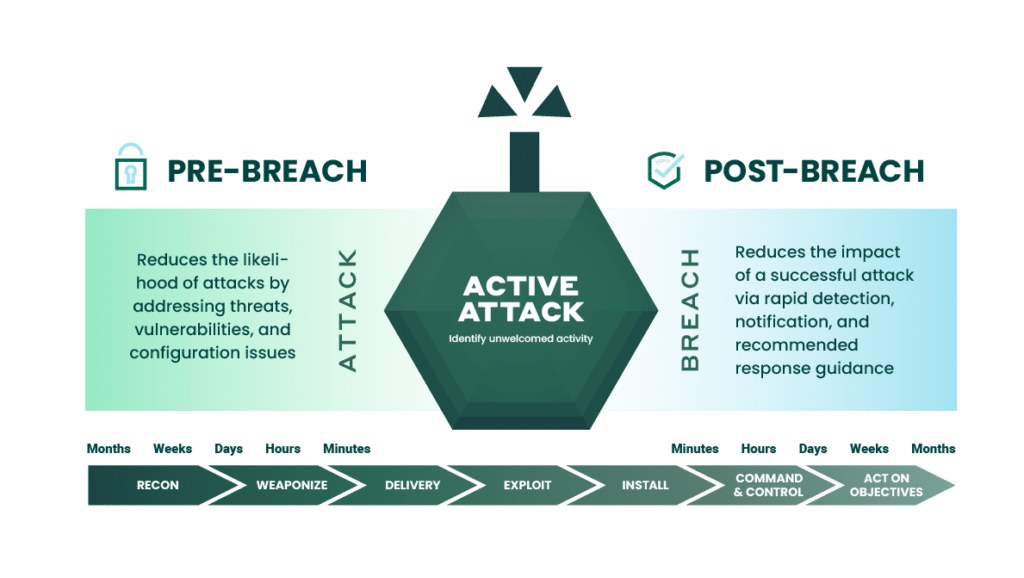
Cloud security is top of mind for today’s IT leaders — and for good reason. But let’s be honest: no one is invincible. Total immunity from breaches is a myth. With increasingly sophisticated threat actors lurking in every corner, the digital battlefield is more treacherous than ever.
The good news? A smart, well-rounded cloud security strategy can drastically reduce your risk. It’s not about perfection. It’s about preparation, resilience, and staying a step ahead.
To be truly effective, your strategy must address both prevention and response. Here are five essential components to help you build a stronger, more secure cloud posture:
1. Visibility
Lack of visibility around cloud infrastructure is one of the top concerns for many organizations. The cloud offers seamless deployment of new workloads whenever necessary. Take, for instance, the creation of a workload to tackle a short-term project or meet a sudden surge in demand. However, once the project concludes, these assets often fade into obscurity. Cloud environments remain fluid, ever-changing entities. Without proper insight into these shifts, your organization risks exposure to potential security breaches. After all, you can’t protect what you can’t see.
2. Exposure Management
Protecting your organization is about limiting your exposure and reducing risk. Prioritizing and addressing vulnerabilities that can cause disruption to your business is a team effort. You need alignment on the top concerns between your IT and security groups and a strong, collaborative relationship between them to effectively manage your exposure.
[Related Reading: Successful Cloud Modernization]
3. Prevention Controls
Organizations managing extensive on-premises or hybrid setups face a formidable challenge with tool compatibility during their transition to the cloud. Many existing tools struggle to integrate seamlessly with cloud environments, which can hinder operational efficiency. Additionally, expanding into the cloud opens up new attack pathways, demanding enhanced security measures. Therefore, it is crucial to implement strong security controls from the very beginning and continuously adapt them to effectively combat evolving threats in the cloud landscape.
4. Detection
When a breach occurs, do you have the capability to detect it swiftly? This poses a significant challenge for numerous organizations due to the scarcity of cybersecurity expertise available in the market. In 2023 alone, the global cybersecurity sector faced a shortfall of over 3.99 million positions. It’s crucial for your security infrastructure to promptly identify anomalies, enabling you to mitigate potential damages effectively. Threat actors employ automated tools for their attacks, necessitating vigilant monitoring of your environment either internally or by outsourcing to a trusted third party.
[Related Reading: Bridging the Cybersecurity Talent Shortage]
5. Response
A critical element of a comprehensive cloud security strategy is a formally documented incident response plan that operates under the assumption of breach inevitability. This plan must explicitly define roles, responsibilities, and communication workflows across relevant teams and stakeholders to ensure rapid containment, mitigation, and recovery.
Regular validation through tabletop exercises and live simulations, coupled with periodic reviews and updates — at minimum annually — are essential to maintain operational readiness and alignment with evolving threat landscapes and organizational changes.
Cloud security is a shared responsibility between you and your cloud provider. Crafting an effective cloud security strategy for your organization hinges on grasping the division between the provider’s responsibilities and your own.
Fortra’s Alert Logic is a managed security provider with extended detection and response (XDR) and managed detection and response (MDR) solutions. Our security experts, data scientists, vulnerability researchers, and 24/7 monitoring capability can help you proactively identify vulnerabilities and root out threat actors so you can deliver the best protection possible for your organization’s applications and data.