Information is currency in today’s digital world. It must be kept secure like cash or any other valuable asset. Governments worldwide recognize the need to safeguard sensitive data and have introduced legislation aimed at protecting it.
Organizations that do the minimum to meet the requirements these laws established leave data potentially vulnerable to exposure and attack. That’s why the American Institute of CPAs created Security Organization Controls (SOC). So, what is SOC compliance?
Simply put, it’s a voluntary system that allows businesses to enhance their information security and protect their customer data. SOC 2 compliance shows customers and partners that you prioritize data security and follow security best practices. To become compliant, organizations apply to licensed auditors to undergo an SOC 2 compliance audit. The audit examines their data protection systems and strategies. Those that meet the mark are officially deemed compliant.
Are you considering evaluation for SOC 2 compliance? Here are a few things to consider for a smooth and useful process SOC 2 compliance evaluation.
A Checklist for SOC 2 Compliance Success
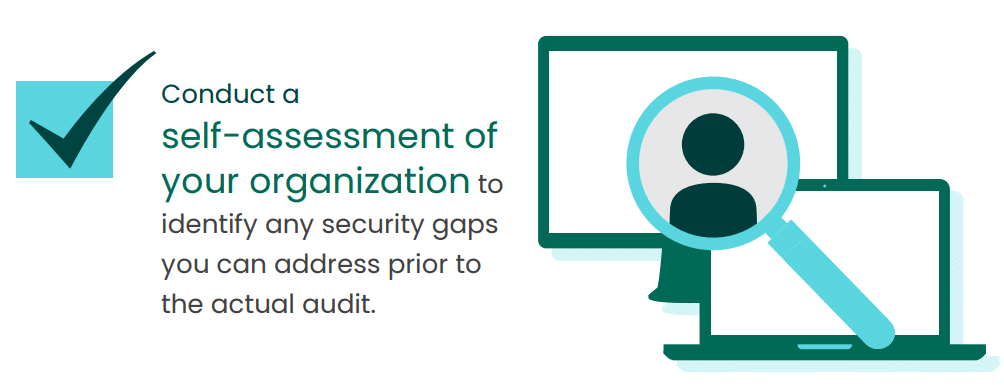
Start with an internal self-assessment based on SOC 2 compliance requirements before reaching out for an independent SOC 2 audit. Actions like penetration testing and scanning for unauthorized access allow you to determine if there are pre-existing security issues with any given internal control you can rectify before the auditor begins their inspection. This saves both you and the auditor time as you don’t need to wait for the SOC 2 report before making major adjustments.
Every business is unique and has different areas of concern. Developing a scope of work can enable auditors to concentrate on the most important parts of the organization. This avoids unnecessary aspects that aren’t critical to the company. You should decide which facets of your business are the highest priority and require the most attention and care.
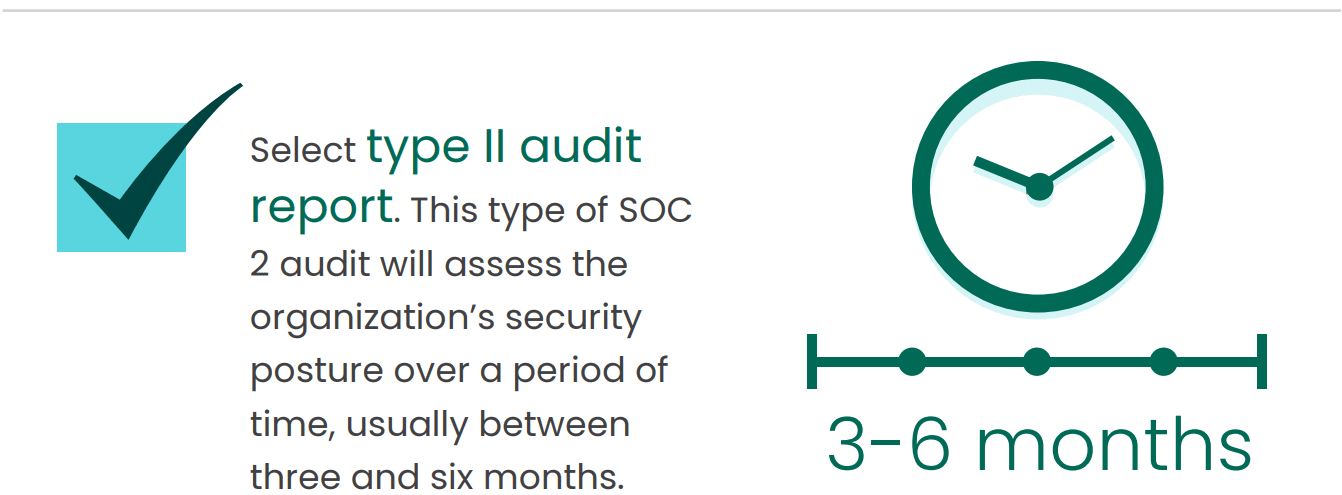
Selecting a Type II audit means assessing your organization’s security posture over a specific period (typically three to six months). Moreover, a Type I audit looks at security compliance at just one point in time. Type II audits analyze the controls an organization uses to safeguard customers’ data and how they perform during that specified timeframe.
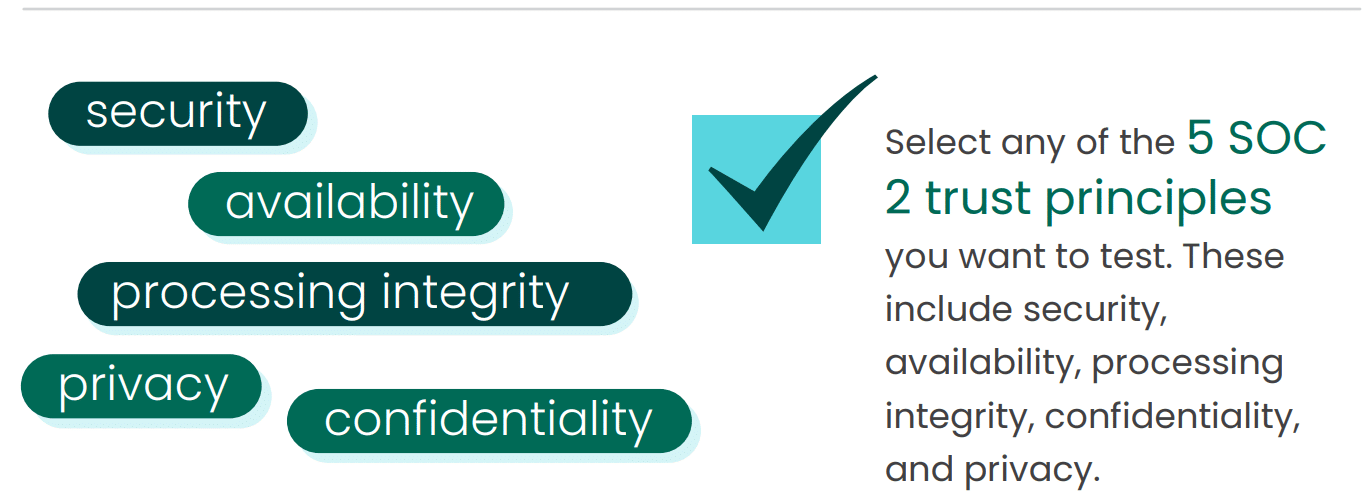
SOC 2 is built on five primary categories (also called trust services criteria): security, availability, processing integrity, confidentiality, and privacy. Each trust principle looks at a different aspect of data protection, and you choose which ones you want assessed. Your selection depends on the kind of data you have, what you use it for, and who has access to it, as well as your organization’s industry. These criteria often necessitate special regulatory compliance. For example, a company contracting with the government has different compliance requirements than one servicing private clients.
While your auditor’s findings ultimately determine your compliance status, you must provide the auditor information about your security strategy, protocols, and measures. This information will give the inspector a baseline understanding of the company’s current security posture, which is crucial in directing them during the auditing process. You also must furnish evidence as proof that your policies exist and are implemented.
Irrespective of whether you receive your SOC 2 certification, meet with a cybersecurity expert to determine whether your controls can withstand recent developments in cybercrime. Attackers’ methods and end-goals evolve constantly. So, it’s imperative that you consult with professionals to determine if your security controls are up to scratch. Don’t let any given safety measure lull you into a false sense of security. Every single program and plan must be up to date.
Fortra’s Alert Logic understands your organization’s security needs are as unique as your business. That’s why we take pride in our in-depth customer collaboration to understand their requirements and what solutions would be best for their operational environment. As a service provider, we know SOC 2 compliance isn’t the easiest thing o achieve, so we’re here to help you throughout your journey to ensure your security posture meets your compliance goals. Request a MDR demo to see our services in action.