The global cyber insurance market experienced unprecedented growth in recent years with companies looking to bolster their recovery from a potential cyberattack. Projections indicate that the cyber insurance market will grow from $8 billion in 2020 to over $20 billion by 2025.
Securing cyber insurance, however, is not a straightforward process. Cyber insurers are raising the bar to obtain a policy, including having detailed information on an organization’s security posture, detection and response tools, and security team.
Understanding and aligning with insurers’ requirements has become crucial for a successful cyber insurance policy application. In this blog, we review key areas that impact your security posture and that most cyber insurers will want to be able to see demonstrated proof of when you apply for a policy.
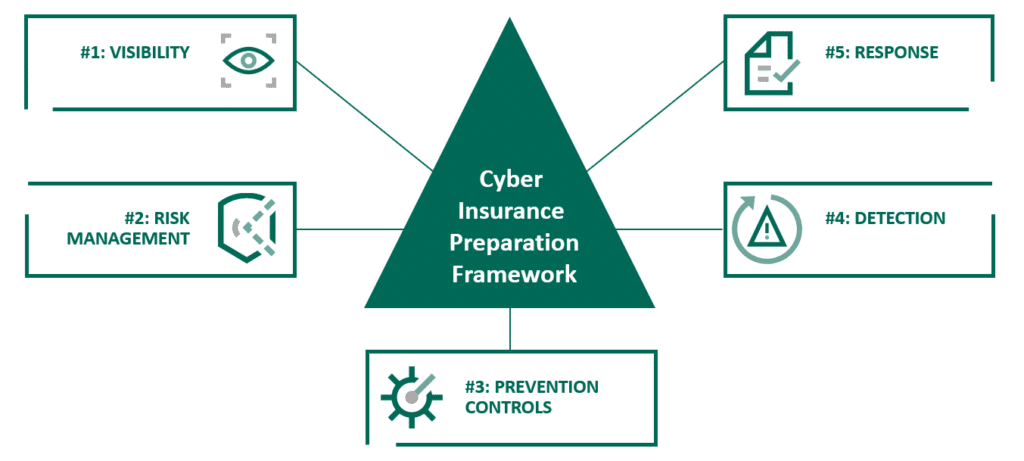
The 5-Step Framework for Demonstrating Cyber Insurance Requirements
In responding to a cyber insurance application or answering questions during a meeting, you’ll need to show you have the breadth and depth of security controls that you’re using to their full extent. Simply ticking boxes that say you have a tool, process, or procedure will not do. Additionally, if you’ve taken a “set it and forget it” approach to your cybersecurity – you’ve implemented a system, but you never review or improve your security controls – you’re likely to be denied a policy.
What is key to demonstrate that you’ve gone beyond simply implementing a security strategy? How can you demonstrate your security posture manages the defense of your business? Do you have full visibility into your entire IT estate, being able to identify threats and exposures quickly? Have you utilized your security solution to really drive identified security outcomes?
Through our work with customers and partners, we’ve devised a five-step framework to help prepare for a cyber insurance review. These five tenets can be used well beyond evaluating your security posture before applying for cyber insurance.
1. Visibility
At the core of any effective security posture is visibility. Simply put, you need to understand what it is that you’ve got if you’re going to adequately protect it. Environments are constantly changing, so you need to ensure you maintain visibility as your environment evolves. Understand where your data is, its importance to your organization, and who is interacting with it.
Among the questions you’ll be asked related to visibility include:
- Do you have an asset discovery tool?
- How frequently does it update your asset inventory?
- What level of visibility does it provide at a network or host level?
- What is the process for assigning criticality to identified assets?
- What is the process for adding new technology to the tech stack?
- What is the process for end-of-life products within the tech stack?
Minimum visibility cyber insurance requirements can include your organization’s data and asset discovery process, data and asset classification, and telemetry for 24/7 threat monitoring. Additional capabilities, such as penetration testing and application security testing, enhance your appeal as a cyber insurance client as they prove how effective your visibility strategy is.
2. Risk management
Understanding your organization’s risk appetite throughout your IT environment is a critical step in developing and maintaining your security strategy. You need to ensure you have alignment between security controls and acceptable risk by prioritizing and addressing critical components that can cause business interruption.
Questions that an insurer may ask:
- How do you enable remote access to company resources?
- How do you handle privileged users?
- Show me how you measure risk.
- Show me how you identify and remediate vulnerabilities and misconfigurations.
- What is your policy for employee-owned devices?
From a minimum risk management requirement perspective, an insurer will expect your organization to use multifactor authentication (SMS based), vulnerability management, network segmentation, and privileged access management (PAM). Being able to demonstrate a strategy that exceeds the minimum requirements could include using an authenticator app or security key for MFA rather than SMS.
3. Prevention controls
Prevention controls are key to stopping threats from progressing because it is impossible to take your risk level down to zero. These controls not only prevent threat actors from getting in by blocking attacks but also ensure that the right people are collaborating with you and your assets through positive policy enforcement.
Questions you should be prepared to answer on a cybersecurity application include:
- How do you protect customer data?
- What controls do you have in place for incoming email?
- What preventive controls do you have on the endpoint?
- How often do you evaluate the effectiveness and tune your preventive controls?
Minimum prevention controls can include having an endpoint detection and response (EDR) solution, secure email gateway, integrated data loss prevention (DLP), and a web application firewall (WAF). Having enterprise-class DLP, port security, and ongoing monitoring and tuning can make you a more attractive cyber insurance candidate.
4. Detection
If a threat can be prevented from progressing then it should be, but we all must accept there just is no such thing as 100% prevention. You need to ensure you have mechanisms in place across your entire IT estate to detect unwanted activity quickly which may slip through or bypass your preventive security controls.
Among the questions you may be asked related to detection include:
- What are your threat detection capabilities?
- What is the process for handling security events and incidents?
- Do you have a 24/7 security team?
- Show evidence of worked detection alerts.
Minimum detection capabilities insurers may look for include having an IDS and log, web application security, and use of a SIEM, XDR, or equivalent platform for analytics and investigations. You can stand out in your detection process if you can demonstrate higher level detection functions like threat hunting activities. Metrics on your mean time to detect threats may also influence your quote, as quicker detections limit the attacker’s potential for damage.
5. Response
In terms of response, how are you acting when you receive a detection alert? For response, having both automated and manual responses actions are crucial. Your ability to demonstrate swift and comprehensive response recovery to normal business operations will be a factor.
Questions to prepare for in terms of response include:
- When was the last time you had to deal with an incident and what were the results of your response?
- Describe your backup and recovery plan.
- Do you review your security incidents to determine how you might prevent/detect something further upstream next time?
Minimum response requirements may include documented incident response plan and a backup and recovery plan. Automated response actions, a tested incident response plan, and tested backup and recovery plan may help you stand out as an attractive candidate to the insurer.
Navigating the complex terrain of cyber insurance requires proactive measures. By addressing the five steps outlined here, organizations not only enhance their chances of securing cyber insurance but also fortify their overall security posture against potential threats.
Learn more about leveraging enhanced security posture to help win with cyber insurance with this on-demand webinar and check out how a managed detection and response (MDR) solution may be the answer to improving your security posture.