Having trouble keeping up and making sense of all the Meltdown and Spectre patches being released? You’re not alone. This guide will help.
Ever since news of Meltdown and Spectre — two massive CPU vulnerabilities affecting nearly every operating system and device — hit, vendors have been racing to release updates to mitigate the flaws. Things haven’t exactly gone smoothly, with several incompatibility muck ups causing a lot of finger-pointing and frustration. To help clear things up, we’ve put together a quick guide that walks through the major updates to operating systems and browsers, explaining how they address Meltdown and/or Spectre, what they specifically don’t address, and any known compatibility or performance issues that have been reported.
Meltdown & Spectre Overview
Before we dive in, here’s a quick recap of what Meltdown and Spectre are all about. For more in-depth details see our post, The Meltdown and Spectre CPU Bugs, Explained.
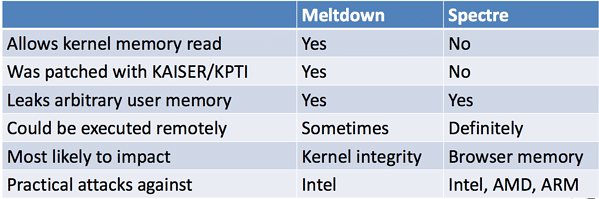
Meltdown (rogue data cache load — CVE-2017-5754)
Meltdown is a CPU vulnerability that allows a user mode program to access privileged kernel-mode memory. It affects all out-of-order Intel processors released since 1995 with the exception of Itanium and pre-2013 Atoms. No AMD processors are affected by Meltdown.
Of the two bugs, Meltdown is the easier one to fix and can largely be addressed with operating system updates.
Spectre variant 1 (CVE-2017-5753) & Spectre variant 2 (CVE-2017-5715)
Spectre isn’t so much a specific vulnerability as it’s a new class of attack. It’s enabled by the unintended side effects of speculative execution (something processors do to speed things up by predicting what instructions they’re about to receive and executing them ahead of time).
There are two flavors of Spectre — variant 1 (bounds check bypass, CVE-2017-5753) and variant 2 (branch target injection, CVE-2017-5715). Both can potentially allow attackers to extract information from other running processes (ex: stealing login cookies from browsers).
Intel, ARM, and AMD processors are all reportedly affected by Spectre to some extent, and it poses significant patching problems. While operating system and browser updates have helped mitigate the risk of Spectre to some degree, experts agree the only true fix is a hardware update. As such, Spectre is likely to remain an issue for years to come.
Source: SANS / Rendition Infosec
It’s important to note that both vulnerabilities put information disclosure at risk. However, neither are remote execution vulnerabilities — in other words, they don’t allow attackers to run malware.
OS Updates
Windows updates
Microsoft’s process for releasing Windows updates addressing Meltdown and Spectre has been a bumpy road, marred by high-profile incompatibility issues with third-party antivirus (AV) software and AMD processors. In some cases, delivery of the latest security updates was temporarily restricted or suspended.
More details and direct download links to the updates below:
- Windows 10
- Version 1507 — KB4056893 (issued 1/3/18)
- Version 1511 — KB4056888 (issued 1/3/18)
- Version 1607 — KB4056890 (issued 1/3/18)
- Version 1703 — KB4056891 (issued 1/3/18)
- Version 1709 — KB4056892 (issued 1/3/18)
- Update that disables Intel’s Spectre variant 2 mitigation (which has caused issues) — KB4078130 (issued 1/27/18)
- Version 1709 — KB4090007 (issued 3/1/18) this update includes microcode fixes that mitigate Spectre variant 2 for devices with Intel Skylake, Kaby Lake, and Coffee Lake processors
- Windows 8 and Windows Server 2012
- Windows 8.1 and Server 2012 R2— KB4056898 (issued 1/3/18)
- Update that disables Intel’s Spectre variant 2 mitigation (which has caused issues) — KB4078130 (issued 1/27/18)
- Windows 8 and Server 2012 — KB4088877 (issued 3/13/18)
- Windows 8.1 and Server 2012 R2 — KB4088879 (issued 3/13/18)
- No patches available for Windows Server 2012 non-R2 version
- Windows 7 and Windows Server 2008
- Windows 7 SP1 and Server 2008 R2 SP1 — KB4056897 (Security only, issued 1/3/18)
- Windows 7 SP1 and Server 2008 R2 SP1 — KB4056894 (Monthly rollup, issued 1/4/18)
- Update that disables Intel’s Spectre variant 2 mitigation (which has caused issues) — KB4078130 (issued 1/27/18)
- ALERT: If you’ve installed any January, February, or March updates for Windows 7 / Windows Server 2008 R2 64-bit machines, apply the latest April patch (either the monthly rollup KB4093118 or security-only update KB4088881) now. The April updates address a critical vulnerability dubbed “Total Meltdown” (CVE-2018-1038) introduced by previous updates.
- No patches available for Windows Server 2008 non-R2 version
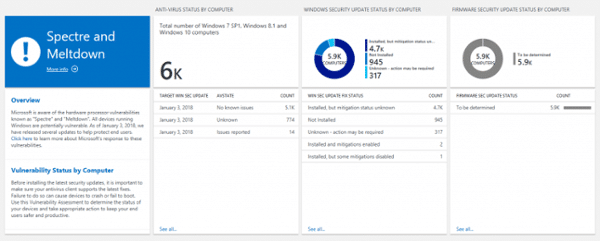
UPDATE (2/13/18): Microsoft has added capabilities to its free Windows Analytics service to help IT pros better track and manage their Meltdown and Spectre patching process. The new features include a dashboard that highlights the status of antivirus compatibility, Windows security updates, and firmware updates — all in one place for every Windows device you manage.
What the Windows updates address:
- Spectre variant 1, bounds check bypass (CVE-2017-5753)
- Meltdown, rogue data cache load (CVE-2017-5754) UPDATE (1/17/18): As readers have pointed out, it appears Windows patches for 32-bit systems (x86-based systems) do not provide Meltdown mitigations.
Per Microsoft:
The existing 32-bit update packages listed in this advisory fully address CVE-2017-5753 and CVE-2017-5715, but do not provide protections for CVE-2017-5754 at this time. Microsoft is continuing to work with affected chip manufacturers and investigate the best way to provide mitigations for x86 customers, which may be provided in a future update.
What they don’t address:
- Spectre variant 2, branch target injection (CVE-2017-5715) — firmware/microcode updates are required to fully address Spectre variant 2. UPDATE 1/29/18: Microsoft has issued an emergency out of band update (KB4078130) that disables the mitigation for Spectre variant 2 (branch target injection) that was included in Intel’s buggy microcode updates. Microsoft justified the move by pointing to reports that Intel’s new microcode can cause higher than expected reboots which may result in data loss or corruption (confirmed in Intel’s Q4 2017 financial results statement). Microsoft’s update is available for Windows 7 (SP1), Windows 8.1, and all versions of Windows 10. Alternatively, the company has also provided instructions for helping customers manually disable and enable Spectre variant 2 mitigation via registry setting changes. You can find the instructions for server customers, and for all other customers. UPDATE 3/2/18: Microsoft is now including microcode fixes for Intel Skylake processors in the latest Windows update (KB4090007). While that update only applies to Windows 10 version 1709 and Windows Server version 1709, the company has also announced it is working with Intel on future updates for additional Windows versions and Intel processors. UPDATE 3/14/18: Microsoft has included microcode fixes for Intel Kaby Lake and Coffee Lake processors in the March Windows update (KB4090007). Once again, these fixes are only currently available for Windows 10 version 1709 and Windows Server version 1709. UPDATE 4/27/18: Microsoft has released two new updates mitigating Spectre variant 2 for Windows 10 and Windows Server 2016 systems. The first, KB4078407, is available as a manual update only and is positioned as a “do-over” of sorts to Microsoft’s original mitigations included in its January 4 updates. The second update, KB4091666, is also available as a manual download and is for Intel systems only. It includes microcode fixes for additional Intel models not included in the previous March updates.
Known issues
UPDATE 3/14/18: Microsoft has removed the registry key requirement outlined below for Windows 10 users. All other Windows versions utilizing third-party antivirus software are still required to have a special registry key set in order to receive updates. More info below.
- AV compatibility issues: During tests, Microsoft discovered that a compatibility issue with “a small number of antivirus detection software products” was causing system crashes. As a result, the company has made delivery of the Windows security updates linked to above contingent on the presence of a special registry key, which it has instructed all AV vendors to add to customer devices only after they’ve confirmed their products are compatible. This deserves reiterating:
Key="HKEY_LOCAL_MACHINE"
Subkey="SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat"
Value="cadca5fe-87d3-4b96-b7fb-a231484277cc" Type="REG_DWORD”
Data="0x00000000”
This has created a lot of confusion, especially since the response from AV vendors has varied, with some setting the registry key for their customers and others recommending users set it, themselves, manually. The situation only gets more complicated considering many organizations have more than one AV solution installed.
Update: Microsoft has clarified that Windows Defender Antivirus, System Center Endpoint Protection, and Microsoft Security Essentials are compatible with the update and do set the required registry key.
That means as long as you have one of these built-in Microsoft protections enabled the registry key should be set automatically—no further, manual action should be necessary.
Caveat: If you are using third party software that Microsoft officially recognizes as AV, it is important to note that, by default, Windows Defender and Microsoft Security Essentials will turn themselves off. That means the registry key won’t be added unless you or your AV actively do it.
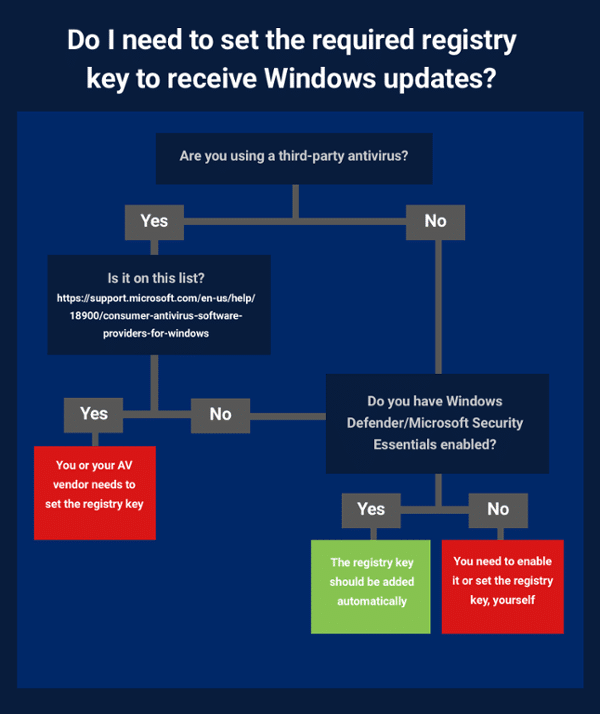
All that said, here is a flow chart that can help you determine your situation:
spectre2
Windows users who aren’t using a third-party antivirus and don’t have Windows Defender or Microsoft Security Essentials enabled will need to set the registry key themselves, manually. To help, Bleeping Computer has put together a .reg file that automates that task. Note: They also issue a warning to make absolutely sure you’re not running an AV that isn’t compatible with the update before using it.
If you are using an AV and haven’t received the Windows patch yet, you are advised to wait until your AV vendor either issues an update that sets the registry key for you or specifically recommends that you do so, yourself.
- AMD compatibility issues: As first reported at the Verge, Microsoft has received numerous reports of PCs running AMD processors not booting after installing the latest Windows security update. After investigating, the company confirmed there were issues and temporarily stopped delivering the update to AMD devices. Affected users needed to visit Microsoft’s support site for instructions on getting their machines back up and running. Update (1/18/18): Microsoft has announced it will resume rolling out patches for AMD devices running Windows 7 SP1 and Windows Server 2008 R2 SP1, Windows 8.1 and Windows Server 2012 R2, and Windows 10, version 1709. Updates for four versions of Windows 10 — 1511, 1607, and 1703 — are still paused. As are updates for Windows Server 2016 and Windows 10 Enterprise.
- Group or MDM policy configurations may be disabling updates: According to Microsoft, if you have Group or MDM policy settings configured to disable preview builds, your machines may not be receiving updates. To fix that, Microsoft recommends temporarily changing Group/MDM policy settings to “Not Configured” and changing them back once the updates have been installed.
- Performance impact: As with the other operating systems, patches addressing Meltdown and Spectre are expected to take a non-insignificant toll. In a blog post, Microsoft Executive VP Terry Myerson explains the impact of these fixes can vary depending on the version of Windows running and the age of the machine:
- Windows 10 on 2016-era PCs with Skylake, Kaby Lake, or newer CPU: Single-digit slowdowns, which most users won’t notice.
- Windows 10 on 2015-era PCs with Haswell or older CPU: Slowdown can be more significant. Some users may notice a decrease in performance.
- Windows 8 or Windows 7 on 2015-era PCs with Haswell or older CPU: Most users will likely notice a decrease in system performance.
- Windows Server (any CPU): Mitigations to isolate code within a Windows Server instance results in a more significant performance impact. According to Myerson, “This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance and balance the security versus performance tradeoff for your environment.”
Enabling Protections for Windows Server
Microsoft has also advised Windows Server customers that they need to take the additional step of adding the following registry keys in order to enable patch protections.
To enable the fix:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f
If this is a Hyper-V host and the firmware updates have been applied: fully shutdown all Virtual Machines (to enable the firmware related mitigation for VMs you have to have the firmware update applied on the host before the VM starts).
Restart the server for changes to take effect.
To disable this fix:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the server for the changes to take effect.
(There is no need to change MinVmVersionForCpuBasedMitigations.)
Microsoft also notes that for Hyper-V hosts, live migration between patched and unpatched hosts may fail. The company also points to an alternative protection mechanism you can use on hosts that don’t have updated firmware yet.
Additional guidance from Microsoft
Verifying new Windows protections are enabled
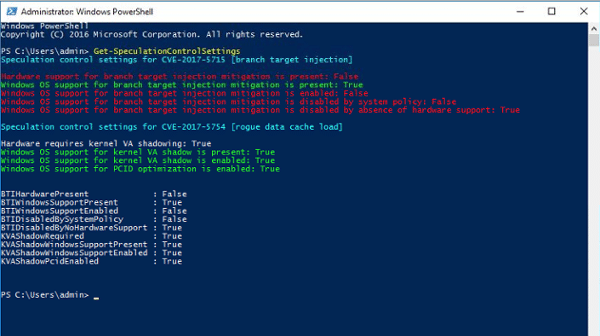
To help confirm whether updates have been implemented correctly, Microsoft has provided a PowerShell script that system administrators can run to test Meltdown and Spectre mitigations.
The following command will install the PowerShell module:
PS > Install-Module SpeculationControl
Note: There are a couple of requirements for running this command. First, you’ll need to be running PowerShell with admin privileges and may need to adjust execution policy. Also, the Install-Module command was introduced to PowerShell in version 5.0. Most Windows 7 machines will not have this version, due to the upgrades being optional and unrelated to security. Any machine with an outdated version of PowerShell can still run the Get-SpeculationControlSettings function below, however, as long as you can obtain the contents of the script and run it ad-hoc.
Once installed, the following command will run the test to check your system:
PS > Get-SpeculationControlSettings
The output will look something like this:
Results for Spectre protections
The first grouping — “Speculation control settings for CVE-2017-5715 [branch target injection] — refer to protections in place for the Spectre vulnerability. If the value for “Windows OS support for branch target injection mitigation is present” is “True” then the Windows Security update has been successfully installed.
The other red lines in that section simply confirm that more complete mitigation for Spectre requires firmware updates, which Intel says it’s in the process of rolling out. According to the company, updates for more than 90 percent of its processor products should be introduced by the end of next week.
Results for Meltdown protections
The second grouping — “Speculation control settings for CVE-2017-5754 [rogue data cache load] — refer to protections in place for the Meltdown vulnerability. If you see the following results and no red lines, then you’ve confirmed the Windows Security update has been successfully implemented and the machine is protected:
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID optimization is enabled: True
Test results confirming successful mitigation of the Meltdown vulnerability
If you see any red lines in this section, then that means the update has not been successfully applied.
macOS and iOS updates
Apple included mitigations to address Meltdown in its macOS 10.13.2 and iOS 11.2 updates released in December. It has since followed up with additional mitigations addressing Spectre with the macOS High Sierra 10.13.2 Supplemental Update and iOS 11.2.2 update.
What they address
- Meltdown (rogue data cache load — CVE-2017-5754)
- Spectre variant 1 (bounds check bypass — CVE-2017-5753) to some degree
- Spectre variant 2, (branch target injection — CVE-2017-5715) to some degree
What they don’t address:
- Spectre variants 1 and 2 — to some degree
While Apple says its latest updates to macOS, iOS, and Safari help mitigate the risk of Spectre being exploited, the company acknowledges it will be continuing to develop and test further mitigations.
No reported compatibility or performance issues
Linux updates
After being left out of the loop, Linux developers are making significant progress on patches, even if they’re not particularly happy about being put in this position. The latest update of the stable Linux kernel (4.14.13) includes patches designed to mitigate Meltdown with Kernel Page Table Isolation (KPTI). More comprehensive patches (including fixes for ARM64 processors) will be available in 4.15, scheduled for release in two weeks.
Patches have also been added to the 4.4 and 4.9 stable kernel trees.
Canonical has released a second update for Ubuntu 16.04 LTS Xenial users after the first caused boot issues.
What they address:
- Meltdown (rogue data cache load — CVE-2017-5754), though not currently for 32bit (x86) machines
- Spectre variant 1 (bounds check bypass — CVE-2017-5753) to some degree
- Spectre variant 2, (branch target injection — CVE-2017-5715) to some degree
What they don’t address:
- Meltdown for 32bit (x86) machines
- Spectre variants 1 and 2 — to some degree
Patches have now been released that mitigate both variants of Spectre, but variant 2 mitigation also requires firmware/microcode updates to be in place. Because those updates are still being (re)developed and rolled out — keep in mind the latest recommendation from Intel was not to apply its firmware patches — variant 2 mitigation is currently incomplete.Work is underway to implement Retpoline, a workaround mitigation technique introduced by Google specifically for dealing with Spectre variant 2. The big advantage of Retpoline appears to be that it results in less of a performance impact than the microcode fixes, but, that said, it does have limitations.For one thing, Retpoline does not work on Intel Skylake processors. More importantly, it requires that code be recompiled in order to “immunize” it. While recompiling the kernel with Retpoline is one thing, updating every userspace application is anything but a quick fix. As this FAQ on the Ubuntu Wiki puts it, “until every piece of code on a system is rebuilt with retpoline the kernel must use microcode-based mitigations to protect userspace.” In other words, Retpoline isn’t a complete substitution for applying microcode updates — yet.
Known issues:
- Patches haven’t been released for machines running ARM64 processors: They are expected to be supported with the release of 4.15 in a couple of weeks.
- Patches bricking Ubuntu 16.04 computers: According to Bleeping Computer, boot issues have been reported by a large number of Ubuntu users running the Xenial 16.04 series after updating to kernel image 4.4.0-108. New updates with kernel image 4.4.0-109 have since been released which address the issue.
- No Meltdown fix is currently available for 32bit (x86): Moving to a 64-bit kernel is the only currently recommended mitigation.
- Spectre version 2 mitigations still reliant on firmware updates: As Intel and AMD continue to work through update difficulties mitigation remains incomplete.
- Performance impact: Based on initial testing, performance penalties for the patches are expected to range from single to double digits, depending primarily on how much interaction applications/workloads have with the kernel. You can find more details in benchmark studies conducted by Phoronix and Red Hat.
Checking Linux for Spectre and Meltdown vulnerability:
A simple script has been developed to help determine whether Linux kernel installations are still vulnerable to Meltdown and Spectre after applying patches.
Browser updates
According to researchers, the most likely exploitation of Spectre appears to be web-based attacks using JavaScript (say in a malicious ad) to leak information, session keys, etc., cached in the browser. As such, Google, Mozilla, Apple, and Microsoft have all either issued or schedule new updates for their browsers to reduce that risk.
What browser updates address:
- Spectre (CVE-2017-5753 and CVE-2017-5715) to some extent
What browser updates don’t address:
- Meltdown (CVE-2017-5754): You’ll need to apply OS updates to mitigate Meltdown.
Chrome
Google has announced it will be including mitigations for Spectre starting with Chrome 64, which will be released on or around January 23. In the meantime, Chrome users are advised to turn on site isolation, which can help prevent a site from stealing data from another site.
UPDATE (1/25/18): Google released Chrome 64 for Windows, Mac, and Linux. The update does include a patch to address Spectre, although Google did not provide technical details, stating simply “this release contains additional mitigations against speculative side-channel attack techniques.” In addition to those mitigations, the update also addresses other flaws (there are a total of 53 security fixes in all).
Firefox
Mozilla has already issued Firefox version 57.0.4, which helps address Spectre by disabling or reducing Firefox’s internal timer functions and disabling the SharedArrayBuffer feature. Firefox users can take additional precaution by enabling site isolation as well.
Safari
Apple hreleased Safari 11.0.2 to specifically mitigate the effects of Spectre.
IE and Edge
Microsoft has made changes to both Internet Explorer 11 and Microsoft Edge to mitigate Spectre. In addition to removing support for SharedArrayBuffer from Edge, it has made changes to reduce the precision of several time sources to make successful attacks more difficult.
Firmware updates
OS and browser updates only partially mitigate Meltdown and Spectre. Organizations need to be prepared for UEFI firmware and BIOS updates, as well. When and whether updates will be pushed out will vary from vendor to vendor, adding another layer of complexity and uncertainty to patching. In some cases, admins may have to proactively check for updates from their PC makers periodically over the next few days or weeks.
Intel
Note: The saga surrounding Intel updates for Meltdown and Spectre is long and ongoing. For the latest news, skip down to “Known issues” and scroll to the bottom of the list.
1/12/18: Intel has released new Linux Processor microcode data files that can be used to add Meltdown and Spectre mitigations without having to perform a BIOS update.
Intel went on record promising firmware updates for 90 percent of affected processors made in the past five years by January 15. So far, it looks as though these microcode fixes apply to a specific list of processors provided here.
The microcode updates can be downloaded directly from Intel, and Bleeping Computer has provided instructions and a video example to help walk admins through the install process here. It should be noted that some issues have already been reported with the updates, specifically around unwanted reboots. While Intel initially confirmed machines with Broadwell and Haswell CPUs were experiencing that issue, later the company said machines running newer processors were affected, too (more details below).
Windows users need to wait until Microsoft finishes testing the microcode and releases an additional update.
Known issues:
- Performance impact: Statements regarding the potential performance impact of those updates have been inconsistent, but the company has most recently said the patches are slowing processors down by six percent in certain situations.
- Older Broadwell and Haswell CPUs experiencing sudden reboots: Intel is already confirming the company has received reports of glitches resulting from the firmware update on systems running Intel Broadwell and Haswell CPUs.
- UPDATE (1/18/18): Machines with newer CPUs also experiencing sudden reboots: Intel has since confirmed the firmware update is causing machines with Ivy Bridge, Sandy Bridge, Skylake, and Kaby Lake processors to suffer unwanted reboots, too.
- UPDATE (1/22/18): Intel now recommending customers NOT apply firmware update: The company has reportedly discovered the root cause of the Broadwell and Haswell boot issues, and is testing an updated patch. In the meantime, it is recommending customers stop deployment of the current patch to avoid reboots and other “unpredictable system behavior.”
- UPDATE (1/24/18): HP and Dell have removed latest BIOS updates until Intel issues new stable firmware: Following Intel’s advice, both companies have halted deployment of Intel’s buggy microcode.
- UPDATE 1/29/18: Microsoft has issued an emergency out of band update (KB4078130) that disables Intel’s mitigation for Spectre variant 2: Microsoft justified the move by pointing to reports that Intel’s new microcode can cause higher than expected reboots which may result in data loss or corruption (confirmed in Intel’s Q4 2017 financial results statement).
- UPDATE 2/7/18: Intel has issued a new microcode update for Skylake processors that addresses Spectre variant 2. Skylake system owners should expect firmware updates soon. Fixes for other chips remain in beta testing.
- UPDATE 2/21/18: Additional microcode updates addressing Spectre variant 2 available: Intel reports its microcode update for Skylake processors is stable, and additional updates for Kaby Lake and Coffee Lake are being rolled out, as well. Considering the problems experienced with the initial firmware updates, many experts are advising caution and careful testing before installing the new updates, however. According to Intel, fixes for Sandy Bridge, Ivy Bridge, Broadwell, and Haswell processors are still in beta.
- UPDATE 3/2/18: Intel has released microcode updates for Broadwell and Haswell processors. That just leaves fixes for Sandy Bridge and Ivy Bridge processors, which according to Intel, are still in beta testing. As is the case with all of these updates, there is still the matter of them being distributed via hardware suppliers, which may take some time. In other news, Microsoft is now including microcode fixes for Intel Skylake, Kaby Lake, and Coffee Lake processors in the March Windows update (KB4090007). While that update only applies to Windows 10 version 1709 and Windows Server version 1709, the company has also announced it is working with Intel on future updates for additional Windows versions and Intel processors.
- UPDATE 4/5/18: Intel reveals list of processors that won’t receive Meltdown and Spectre patches. The company has confirmed the following families of older processors won’t receive microcode updates designed to mitigate the vulnerabilities: Bloomfield, Bloomfield Xeon, Clarksfield, Gulftown, Harpertown Xeon C0 and E0, Jasper Forest, Penryn/QC, SoFIA 3GR, Wolfdale, Wolfdale Xeon, Yorkfield, and Yorkfield Xeon.
- UPDATE 4/27/18: Microsoft is including microcode fixes for additional Intel models in Windows update KB4091666. The additional models covered include Broadwell and Haswell processors.
AMD
Update 1/12/18: AMD has officially acknowledged that its processors are vulnerable to both variants of Spectre, but not Meltdown. While the company says OS patches are enough to mitigate Spectre variant 1, it will be rolling out optional microcode updates this week, starting with fixes for Ryzen and EPYC processors.
Update 4/11/18: AMD has released microcode updates mitigating Spectre variant 2 for processors dating back to 2011 and has shared them with OEM and motherboard makers so they can be included in BIOS updates. In addition, Microsoft has released an update that includes (KB4093112) OS-level patches for AMD users.
Known issues:
- Windows OS update compatibility issues: As first reported at the Verge, Microsoft has received numerous reports of PCs running AMD processors not booting after installing the latest Windows security update. After investigating, the company confirmed there are issues — specifically with AMD Opteron, Athlon, and AMD Turion X2 Ultra families — and temporarily stopped delivering the update to AMD devices. AMD says it is working with Microsoft to resolve the issue. In the meantime, affected users need to visit Microsoft’s support site for instructions on getting their machines back up and running. Update (1/18/18): Microsoft has announced it will resume rolling out patches for AMD devices running Windows 7 SP1 and Windows Server 2008 R2 SP1, Windows 8.1 and Windows Server 2012 R2, and Windows 10, version 1709. Updates for four versions of Windows 10 — 1511, 1607, and 1703 — are still paused. As are updates for Windows Server 2016 and Windows 10 Enterprise.
IBM
According to IBM, firmware patches for POWER7+, POWER8, and POWER9 platforms are all currently available via FixCentral. The company says Power7 patches will be available February 7. In addition, it estimates IBM i operating system patches (also available via FixCentral) will finish rolling out on February 12, and AIX patches will be available starting January 26.
Closing note
For now, the generally recommended course of action is not to panic and instead take the time to properly assess, test, and carefully implement OS and firmware updates as they are made available—especially since there have been a variety of widespread compatibility issues already.