Cloud technology is in the DNA of modern businesses. It cuts the cost of data management, sets backups in place, and makes information available to anyone who needs it, wherever they are. Yet these advantages come with risks and responsibilities, requiring you to maintain strong protection over your systems. Your cloud data can’t be left vulnerable behind weak access points or poor vigilance. You must put effective cloud security measures in place to reduce your risk, allowing you to detect any threats early, address them quickly, and reduce any potential impact to the environment.
It’s been estimated that 30,000 websites globally are hacked every day. Misconfigured security, overly generous access settings, and exposed code will leave you vulnerable. This is even more dangerous in the cloud. After all, a single cloud data breach holds the keys to many other parts of your network. One mistake can compromise your entire environment.
In this blog, we’re examining how the scale and potential of cloud computing requires the absolute best protection you can find. Keep reading for a breakdown of cloud security: its threats, implications, and why they’re so critical.
What Is Cloud Protection – And Why Should You Care?
For starters, we must affirm that cloud security can never be boiled down to just one thing. Rather, it’s a web of technology, plans, and procedures that keeps your assets from being accessed or compromised by threat actors.
The cloud itself lets you store, find, and manage data on external hardware. Cloud security uses tools and stringent behaviors to ensure that information – whether created internally or handed over by your customers – remains safe. Generally, sound cloud security solutions involve:
- Passwords and user privileges. Everyone in your organization, from new recruits to senior leaders, will require at least some cloud data for their daily tasks. Precise levels of access are essential for putting that data in the right hands and nowhere else.
- Robust encryption that encodes and transcribes data for cloud storage. Plaintext transforms into something unreadable, so malicious actors can’t use it.
- Workload protection. You can’t just rely on protecting the endpoints (access points) throughout your network. Any work moving between cloud platforms needs to be secured while remaining usable.
- Security experts and automated software. Human expertise, together with automation, isolates and acts on threats before they become severe.
Public cloud providers such as AWS and Azure have their own security practices as part of their ownership in the Shared Security Responsibility Model (SSRM). But SSRM is a shared responsibility, and as such, you must adhere to your share of the responsibility. The potential cost of hacking, data theft, and accidental leaks is too devastating to be ignored. The global average cost of a data breach in 2024 was $4.48 million, a 10% increase over the previous year.
Leading Cloud Security Risks
We will never be able to drag every cloud security risk into the spotlight – these threats are changing constantly as more malicious agents hone their tactics and cloud platforms level up in complexity. However, we can identify some of the largest, ongoing risks to your data and operations.
Encryption, for example, can be a major headache. Three cloud service models – infrastructure, platform, or software – perform different tasks to encrypt your information. Your cloud provider has to deal with massive amounts of data that must stay healthy in the model you’ve chosen. Additionally, compliance changes with new territories. Other regulators might assess your data first, raising the chance of something being mishandled.
Meanwhile, it’s easy to forget about refreshing security protocols for cloud storage. Passwords, cryptographic keys, and multifactor authentication must be changed regularly. Any business that fails to automate these tasks leaves a blind spot in protecting its assets.
Beneath it all, you’re facing the insidious activities of hackers and scammers. Phishing emails may fool your employees into handing over sensitive information. DNS, SQL, and XSS attacks can disrupt service or bypass access controls. If someone hacks a gateway device, they probably have a clear way into your cloud network.
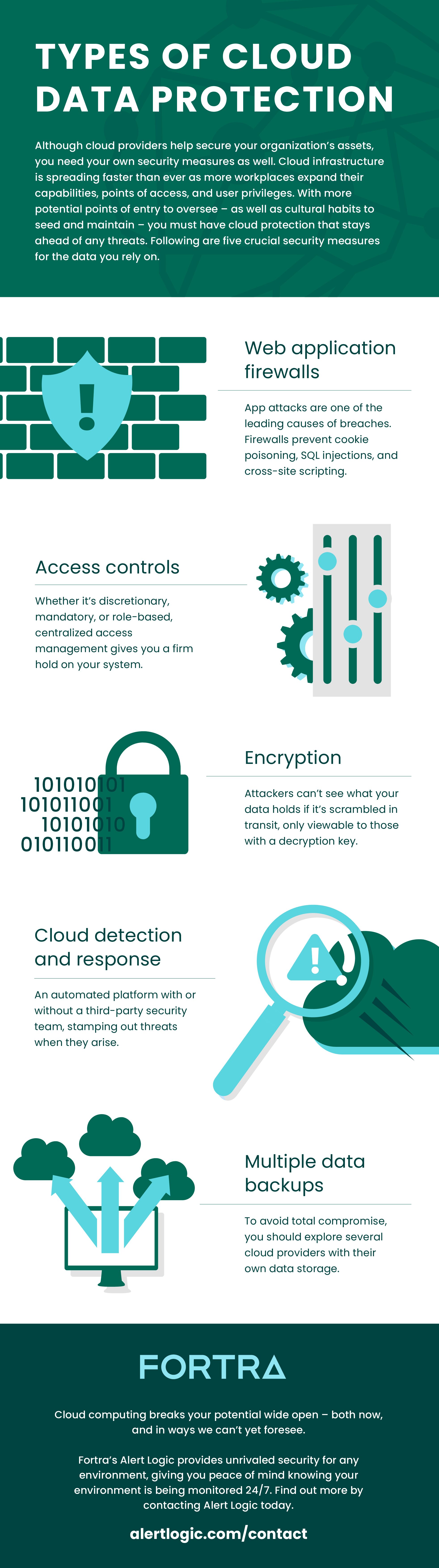
Types of Cloud Protection
On top of clear, continuous education for security in your workforce, there is much to explore for ironclad cloud protection. Here are a few solutions:
- Web application firewalls. These control all traffic from application servers, guarding against attacks such as SQL injections, cross-scripting, and cross-site request forgeries. Unlike regular firewalls, you set the boundaries of what may constitute a threat.
- Detection and response for cloud workload protection. When you unify this security across all providers, you safeguard container events – the small units of software that package up libraries, code, and configuration files.
What You’ll Gain from Cloud Security
Cloud technology is a powerful asset for anything you’re hoping to accomplish in the digital realm. And with sufficient protection, you can make the most of these wins without worry. More specifically, though, what do those successes look like with a cloud security provider on board?
Chiefly, you’ll reduce the risk of compromise in your environment. Business practices can run on reliable information, accounts, and access privileges without fear of losing them. While no organization is immune to cyberattacks, having the proper security controls in place greatly reduces your risk. Customer information, as well as your own, stays where it’s meant to be, ultimately helping you maintain a strong reputation.
As threats are dealt with, you’ll be able to scale up or down with server demand, a crucial service for maintaining protection as your business grows. You aren’t just vigilant against threats today, but any that may surface in the grand scope of your goals.
Fortra’s Alert Logic can help you lock down cloud security concerns along the way. Learn more about our cloud leadership.