4 minute read
Ever hear the joke about outrunning a bear? There are various versions, but I like:
“A bear jumps out of a bush and starts chasing two hikers. They both start running for their lives, but then one of them stops to put on his running shoes. His friend says, “What are you doing? You can’t outrun a bear!” His friend replies, “I don’t have to outrun the bear; I only have to outrun you!”
When it comes to cybersecurity every organization is a hiker, and cyber attackers are the bears—bears with endless stamina. And if you think you aren’t being chased, think again. Attackers care about ROI just as much as you do. They embrace scaled, automated tools and scripts to find quick and easy targets anywhere they can. There is an endless supply of easy targets for attackers to cash in on—from small companies to large organizations who spend enormous amounts of money (researching / planning / deploying, tuning) on advanced “next generation” security solutions (ahem…SIEM) to detect and stop sophisticated, targeted attacks.
I’m not saying that you shouldn’t worry about targeted attacks, of course you should—you never know if or when you might be targeted. However, everyone is subject to automated attacks, always. So, it is equally important to ensure that you continuously address the basics to protect your organization from automated attacks that easily exploit vulnerable assets (configuration issues, missing patches, weak passwords, no encryption, promiscuous access control privileges). Most organizations will say that they have all the basics addressed—that they aren’t worried (hello Equifax hack).
Top Amazon GuardDuty finding types seen by Alert Logic customers
Here’s a great example to validate the automated activity from attackers. We have a new software-as-a-service offering called Cloud Insight™ Essentials for AWS that integrates with Amazon® GuardDuty™. It helps customers respond faster to suspicious activity reported by GuardDuty (reconnaissance activity, compromised instances, and actively compromised accounts). New customers quickly notice and ask why they are seeing so many of these particular findings:
#1
Recon:EC2/PortProbeUnprotectedPort
indicates that an EC2 instance has an unprotected port that is being probed by a known malicious host
#2
Recon:EC2/Portscan
indicates that an EC2 instance is performing outbound port scans to a remote host, a possible port scan attack
#3
UnauthorizedAccess:EC2/SSHBruteForce
indicates that an EC2 instance has been involved in SSH brute force attacks to obtain passwords to SSH services on Linux-based systems and can lead to unauthorized access to an AWS resources
#4
UnauthorizedAccess:EC2/RDPBruteForce
indicates that an EC2 instance has been involved in RDP brute force attacks to obtain passwords to RDP services on Windows-based systems and can lead to unauthorized access to an AWS resource
Here is an example of an UnauthorizedAccess:EC2/SSHBruteForce attack detected by GuardDuty seen in the Alert Logic® Cloud Insight™ Essentials console. This activity was detected within minutes of launching the EC2 instance.
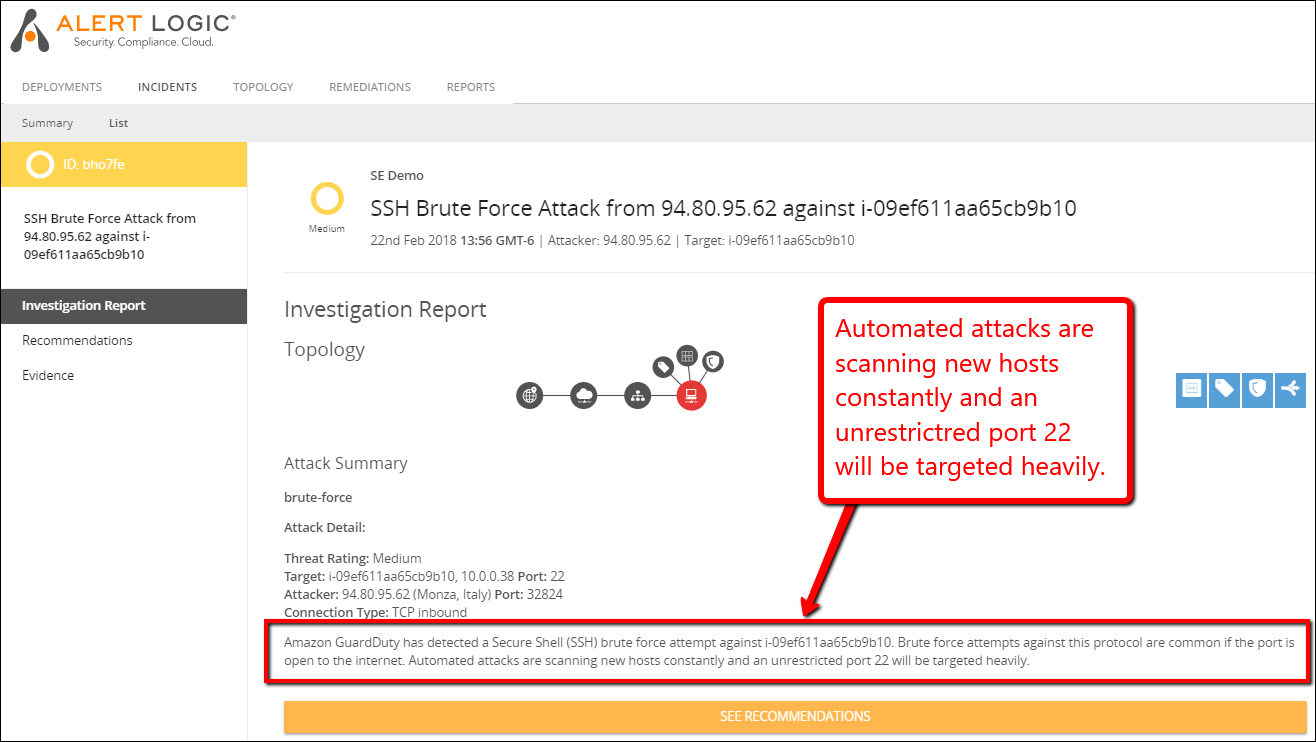
gd incident brute force
It is important to pay attention to the basics when it comes to securing your assets. Perhaps the basics would get more attention if we called them Advanced Persistent Exploit Automation (APEA?), but for now we’ll call them Best Practices (sorry) and refer to the Center for Internet Security for their Top 20 recommended security controls for securing organizations against today’s most pervasive threats.
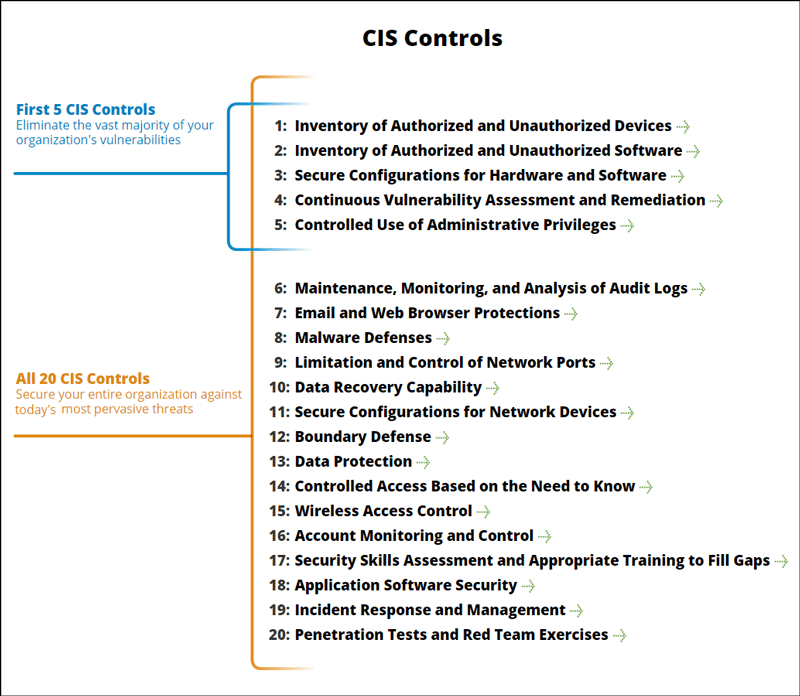
CIS Controls
The intersection between the top 4 Amazon GuardDuty finding types that customers frequently see and these top 5 CIS Controls is not a coincidence (they are called Best Practices for a reason). While many of these were born out of on-premises environments, most of these are relevant for cloud environments, especially the top 5.
What you can do about cloud workload protection (outrun your buddies)
If you have workloads deployed on AWS, we know that opportunistic attackers are going to endlessly probe for specific AWS misconfigurations and software vulnerabilities to exploit. To keep them from getting a return on their investment, it is critical that you continuously:
- Detect and monitor all your workloads deployed on AWS, especially in accounts or regions where there are frequent changes and additions by team members with privileged access.
- Inspect the configurations of your AWS services (S3, IAM, EC2, ELB, IAM, Encryption Keys, Security Groups, Subnets etc.), and every single deployed EC2 instance.
- Scan for vulnerabilities, configuration issues, and missing patches in the software you deploy—patch/upgrade as soon as possible, at the AMI level when applicable.
- Identify unnecessary admin privileges for all your services and workloads deployed in AWS—restrict access on a least privilege basis.
How we can help you with cloud workload security
We save you a huge amount of time and frustration (and potential errors) with our automated AWS Vulnerability Scanning Service. It will automatically discover all your assets, check for misconfigurations and vulnerabilities and give you guidance on what to fix first and how to do it.
Plus, if you have Amazon GuardDuty, it will make it easier to understand and respond to GuardDuty findings. It is free for 30 days, and only costs $49 a month per AWS account after that (no contract required). You can launch it and start seeing results in minutes by going to AWS Marketplace.
.
