The Importance of Container Security
Container security is more vital than ever as the explosive growth in container adoption fuels a surge in security threats. From access control weaknesses to privilege escalations and sophisticated malware attacks, the expanding reliance on containers calls for robust, proactive measures to safeguard your systems.
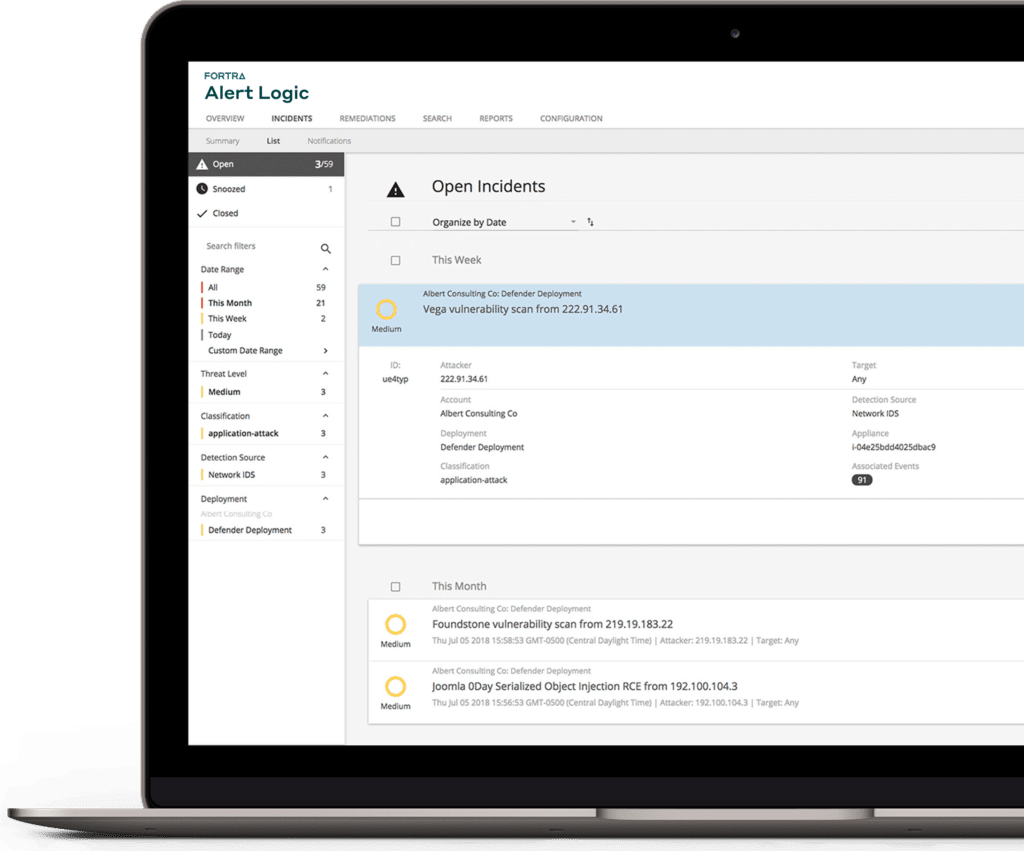
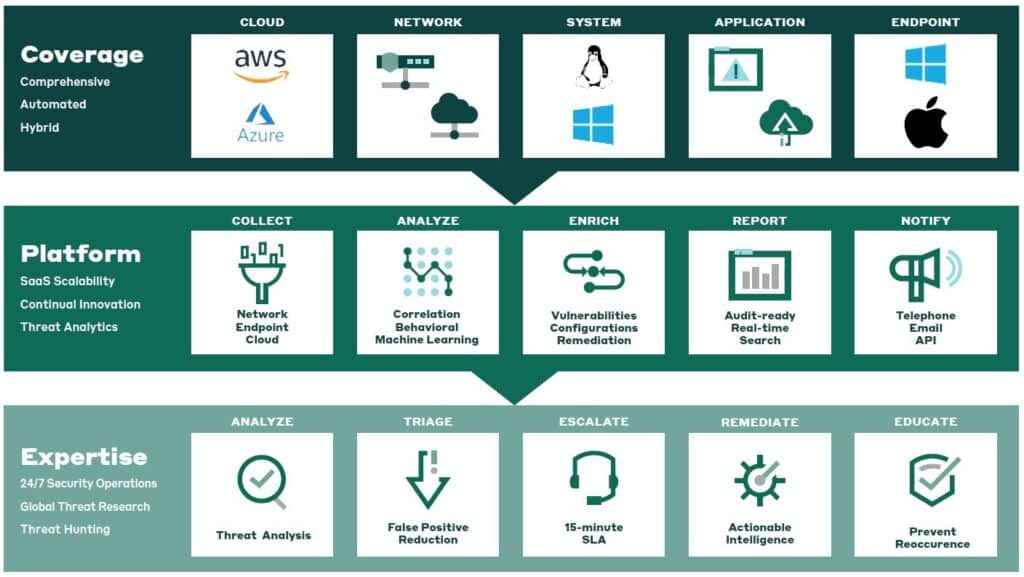
We deliver the industry’s leading network intrusion detection and log management solution purpose-built for containers. No matter where your workloads operate — AWS, Azure, hybrid, or on-premises — our platform ensures real-time cloud environment is always protected, giving you unmatched peace of mind.
- Detect cyberattacks in real-time by analyzing the signature of data packets as they traverse your containerized environments
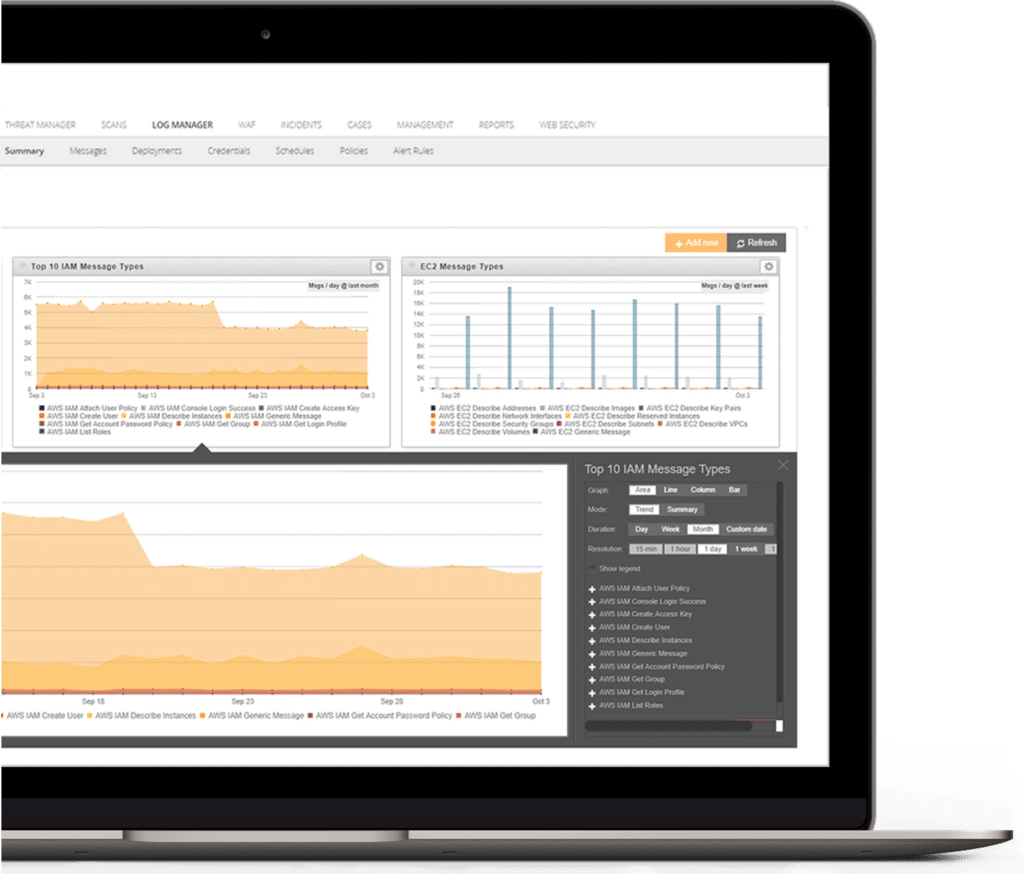
- Collect, aggregate, and search container application logs to gain insight into container activity for optimal security and compliance
- Ensure your security is as adaptable and portable as your containers, seamlessly spanning cloud, hybrid, and on-prem environments
- Build a better view of security impacts with a container topology visualizing the compromised container and its relationships
- Review analysis of host network traffic and communications to, from and between containers
- Get real-time alerts when active exploits threaten your container ecosystem
Protect your containers with Fortra XDR and Fortra’s Alert Logic MDR
Protection Across
Your Container Network
Stop cyberattacks targeting your cloud, hybrid, and on-prem containers from cyberattacks with advanced detection of both known and unknown exploits, along with container-native vulnerabilities.
Protecting Container Services
Docker & Docker Swarm
Learn more about
Docker Security >
AWS
Fargate
Learn more about
Fargate Security >
Amazon ECS
& EKS
Learn more about
Amazon ECS & EKS Security >
AWS Elastic Beanstalk
Learn more about
Elastic Beanstalk Security >
Kubernetes
CoreOS
And Their Hosting Environments
AWS
Azure
Google Cloud Platform
On-Premises
Container Security Case Studies
accesso uses containers to deploy and manage apps and needed a partner with cloud container expertise. Read accesso’s story >
RunBuggy wanted a security solution that would enable a full view of their expanding AWS infrastructure and containers. Read RunBuggy’s story >