Ransomware is a persistent threat. Organizations of all sizes are targets, from small family-owned operations to large global enterprises, regardless of their level of security sophistication.
Attacks are increasing and costly. In 2020, daily attacks increased as the year progressed, with third quarter attacks increasing 50% over the first quarter numbers. And the average ransom demand is now over $80,000.
Ransomware creators are organized, global, and opportunistic. They operate much like enterprises with service desks and attack kits and take advantage of every opportunity, like the pandemic, to exploit weaknesses and vulnerabilities. There is no apparent end to their creativity — the latest attack types, in fact, hide within legitimate processes, making them very difficult to detect.
Detecting Ransomware Attacks
Ransomware attacks follow a common kill chain pattern to breach security and infect systems. This pattern follows the line of attack -> compromise -> objective, throughout which attackers are scanning your environment for security software and determining what malware to install to exploit your vulnerabilities.
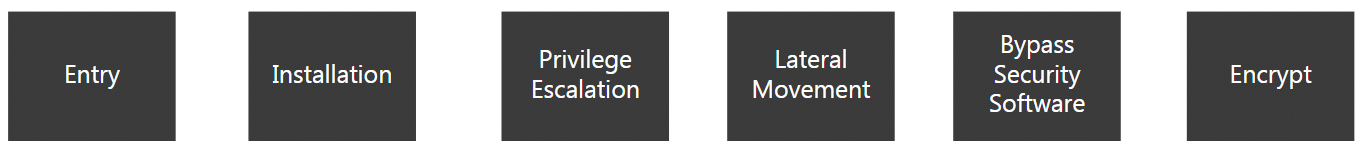
The Ransomware Kill Chain
Entry
Email is the most common vector exploited by attackers to gain entry into your infrastructure. Targeted phishing campaigns are easy to launch, and despite increased security awareness training, people still can be fooled into clicking on unknown links or opening attachments.
Two other vectors that are being exploited are virtual private network (VPN) connections and Windows Remote Desktop Protocol (RDP). With more people working from home, these vectors are even more prevalent today than they were in the past, and that makes them attractive to attackers.
Installation
Gaining entry is only the first step. Once malware enters, it is then installed. But the installation typically happens in phases. The first package installed usually is not the encryption package. Other malware code — sometimes called a “family of friends” — often will be installed first. Examples include Emotet, Trickbot, and Bazar. These packages are used to prepare your environment for delivery of the final encryption package.
Privilege Escalation
The next step is privilege escalation. This is a critical step in the ransomware lifecycle. In order to gain control over a lot of machines, the malware needs to elevate itself to administrator status and acquire domain administrative privileges.
Lateral Movement
Upon escalation of privileges, the malware then spreads across networks and open shares within your environment.
Bypass Security Software
As malware proliferates, it often installs other code to disable security software or alter settings or shutdown processes that might interfere with the installation of the encryption package.
Encrypt
This is the final step in the process. If ransomware is not detected and stopped by this point, the attack will succeed.
How Does Alert Logic Detect an Attack?
The key to stopping ransomware is to detect its presence early. Alert Logic ingests data from sources at different phases of the typical ransomware lifecycle and uses analytics engines to process data and formulate remediation measures.
Entry
To guard against ransomware entry, Alert Logic monitors both RDP and VPN vectors. It provides continuous coverage of the RDP Bruteforce attack vector using Windows logs and IDS (intrusion detection systems) as detection sources. The RDP Service Discovery vector is covered using data from firewall logs. This firewall analytic is used to track any new hosts that are open to the internet. Finally, VPN UBAD (user behavior analysis detection) is used to track any anomaly in terms of login and GEOIP resolution and then tracking if the IP address is different from the baseline for a VPN module.
Installation
Alert Logic offers protection against both the installation of malware friends and ransomware. For organizations with Extended Endpoint Protection (EEP), ransomware and variants of malware are blocked as they arrive in phishing emails. Or, if they are embedded in attachments, EEP blocks them from executing when opened.
Another way Alert Logic detects malware after installation is through blocking malicious IP addresses. Alert Logic uses firewall logs and IDS to monitor attempts at connecting to known malicious IP addresses. If malware gets installed and attempts to connect to one of these known addresses, Alert Logic terminates the connection.
DNS tunneling is another popular method used by malware after installation. Alert Logic continuously monitors for tunneling activity so attempts can be shut down before a breach can occur.
Privilege Escalation and Lateral Movement
At this phase in the ransomware lifecycle, malware attempts to elevate its privilege level, to seek out critical servers and infect them. To accomplish their goals, ransomware creators often utilize native Windows programs and processes — default system files and binaries that are used by the operating system — in an attempt to blend in and go undetected.
One set of commonly used binaries that are often exploited for nefarious purposes are known as Living off the Land Binaries (LOLBin). These are file-less, malware-less techniques attackers use to turn a system’s native tool into a useful hacking instrument capable of bypassing traditional file-based detection and prevention techniques. Common examples include:
- Rundll32 Process Dump – This is an important component of certain Windows operating systems that attackers can use to steal credentials.
- Certutil Download – This can be used to download an obfuscated malicious payload to a system.
- Certutil Decode – Certutil is a command-line tool installed as part of Active Directory Certification Services and can be used to de-obfuscate a malicious payload for purposes of executing the file.
- NLTest Show Trusts – This is part of Active Directory Domain Services and can be used to discover other domains and map out your environment.
- SYSVOL – This is part of Active Directory Domain Controller and can be used to distribute malicious code laterally and run it on other hosts in your network.
- Cobalt Strike Style Powershell Invocation – Cobalt Strike is heavily used by attackers, leveraging Powershell’s task automation and configuration management capability to perform privilege escalation, lateral movement, installation of suspicious services, and other tasks in your environment. This is a powerful, multi-use tool for attackers to use.
Living off the Land binaries are very effective tools for ransomware to use to infiltrate your systems. As a result, these are high-priority coverage targets for Alert Logic. In addition to the commonly-used binaries listed above, Alert Logic uses log telemetry of Windows behavior to continuously research other binaries and assess detection viability.
Stay Prepared Using Threat Intelligence
Ransomware continues to evolve. The key to protecting your organization is to stay on top of new threats as they emerge and to take preventive action as soon as possible.
Alert Logic’s Threat Intelligence team continuously analyzes threat data, tracking new attack vectors and propagation vectors for malware and ransomware, and incorporates detection capability into our Managed Detection and Response (MDR) solution. For more information, check out www.alertlogic.com/managed-detection-and-response/