There is a misconception out there that storing sensitive business information in third-party cloud services is less safe and secure than keeping it in-house. This couldn’t be further from the truth. In fact, the large data breaches we’ve all heard of such as Target, Anthem and Sony have actually occurred in on-premises data centers.
In an article from the Wall Street Journal, U.S. CIO Says Cloud Providers Offer Best Data Security, The United States Chief Information Officer Tony Scott said, “get to the cloud as fast as you can” as he believes that cloud providers have the ability to “do a much better job of security than any one company or any one organization can probably do.”
Third-party cloud providers such as Amazon.com, Google and Microsoft definitely have the skills and ability to provide high levels of security. They have hundreds of security professionals dedicated to ensuring their infrastructures are secure at the highest levels, plus they are done so with the industry’s best practices. However, it’s important to be aware that security in any cloud environment is a shared responsibility.
What do I mean by shared responsibility? All cloud providers use a shared security model when it comes to protecting the cloud, which means some areas of security are the responsibility of the cloud provider, and some of the customer. In other words, you can’t move to the cloud and expect the third-party cloud providers to take care of all your security needs on your behalf. It takes two to tango, and in this case, two to secure your cloud environment.
The shared responsibility model is made up of two components – “security of the cloud” and “security in the cloud.” “Security of the cloud” is what the cloud provider implements and operates on the customer’s behalf. They’re responsible for protecting the global infrastructures of services running in the cloud and the actual physical security of the facility in which the services operate. On the flip side, “security in the cloud” is the security measures that the customer implements and operates, related to the security of the content and applications that make use of the cloud provider’s services.
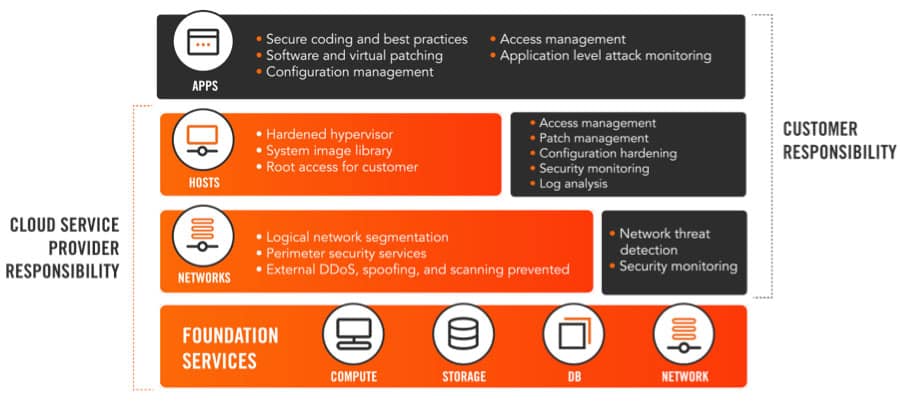
Here’s a breakdown of what falls into the cloud provider’s and the customer’s area of responsibility.
As you can see, there is a clear distinction of who is responsible for what, and both the cloud providers and customers need to meet their respective security responsibilities to ensure the environment is secure. Customers can be comforted that third-party cloud providers deliver a high level of security of the cloud, but they need to ensure that security in the cloud is addressed to protect the content that lives in the cloud provider’s services.
Watch our webinar on the evolving world of cybercrime, Behind the Scenes: The Cybercrime Landscape, to learn how threats are changing.
[Related Reading: Data Security Best Practices]
[Related Reading: Top Cloud Security Vulnerabilities]