Quickly Detect Network Intruders Before They Cause Damage
Protect your business with Alert Logic’s award-winning managed security services. Our advanced Intrusion Detection System (IDS) delivers continuous, comprehensive protection across your entire infrastructure — whether in the cloud, on-premises, or hybrid environments. With 24/7 threat monitoring, we quickly detect intrusions, reduce attacker dwell time, and help minimize the impact of cyberattacks. From containers to applications to core systems, we keep your environment secure.
Our IDS solution identifies high-risk threats like lateral movement, brute force attempts, privilege escalation, ransomware, and command-and-control activity. By analyzing network traffic across all hosts, we give you full-spectrum visibility into potential threats.
For containerized environments, our specialized security extends to AWS, Azure, and on-prem platforms, including Docker, ECS, Kubernetes, Elastic Beanstalk, and CoreOS providing seamless, intelligent defense against modern attacks.
What Is An Intrusion Detection System?
NIST defines an IDS as “a security service that monitors and analyzes network or system events to detect and provide real-time or near-real-time warnings of unauthorized attempts to access system resources.” An IDS primarily examines internal network traffic to identify suspicious or malicious activity, enabling it to detect attacks that bypass the firewall or originate from within the network.
A network IDS is critical for securing your network as it allows you to detect and respond to malicious traffic. It can immediately alert your team of potential attacks or network intrusions. A network IDS also continuously monitors all inbound, outbound, and internal traffic, analyzing data flows between systems within the network. When suspicious activity or recognized threats are detected, the IDS triggers immediate alerts, empowering the IT team to respond swiftly, investigate thoroughly, and take decisive action to block or mitigate an attack before it causes damage.
Firewall vs. Intrusion Detection System: What’s the Difference?
Firewall
A firewall acts as a gatekeeper filtering incoming and outgoing network traffic based on predefined security rules. Positioned at the network perimeter, it blocks or permits traffic primarily by analyzing packet headers (e.g., IP addresses, ports, protocols). While next-gen firewalls (NGFW) can inspect payloads for deeper inspection, this is still relatively uncommon in practice.
Firewalls operate inline, actively controlling traffic flow to prevent unauthorized access.
Intrusion Detection System (IDS)
An IDS is a passive security tool that monitors and analyzes mirrored network traffic for signs of suspicious activity or known threats. It evaluates both headers and payloads, using techniques like signature-based and anomaly-based detection to identify threats that may bypass firewalls.
Unlike firewalls, IDS tools sit out of band and do not block traffic. Instead, they trigger alerts and provide valuable context for investigations.
Stop Chasing False Alarms — Start Catching Real Threats
Unreliable IDS alerts waste your team’s time and let real breaches slip through the cracks — often undetected for up to 277 days. We change that. Our managed network intrusion detection system relentlessly monitors your network traffic to uncover hidden threats. Backed by expert threat analysts, we filter the noise and deliver only actionable insights — so you can respond with confidence, speed, and precision.
- Achieve rapid security monitoring in minutes with pre-built automated deployment
- Effortlessly scale with low-impact agents that self-configure, self-register, and self-deregister — ensuring seamless, no-touch support for auto-scaling environments
- Secure your network with deployed agents that encrypt and transmit all ingress, egress, and lateral traffic to our backend for advanced threat processing
- We compare your network traffic with over 17,000 active IDS signatures that detect a wide array of malicious activity and attack methods, including exploits in app stack components, and attack methods included in the OWASP Top 10
- 24/7 security monitoring, expert incident analysis, and live notifications of critical attacks by security analysts in our global SOC
Harness Your IDS Data for Proactive Network Security
- Always-on monitoring and scanning, advanced analytics combined with machine learning provide a holistic view of your environment so you can detect network intruders faster
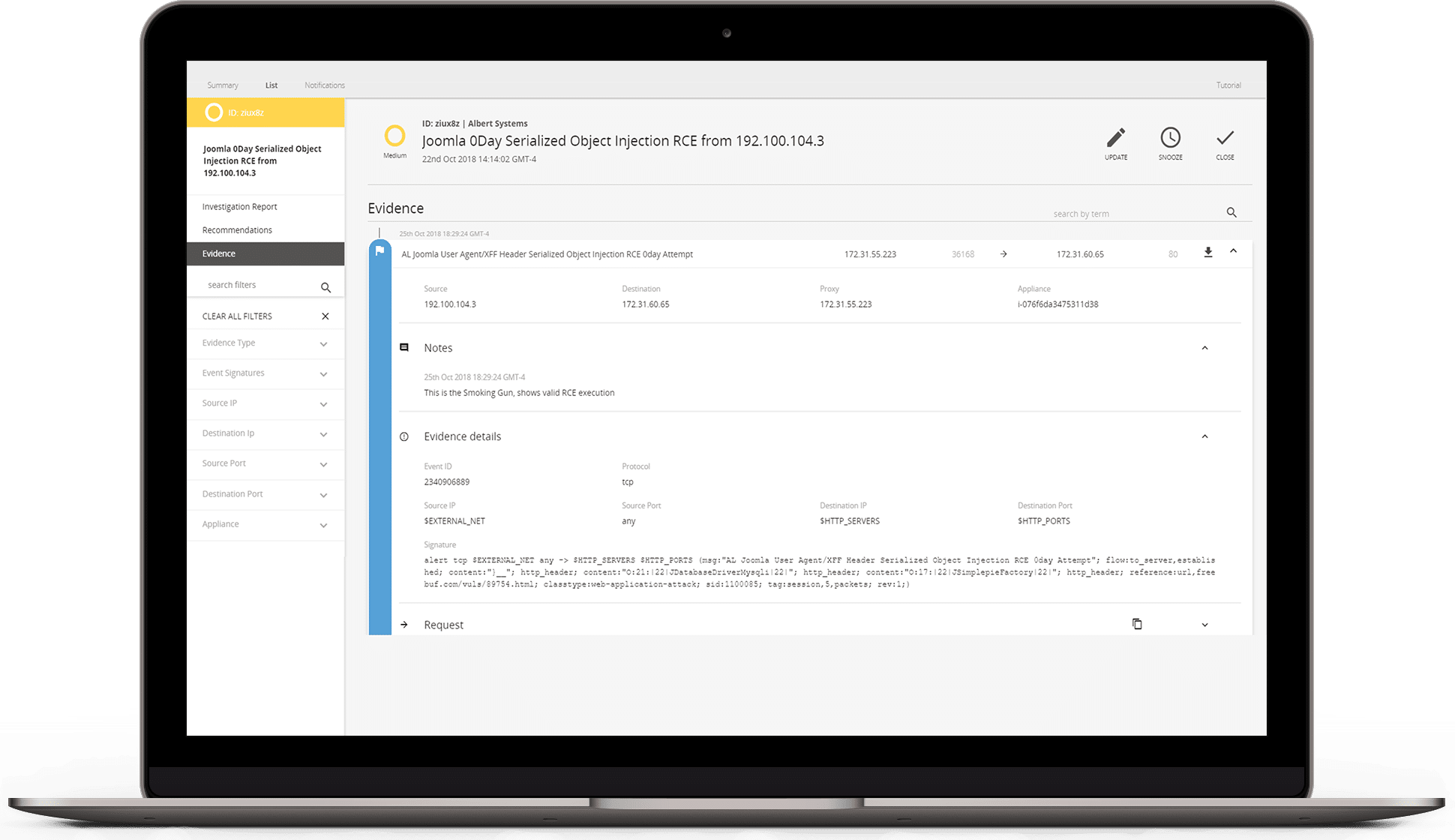
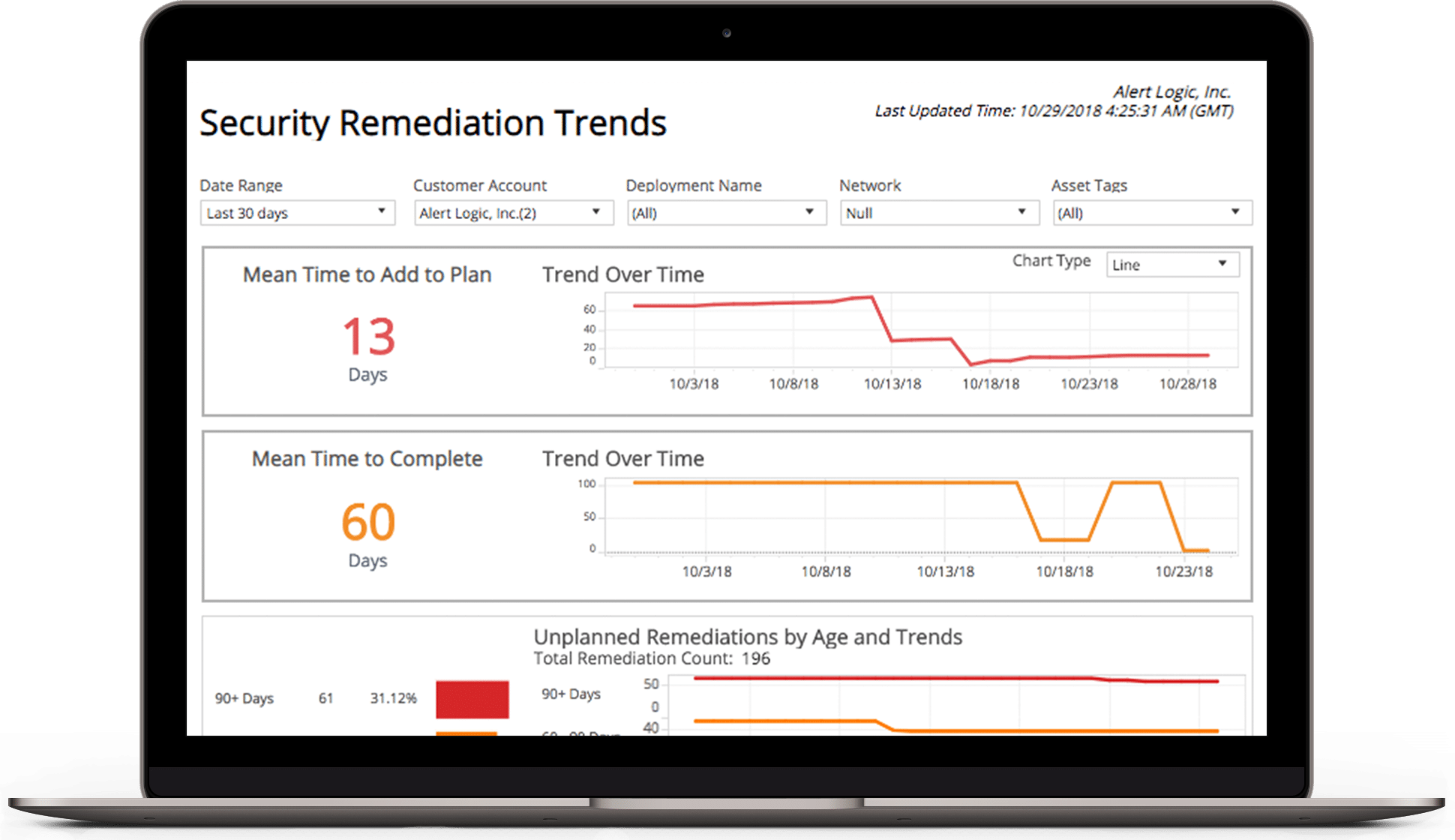
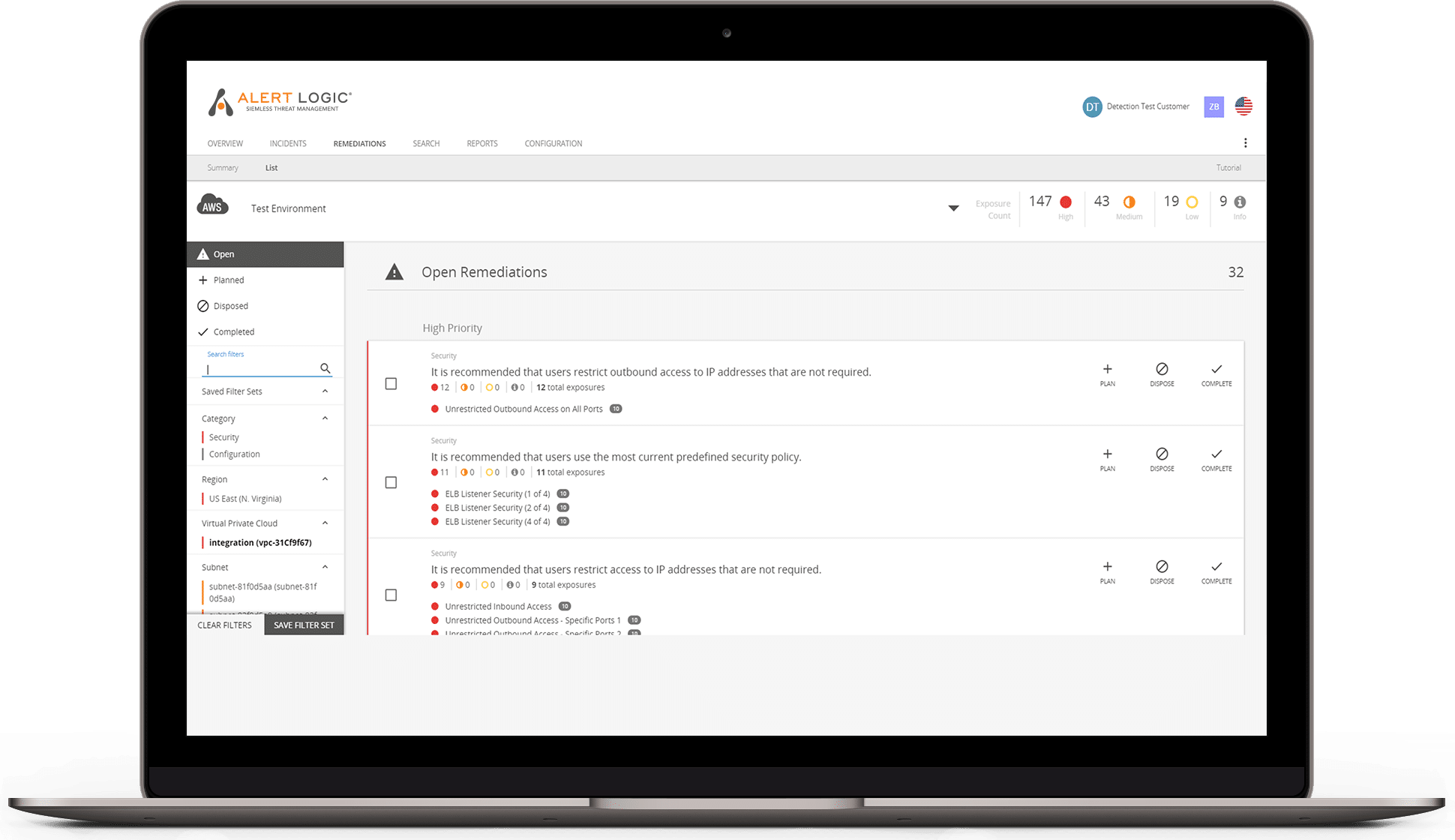
- Receive pre-built or ad hoc reports that include risk levels, threat details, potential impact, and detailed remediation recommendations
- Filter or search on asset groups, hosts, services, open ports, or specific vulnerabilities to find and address an emerging threat