Vulnerability Scanning & Assessment
Our network vulnerability scanner is a cornerstone of Alert Logic’s managed security services — because you can’t protect what you can’t see. We help you:
-
Track changes in your environment including additions, moves, and deletions
-
Uncover gaps in network and service layers that could lead to compromise
-
Take action with expert guidance on remediation and mitigation
-
Simulate real-world attacks and run comprehensive vulnerability checks, including registry evaluation
How Does a Vulnerability Scanner Work?
A network vulnerability scanner uncovers and identifies critical network and host vulnerabilities within your environment. It simulates external attacks and conducts thorough vulnerability assessments, including registry analysis. All environments – including AWS and Azure workloads, web apps, and APIs – can be scanned with Alert Logic.
Alert Logic conducts comprehensive scans across all assets in your deployments:
- For new deployments, Alert Logic automatically sets up default scan schedules tailored to the deployment type, ensuring agent-based, internal network, and external network vulnerability scans are carried out on all assets and ports, except those marked for exclusion.
- For data center deployments, a default discovery scan schedule also is established to detect new assets.
- Customers have full flexibility to schedule specific scans for all or selected assets and ports, giving you control over when critical security checks occur.
With Alert Logic, you can receive instant notifications for threats, changes, and scheduled events in your environment, empowering you to take swift action. Customers can subscribe to both alert-based and scheduled action notifications; for alert-based notifications, easily customize the criteria to focus on critical threats, allowing you to prioritize high-risk situations and respond effectively.
Types of available network scans
- Agent-based: Improves vulnerability assessment by providing authenticated network scanning without the need for credential management. It reduces network traffic and minimizes impact, enhancing efficiency, accuracy, and usability in Alert Logic’s vulnerability scanning. It also significantly boosts the reliability and precision of scan results.
- Internal Network: Runs from an Alert Logic appliance in your environment, these scans can be done without credentials (unauthenticated) or with credentials (authenticated). Without credentials, your network is scanned by bypassing host login and utilizing exposed ports, protocols, and services to detect vulnerabilities, misconfigurations, and default account exposures. With credentials, Alert Logic can access each host on your network, gathering information while conducting thorough vulnerability assessments, including registry setting analysis, identifying misconfigurations, and detecting missing patches.
- External Network: Runs from the Alert Logic data centers targeting your internet-facing environment, this scan simulates external attacks to uncover vulnerabilities and potential risks posed by these threats.
- Asset Discovery: Uncovers assets and configurations, providing essential insights so you can make informed decisions on what to protect and the level of protection required. Achieve full visibility into all assets and environments for enhanced asset management and improved security outcomes.
- PCI Scanning: As a PCI ASV, our scans meeting the requirements of PCI DSS 4.0, 11.3: “Perform network vulnerability scans by an ASV at least quarterly or after any significant network change” (includes 11.3.1, 11.3.2).
Scanner Features
Quickly discover and visualize weaknesses in your deployed assets with regular automated network vulnerability scanning and health monitoring:
- Identify 91,000+ network security vulnerabilities and 8,600+ software configuration issues in all your environments
- Identify internet-facing vulnerabilities in web applications
- View detailed operating system, port configurations, services, and certificates for each asset
- Identify OWASP Top 10 vulnerabilities in custom-built or commercial apps with PCI ASV-level vulnerability scanning service
- Get a comprehensive list of missing security patches, unauthorized applications, and vulnerable network configurations.
- Detect vulnerabilities missed by agent-based scanners with virtual network vulnerability scanner appliances that scan anything with an IP address
See the vulnerability scanner in action
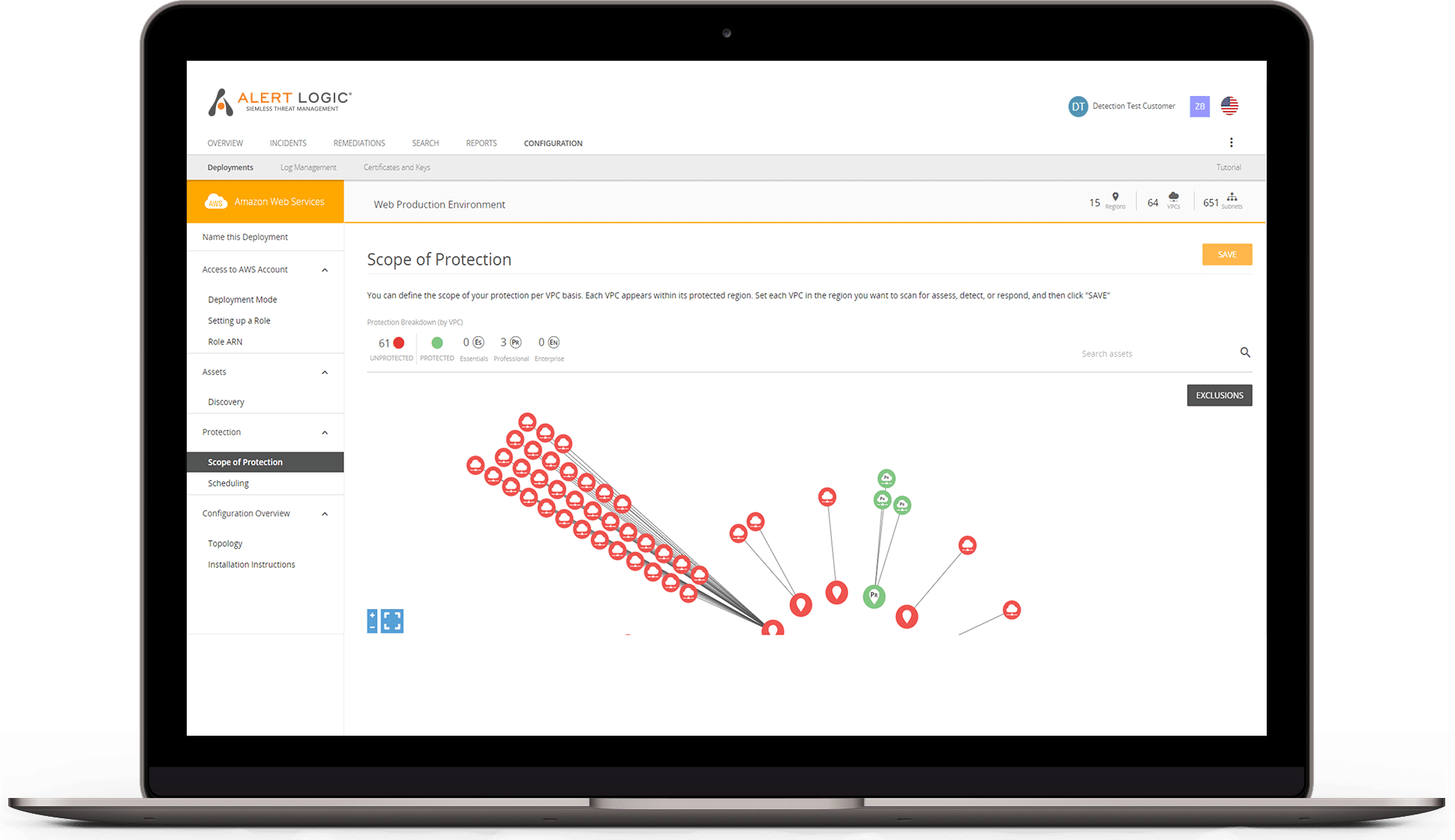
Visualize All Your Assets
Alert Logic helps you stay ahead of threats with a seamless, proactive vulnerability assessment process — managed for you:
- Discover and visualize your assets based on recurring discovery processes across cloud, hybrid, and on-prem installations
- Refresh anytime for a current view of your environment, and pivot to see vulnerabilities by AMI, IP, Instance ID/type, Availability Zone, tags or keyword
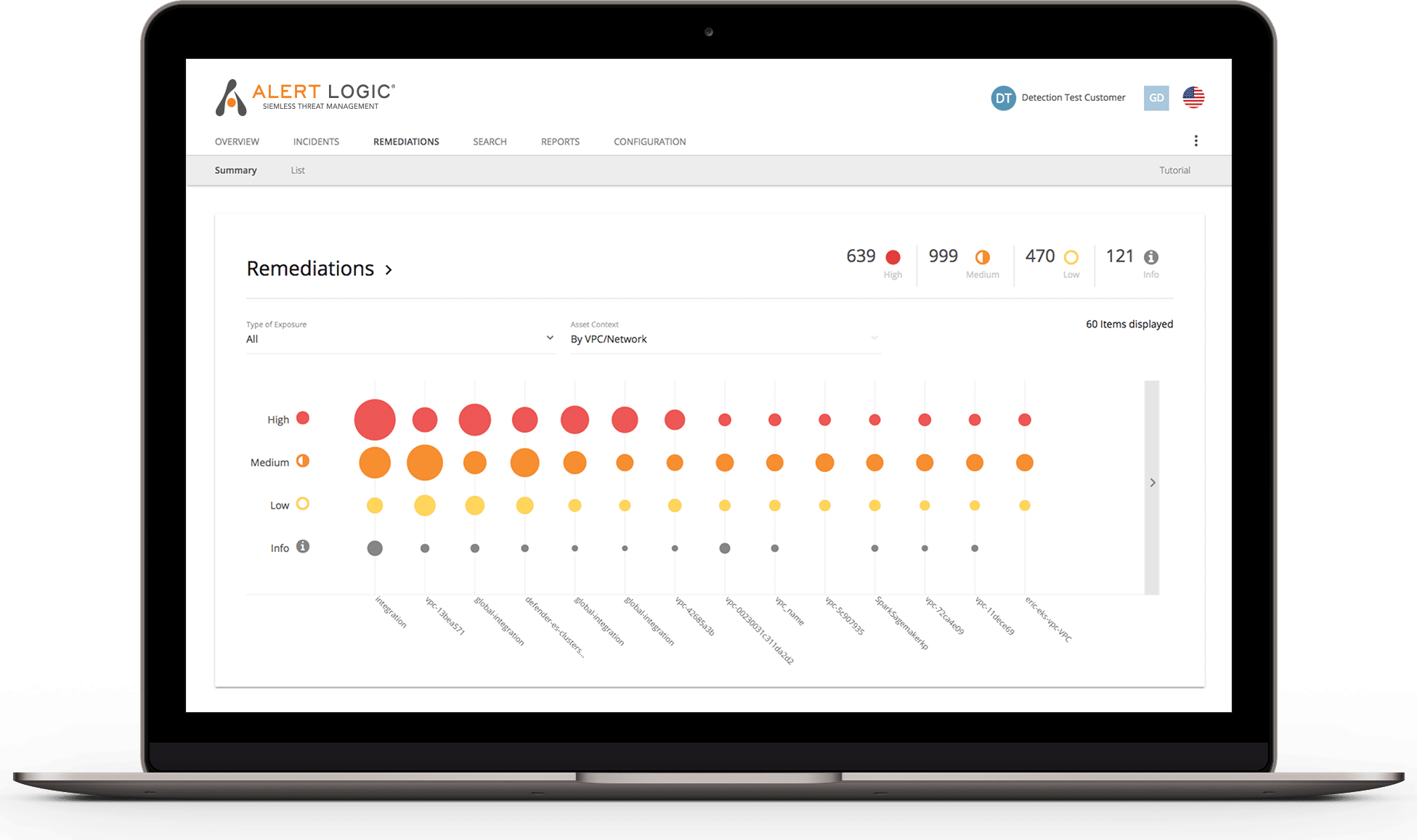
- Gain a clear view of the distribution of exposures and threats across your network assets through the topology page in our console
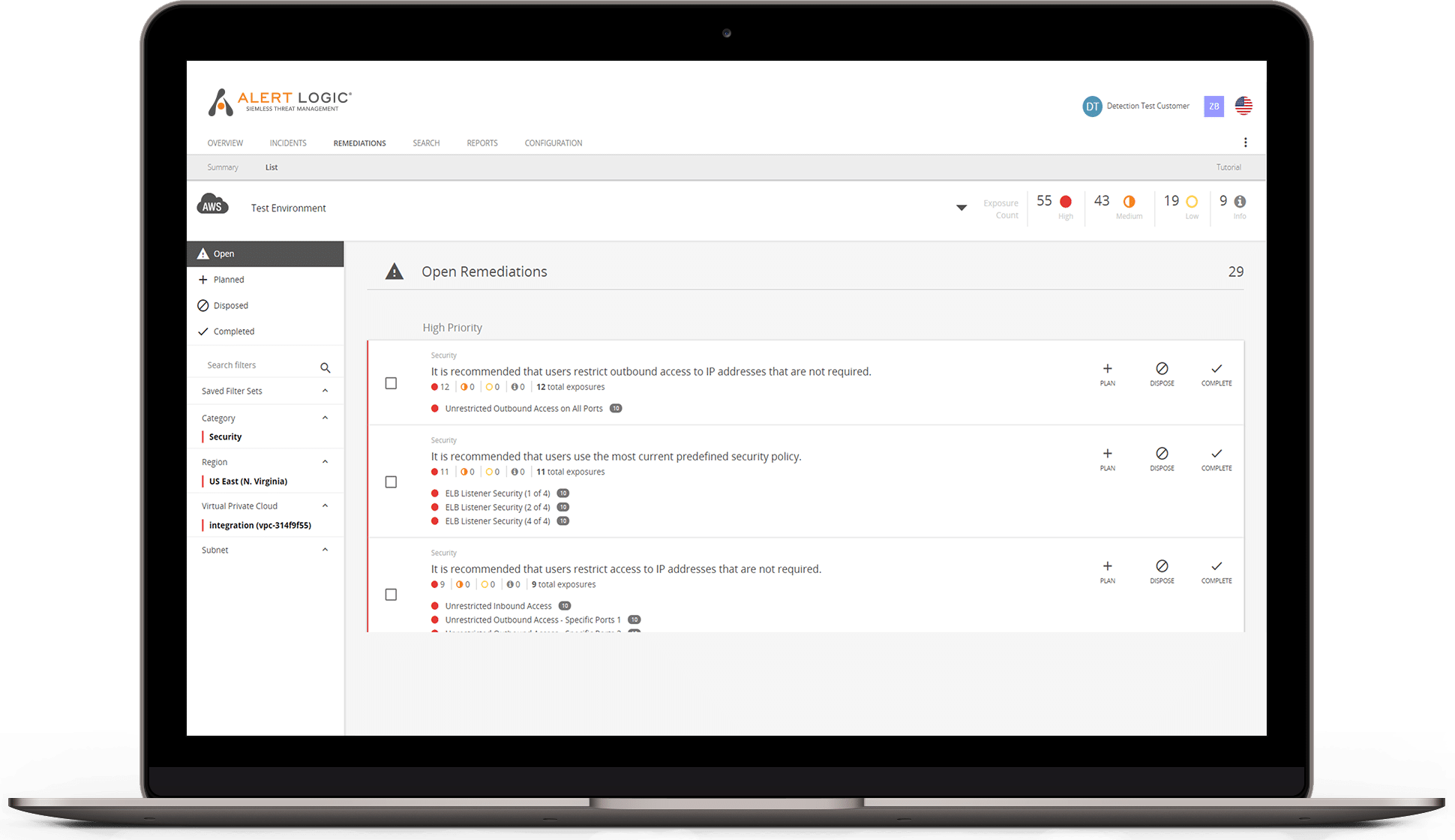
- Maintain your security with simple, clear remediation guidance from our cyber-risk experts
Meet PCI Vulnerability Scanning Requirements
Safeguarding sensitive payment data is critical, and customers expect their credit card information to be handled with the highest security standards. For organizations required to comply with PCI DSS 4.0, partnering with a managed security service that’s also a PCI Approved Scanning Vendor (ASV) ensures external vulnerability scans meet compliance requirements — including the new Requirement 11.3.2 mandating quarterly scans.
With our MDR and XDR solutions, customers gain on-demand access to PCI ASV scans that validate defenses, maintain compliance, and strengthen protection against today’s evolving threats.

Find & Fix Misconfigurations Faster
Misconfiguration of cloud platforms is a continuing challenge. According to the Top Threats to Cloud Computing 2024 report, misconfiguration and inadequate change control was ranked as the #1 cloud security concern.
Alert Logic tackles these challenges head-on with 24/7 managed vulnerability monitoring and in-depth assessments designed to safeguard your cloud environments:
- Agentless, API-driven technology launches in minutes – no security experience required
- No overhead added to your cloud environment
- REST API integration with your DevOps toolchain for continuous integration/continuous deployment (CI/CD)
- AWS workloads: No-touch automation through AWS APIs and services including CloudTrail and GuardDuty
AWS Vulnerability Scanning: Level 1 MSSP
Alert Logic has achieved the AWS Level 1 MSSP distinction across 10 specializations, including AWS Infrastructure Vulnerability Scanning and AWS Security Best Practices Monitoring. This recognition highlights our technical expertise and proven track record in helping organizations assess AWS configuration exposures, uncover software vulnerabilities, and take prioritized, actionable steps for remediation and risk mitigation.