SOAR (security orchestration, automation, and response) leverages automation, orchestration, artificial intelligence, machine learning, and advanced analytics to centralize and streamline critical threat intelligence, empowering organizations to tackle potential security risks swiftly and effectively. By automating responses, organizations can significantly reduce their mean time to respond (MTTR), minimizing the impact of security incidents and enhancing overall resilience.
Automation and orchestration lie at the core of SOAR capabilities, empowering SOC teams to accelerate response times by automating time-consuming tasks. This enhances efficiency, allowing them to devise stronger, more agile strategies for tackling any threat that could jeopardize their organization.
An essential element of Fortra XDR and Alert Logic MDR, our automated incident response provides a flexible, scalable and integrated approach to protect your entire IT estate. Through a combination of automated response and expert guidance, Alert Logic delivers the options you need to reduce time-to-resolution for security-strapped teams before any serious damage impacts your business.
With our incident response, you can align the correct use cases to the needs of your business, including:
- Isolate host — Block incoming and outgoing network activity of an endpoint
- Disable credentials — Block usernames and passwords from accessing the network
- Shun attacker — Block an external IP attack by updating a rule at the network edge
Detection Strength & Broad Coverage
Effective response strategies rely on robust detection, which demands both comprehensive coverage and depth. Alert Logic detection harnesses advanced threat research and intelligence to perform in-depth threat analysis. It also integrates machine learning and incident enrichment to assess and understand risks more thoroughly. This is complemented by extensive coverage across all environments — ingesting logs and collecting telemetry data from every corner of your infrastructure, including endpoints, cloud, network, and identity providers.
Embedded SOAR Capabilities
Alert Logic’s automated incident response provides you with the ability to:
- Trigger response actions including blocking, containment, and host isolation based on the type of attack and asset targeted
- Notify appropriate personnel for human decision before executing action
- Complete audit trail of all automated actions taken
You determine the appropriate response, and Alert Logic makes it happen.
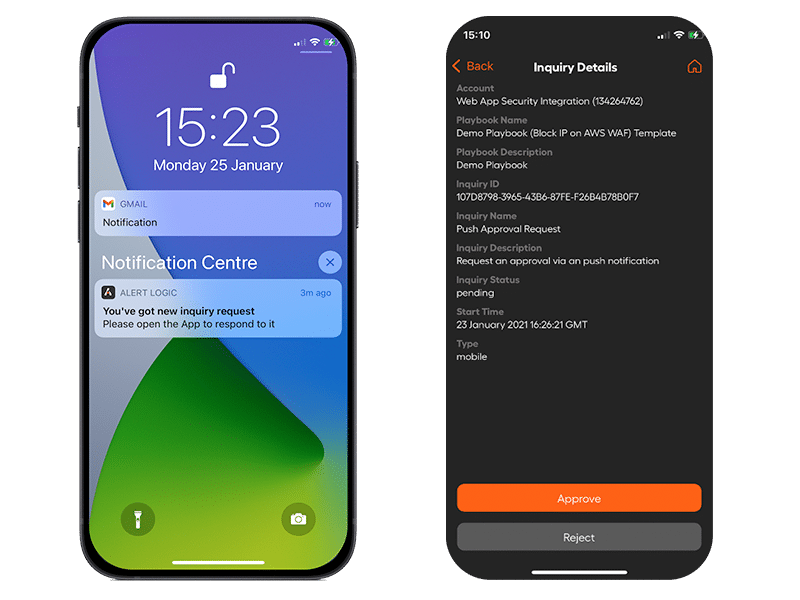
Balancing Automation &
Human-guided Response
In multi-cloud environments, organizations require solutions that minimize damage of a breach with the right balance of automation and human interaction. This flexibility enables you to adopt automation at your own pace: full automation streamlines workflows to enable response actions across network, endpoints, and cloud environments while human-guided automated provides much-needed context to deliver better outcomes. Alert Logic automated incident response provides:
- Wizard-based workflow templates
- Timely human approval using Alert Logic’s mobile app
- Test integration points for response action
Incident Response Resources
SOLUTION BRIEF




