Most modern web applications running in the cloud are built on an application stack comprised of the following nine components:
In this post we’re going to talk specifically about how Alert Logic protects the top layer of the application stack—packaged apps. Some examples of popular packaged apps include Oracle, SAP and SharePoint. When compared to hosted apps, which run at least partially in the cloud or a remote data center, packaged apps are generally all-inclusive and meant for local installation. In most cases, packaged apps benefit from increased performance due to low latency local-access, simplified single-tenancy design, and offline access—all of which can help to improve your security posture and regulatory compliance requirements.
However, the fact that you’re running a local, single tenant packaged app does not mean you can forget about security or compliance! Even standalone packaged apps require smart strategies for access, patch, and configuration management at the application and host levels. An effective security posture for a packaged app is going to require ongoing host-level threat detection, log analysis, and up-to-date vulnerability scanning in order to keep your data safe and secure.
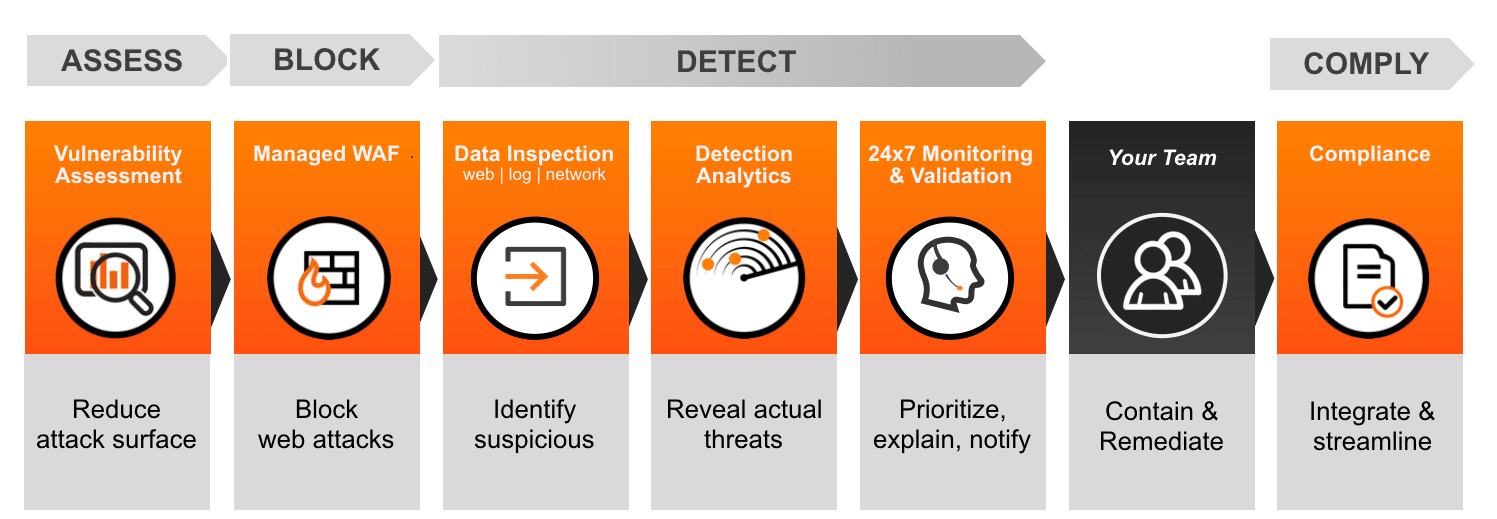
Alert Logic helps to protect your packaged app by providing six essential security and compliance controls that allow you to assess risk, block attacks, detect threats and comply with regulatory controls:
Let’s flesh out what that means in terms of real-world application stack protection and peace of mind. Consider Oracle — one of our original three packaged app examples.
Assess and Prevent Risk
Alert Logic provides nearly three thousand vulnerability scan checks for Oracle. These scans are a collection of well-documented high, medium, and low-risk common vulnerabilities and exposures (CVEs) known to impact Oracle, with attacks going back as far as 1999. And our coverage extends beyond just the Oracle database. We also have hundreds of known vulnerability scans targeted at Oracle Java, MySQL and Oracle ERP products like Peoplesoft, Fusion Middleware, E-Business Suite, Enterprise Manager, and Oracle WebLogic. Alert Logic uses automated agent-based and agent-less continuous scanning of assets to check for inherited or historical risks as well as current or future risks to your Oracle assets.
Prevent and Block Attacks
Alert Logic provides a managed web application firewall (WAF) to block web attacks to your Oracle application(s). Let’s outline this multi-step process:
- Customers are assigned a Web Application Security analyst who builds a custom ruleset for your environment using logged traffic violations. Your analyst familiarizes herself with your application and application parameters. Using samples of legitimate traffic, the analyst creates rules that are custom to your application.
- Your Alert Logic WAF analyst monitors your application’s behavior in order to build out positive and negative rulesets, which Alert Logic calls a policy. For example, if your analyst sees a parameter in an input form of your web application that only takes alphanumeric characters with one special character and that one special character gets flagged as a violation, the analyst can create a rule that allows only these characters. This is known as a whitelist-based rule. On the other hand, if all of the legitimate traffic to a specific parameter doesn’t cause a violation, it would not require a rule to be created. In this instance, negative signatures are used to detect any inbound attacks to this specific parameter field. If the WAF detects a remote code injection to a non-whitelisted parameter, it will block the attack as an OS Commanding injection. This is known as a blacklist policy. A WAF usually has an assortment of both whitelist and blacklist rules in each policy.
- Your Alert Logic WAF analyst works closely with you as an extension of your security team. While creating your policy, the WAF analyst selectively enables blocking rules as permitted by you after he/she monitors and learns your application’s functionality. This will minimize the chance of false positives and false negatives.
- Your Aanalyst continues to update and tune your WAF as your Oracle environment evolves. It’s worth noting that our WAFs can also detect data exfiltration in some instances and can be tuned to detect other sensitive data going outbound.
Threat Detection
Alert Logic threat detection is based on three main types of information:
- Log parsers scour system logs for potentially suspicious activity, such as with Oracle when new profiles are created or dropped, or the whenever the system is altered. They also detect brute force attacks (failed login attempts) or even simple access to network services like SSH or FTP, which are investigated by our system analysts. Log parsers can also detect an elevation of sudo privileges and other behavior that may require simple auditing. Alert Logic has over one hundred log parsers for Oracle.
- IDS inspection of network traffic utilizes nearly one thousand IDS signatures for Oracle. These attack signatures will detect numerous types of threats related to Oracle based on the most up-to-date threats in addition to well-known historical threats. Network pcap data is captured and is fed into the Alert Logic analytics engine for incident correlation. If an incident is created, an ActiveWatch analyst alerts you via phone call or email depending on your communication preferences.
- Human expertise. Alert Logic employs sophisticated machine learning and analytics in order to improve the quality and accuracy of the threat detection process. Couple that with our highly trained 24/7 staff of SOC analysts, who assist in providing insight and priority when a valid security threat has been detected, and you’ve got a winning strategy.
Comply with Controls
If you’re running Oracle for storing employee data, accepting and processing customer payment information, or archiving patient records, you are likely familiar with the increasing complexity of regulatory controls, such as SOX, PCI Compliance, or HIPAA. Fortra is an approved ASV scanning vendor for PCI. In addition, Alert Logic helps you meet the reporting requirements required by SOX as well as the log data review, intrusion detection and vulnerability scanning required by HIPAA. Visit our security compliance page to explore how Alert Logic can help.
Packaged apps such as Oracle sit at the top of your application stack and represent some of the most visible entry points for attackers looking to compromise your web applications. Top-of-stack attacks are generally harder to detect because they can appear like normal traffic, utilizing normal application pathways. Once compromised, attacks may sit idle, waiting for the right time to move deeper into your application stack. An effective security strategy must take a full stack approach in order to properly protect your data, and it all begins with protecting your packaged apps.