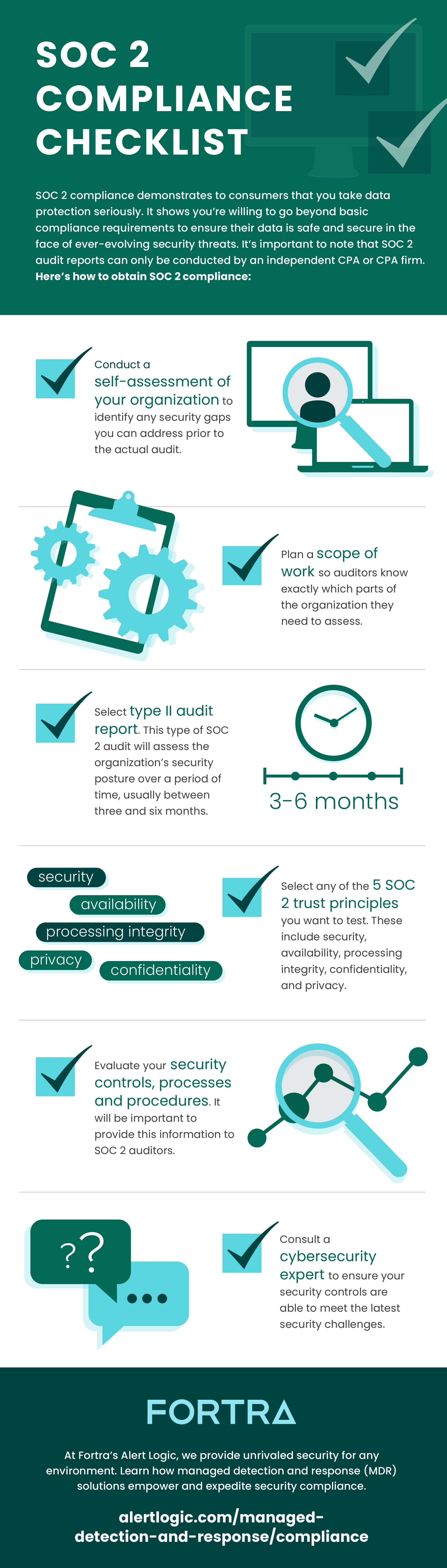
What is SOC 2 Compliance?
SOC 2 compliance was created by the American Institute of CPAs to help service providers better protect customer data and instill greater trust in their end customers. Licensed auditors perform SOC 2 audits who then provide an in-depth SOC 2 report to the service organization about their data management. This gives the organization critical, actionable insights they can use to make better-informed decisions about their data protection strategies.
Although SOC 2 compliance isn’t legally required, it’s important for service providers entrusted by customers to handle millions of pieces of private demographic information, contact details and online behavior information. Without a doubt, anything that causes customers to lose faith in an organization’s ability to handle that data — be it through a data breach, data loss or theft — can have serious long-term implications for the business. SOC 2 helps ensure data stays safe and customers remain confident.
5 Trust Principles of SOC 2 Compliance
1. Security
Ensures the proper access controls are in place to allow only authorized users to access critical data. Additionally, auditors test whether the proper security software is in place to protect against malicious actors.
2. Privacy
Denotes how client data is handled by the organization, including collection, use and disposal. Personal identifiable information — including anything that could be used to distinguish individuals — is considered critical and in need of extra privacy protections.
3. Confidentiality
Access to confidential data is required to be restricted to only those who need to use it. Encryption is one of the recommended methods for maintaining data confidentiality.
4. Availability
Helps make sure systems and operations are accessible to users based on the terms of the relevant service level agreement, enabling users with authorization to access the data.
5. Processing integrity
Systems, processes and applications need to work the way they’re designed to. To achieve processing integrity, it’s essential that data is properly cleansed and validated to ensure real-time accuracy.
How SOC 2 Compliance Benefits Your Business
Without question, data security is critical. Cybersecurity events have been on the rise in recent years, but they became particularly pronounced since the beginning of COVID-19. It’s clear that data security is essential to protecting consumer data and thwarting black-hat hackers. Check out these four ways businesses can benefit from SOC 2 compliance:
Brand reputation
SOC 2 demonstrates an organization takes data security seriously through extra steps ensuring controls are in place to protect data. In the modern digital economy, this helps brands build a reputation for trustworthiness among both new and existing customers.
Optimal service
Beyond protecting data, a SOC 2 audit helps organizations gain better visibility over their data stores. Data visibility helps them eliminate data silos to make their operations and processes more efficient, while at the same time leveraging their existing data for better business outcomes. All of this enables organizations to provide better quality and more efficient service to customers.
Increased revenue
Organizations are making an investment when they hire SOC 2 auditors. A SOC 2 audit can cost between $10,000 and $100,000. The combination of the aforementioned benefits helps service providers generate new business and optimize current customer relationships.
The Difference Between SOC 2 Types I and II
There are two different types of SOC 2 compliance, each ranging in cost, duration and scope:
SOC 2 type I
Type I reports provide details about an organization’s systems and internal control designs to make a judgment about their suitability to protect and secure data. Type I reports differ from type II in that they tend to provide attestation at a specific point in time, making them slightly more limited in their scope.
SOC 2 type II
Type II is similar to type I with the key difference being they provide attestation information across a 6-month period. Consequently, they are more comprehensive than their counterparts and provide a more detailed account of a service provider’s internal control systems.
The SOC 2 Audit Process
Although the process of conducting a SOC 2 audit can be long and cumbersome, the process itself is actually quite simple. Following are the four steps to completing a SOC 2 audit, according to Dash:
1. Security questionnaire
The SOC audit begins with the auditor asking questions about the company’s data protection policies, procedures and infrastructure. The purpose is to develop an understanding of how well attuned the team is to data security standards.
2. Gathering evidence
Auditors then ask for proof that the security policies and procedures actually exist. They use this information to understand the inner workings of specific security systems.
3. Evaluation
Auditors synthesize the documentation and information gathered and begin assessing it. If they uncover any security gaps, the organization may be required to take remedial action before the process continues. Auditors may follow up with team members to ask clarifying questions or seek additional information.
4. Report creation
Once the auditor completes the evaluation portion of the process, they submit a SOC report with their final assessment of the organization’s security standards. Organizations can use this information to make adjustments to their security infrastructure as needed to become SOC 2 compliant.
Sufficient data security starts with having the right team of experts on your side. Fortra’s Alert Logic cybersecurity professionals work with enterprises to learn their business and provide the technology and expertise for their unique security needs. We provide 24/7 protection to organizations to ensure they have the most appropriate response plan to confront whatever threats arise.
Learn more about our SOC 2 compliance solutions.