Identifying and responding quickly to attacks is a must. Alert Logic’s combination of a proven security platform, leading threat intelligence, and expert defenders provide the comprehensive coverage you need delivered in a SaaS model.
And with our global Security Operations Center monitoring your systems 24/7, you’ll have peace of mind knowing your IT environment is secure. Our team leverages a diverse range of data collection and analytics methods for rapid threat detection.

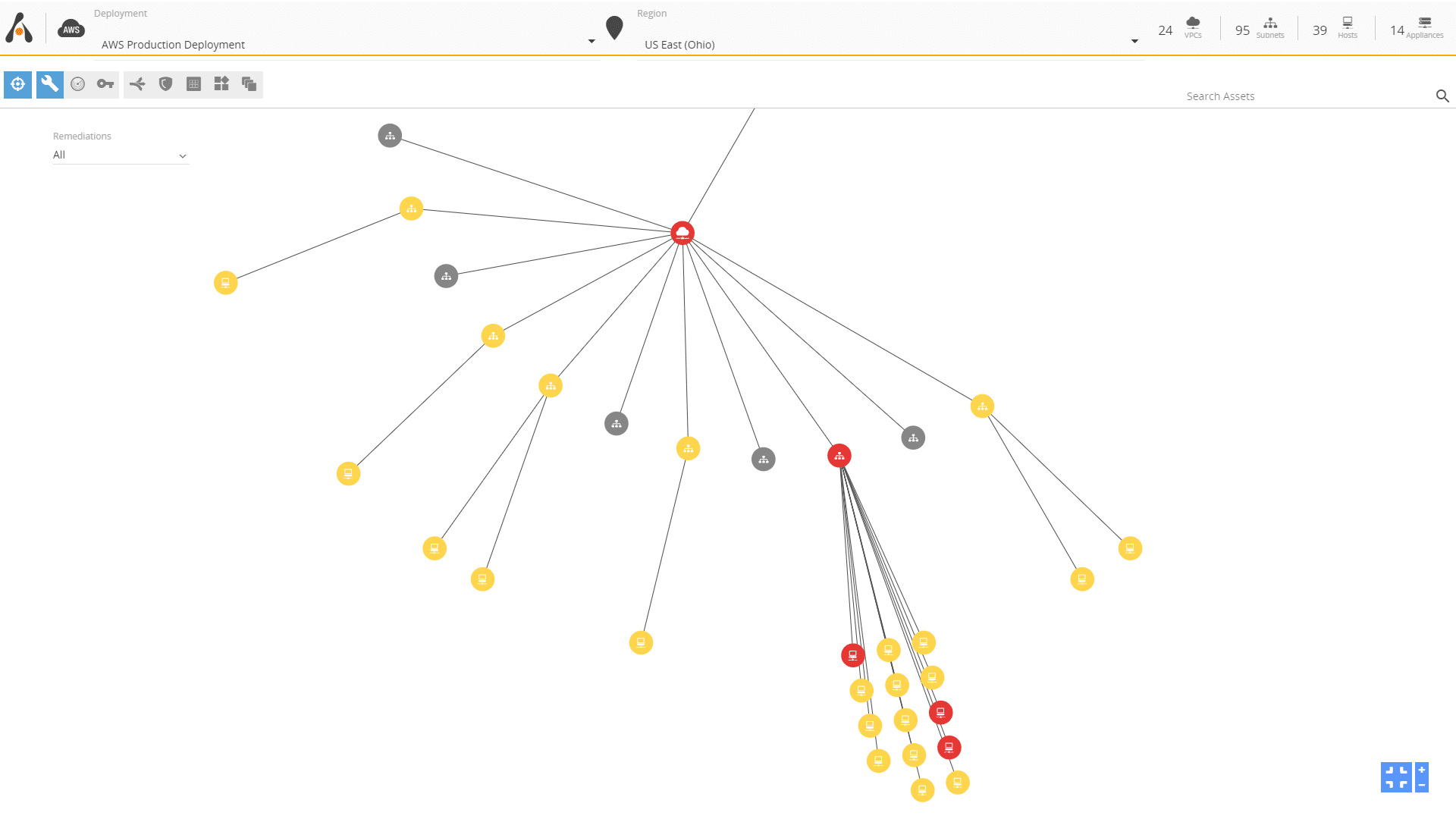
Reducing the Likelihood of Successful Attack
With Alert Logic’s managed security services, your assets are continuously and automatically discovered, analyzed, and assessed for risks. Our platform identifies vulnerable systems and configuration flaws that leave you exposed to potential attacks. Armed with this critical insight, your team can swiftly take action to eliminate weaknesses and prevent breaches before they happen.
Every day, new threats emerge, putting your systems at risk. To stay ahead, we deploy cutting-edge threat-hunting techniques, sifting through vast data sets to pinpoint vulnerabilities. We alert you to your most at-risk assets and collaborate with you to proactively stop attacks before they strike.

Reducing the Impact of a Breach
Our security experts are always on alert for the possibility of a breach. We’re constantly innovating, refining detection methods, and deploying cutting-edge techniques designed to deliver tangible, real-world advantages for you.
The diversity and depth of our customer base strengthen our defense against threats, turning every attempted attack into valuable insight. By learning from each encounter, we deliver ongoing, enhanced protection to our entire community.
