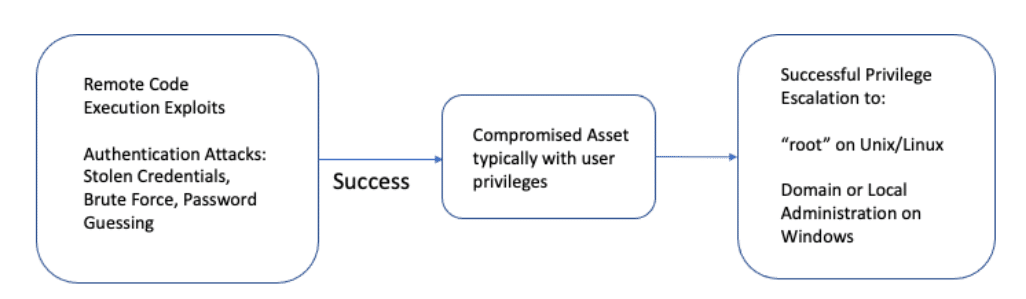
Privilege escalation vulnerabilities allow attackers to successfully elevate their access to a targeted asset. The attackers’ objective is to obtain complete control over the targeted asset by gaining “root” access in Unix/Linux environments and Domain/Local Administrator access in Windows environments.
Privilege escalation vulnerabilities by themselves are generally never ranked at the highest level on the Common Vulnerability Scoring System (CVSS). For example, the privilege escalation vulnerability announced yesterday for Unix/Linux systems in the “Polkit” system tool (CVE-2021-4034 dubbed PwnKit) is rated at 7.8. In comparison, the recent Log4Shell vulnerability was rated at max CVSS criticality of 10.0. So, what makes Alert Logic Threat Intelligence activate our Emerging Threat Process for some privilege escalation vulnerabilities?
Chaining of Exploitation
The answer lies in the cumulative impact on any environment from the chaining action of vulnerabilities, often used by cybercriminals, including ransomware gangs. The chaining of exploitation leads to the same criticality as CVSS 10.0.
In any given environment, despite the best attempts at reducing the attack surface, there is always a set of systems that need to be patched or have mitigation actions applied. In addition, there are continuous attempts to break into the environment via authentication attacks, from using stolen credentials to password guessing attacks.
The worst aspect of privilege escalation vulnerabilities is that compromising a user device (laptop – workstation) can potentially lead to compromise of the entire environment, including servers.
IT Teams are not yet done with the Log4Shell patching work that has the broadest known attack surface in recent times. The emergence of the PwnKit bug at this time will prove to be a harbinger of multi-stage attacks with complete compromise of any vulnerable systems. The exploit for PwnKit is out in public – it is easy to get root shell in seconds. Given that this bug has been discovered after existing for 12 years, it is likely that the vulnerability may have been already exploited underground.
Has There Been a Precedence of These Multi-stage Attacks for Other Privilege Escalation Vulnerabilities?
Yes, yes, and yes. Across both Linux/Unix and Windows environments.
ShellShock is an older example from 2014, when it was widely exploited on Linux/Unix systems.
And let’s not forget the more recent Windows Zerologon vulnerability from 2020. As described in a previous blog post, ransomware authors have been successfully exploiting this vulnerability to reduce the time taken to compromise an environment for ransomware from days to hours.
Microsoft released patches for two privilege escalation vulnerabilities in November 2021: CVE-2021-42287 and CVE-2021-42278 – Active Directory Domain Services Elevation of Privilege. These are easily exploitable for becoming the ruler of the entire Windows domain!
What is Needed to Best Detect These Classes of Vulnerabilities?
If a vulnerability by itself or in combination with multi-stage attacks poses a risk for our customers, we activate our Emerging Threat Process (all the specific detections and progress for the PwnKit vulnerability can be found here). But what is needed for Alert Logic to detect such vulnerabilities?
Laser sharp analytics
In general, we leverage the logs collected by the Alert Logic agent on Unix/Linux systems and Alert Logic’s Analytics Engine to craft analytics for threat hunting and incident creation for our customers. Specific detections for PwnKit have also been added to our vulnerability scanning.
Broad, generalized solutions
We also look at generalized solutions that can detect the lateral movement emerging after privilege escalation. This is an area where Machine Learning based techniques have been used to detect anomalous activity in a Windows environment. The aim of developing these generalized analytics is to provide futureproofing against new privilege escalation exploits (i.e. 0-day coverage for our customers).
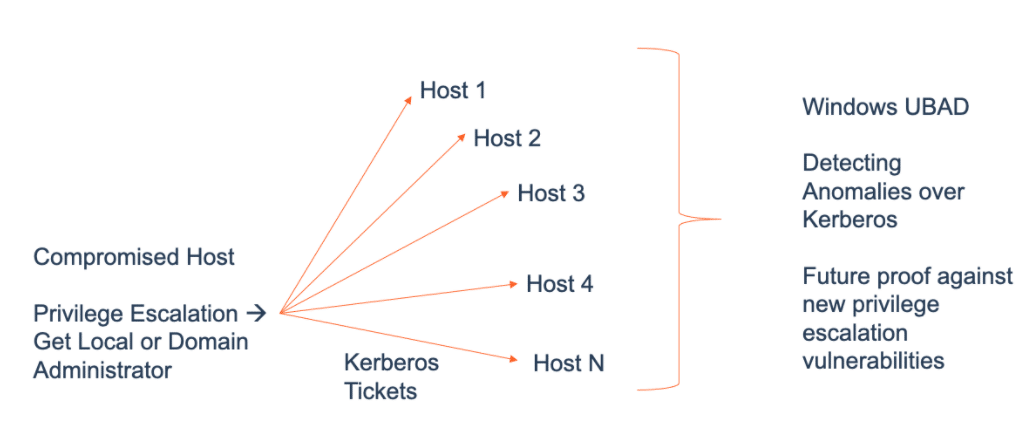
The machine learning based analytics released in Dec 2021 detects anomalous Kerberos activity.
In summary, our Threat Intelligence and SOC teams are working 24/7 to detect any breach activity along the kill chain, either via laser-focused detection on specific vulnerabilities or by leveraging machine learning and other techniques for generalized coverage of a class of vulnerabilities.
This is the secret sauce that powers Fortra’s Alert Logic MDR.
For the specific detections and progress of the PwnKit vulnerability, visit our Knowledge Base article.