No one would argue against the importance of protecting an organization’s IT environment. But how to do this effectively is not always a decision that is reached easily. Fully internal (DIY), collaborative with an external partner or outsource as many elements as you can? Use 30, 40, 50+ tools from various vendors or use a select few tools hoping your internal team can manage them? Go with SIEM, EDR, XDR, MDR or a mix of these detection and response options? To make the best decision for your organization’s security strategy – either better defining your current strategy or creating one for the first time – you need to map out your ideal security outcomes.
Alert Logic’s had a recent webinar where Rohit Dhamankar, Fortra’s Vice President of Product Strategy, and Angelica Villarreal, Fortra’s Alert Logic Director of Product Marketing, discussed the right approach to achieving your security goals and strengthening your security posture with a detection and response solution. In this blog, we’re sharing learnings from our experts including key questions to ask and areas for consideration to give you a clearer understanding of which detection and response solution will work best for your organization.
Security Drivers, Outcomes & Organizational Challenges
While there’s no one driver or desired outcome for organizations’ security needs, the most common drivers can be placed into one of four buckets. Drivers of security needs:
Corporate drivers
Examples may include an organization has new leadership, board of directors requires defined security strategy.
Regulatory
Priority may be to comply with regulatory and industry requirements, failing an audit.
Operational
This may include when an organization was compromised/experienced a breach, competitor had a security incident.
Business model
May be a business transformation, adding a new environment (such as another public cloud).
Desired outcomes:
- Vendor consolidation
- Improved security posture
- Improved mean time to respond (MTTR)
- Simplify security operations and infrastructure
- Improve control and governance
- Demonstrate measurable value for security program
- Automate security program
In terms of security challenges an organization is experiencing, while they differ depending on the company, what we see as the number one challenge our customers are experiencing is lack of visibility across their environment. Can you really protect what you can’t see? Whether you’re operating in the cloud, on-premises, or in a hybrid environment, lack of visibility will derail any security strategy. With heightened digital transformation, your environment is likely changing rapidly and while these changes can help your business in many ways, they also can open you to new security challenges.
“With almost 4 million cybersecurity positions currently unfilled around the world, not being able to fill openings within an internal security team is a common problem,” said Dhamankar. It’s not only hard to attract and retain experienced cybersecurity talent, but tool complexity and the number of security tools organizations have each requiring specific skill sets and expertise makes it’s even more difficult to find a person with the right experience.
The evolving threat landscape is another security challenge for any organization, particularly in the mid-market size, trying to handle security internally. Threats evolve rapidly and are becoming harder to detect. Couple this with the new versions and tweaks to security technology and an internal team trying to stay abreast of the threats while learning the latest version of a security technology can be overwhelming.
Understanding What You Need to Protect
A security strategy and solution won’t be successful if you’re not clear on all you’re trying to protect and ensure you’re covering your entire IT landscape. At the end of the day, the fundamental question to ask yourself is what’s constitutes your organization’s attack surface? As you answer this question, make sure you’re considering your organization’s:
- Laptops
- Workstations
- Servers
- Network devices (including firewalls and IoT)
- IaaS/PaaS
- SaaS
It’s also important to remember that your security strategy encompasses prevention, detection, and response. Traditionally, many organizations have weighed prevention well above a response element of the strategy. Yes, you do want to stop every attack possible, but you have to be ready for that one malware that gets past your preventive efforts with a very strong detection and response component.
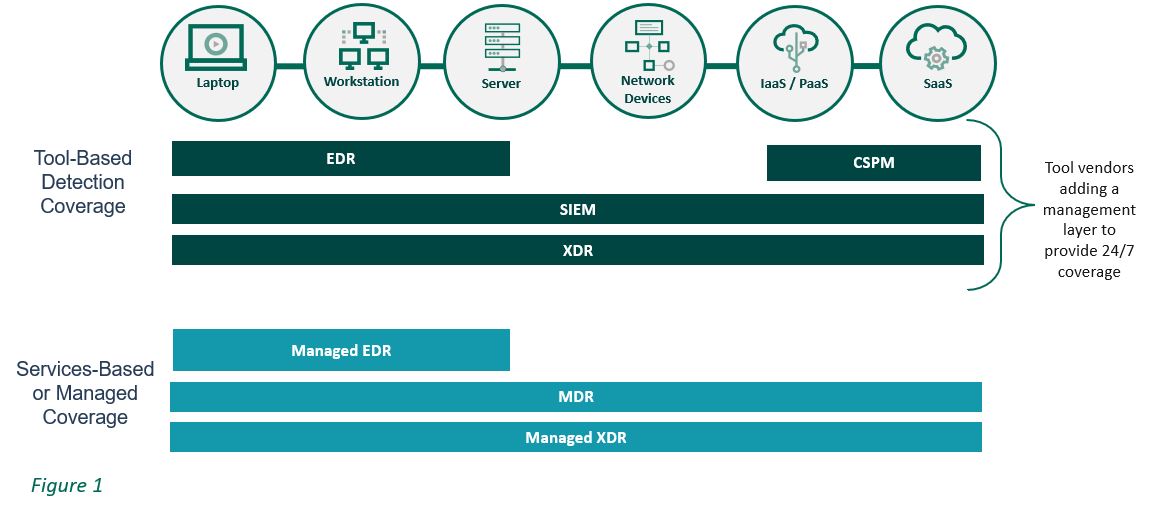
SIEM vs. EDR vs. MDR vs. XDR: Sorting Through Detection and Response Alphabet Soup
It seems like almost every year, there’s a new cybersecurity acronym or a new flavor of an existing term. Your security solution is more than just a name – it’s the elements within it that will help you in delivering a security strategy for your organization that enhances your security outcomes. Four of the more common security solution approaches include SIEM (Security Information & Event Management), EDR (Endpoint Detection & Response), MDR (Managed Detection and Response), and XDR (Extended Detection and Response).
SIEM: Collects data from many sources including workstations, application logs including servers, network devices, firewalls, and IDS.
- Coverage is most effective for endpoints, network, and SaaS
- Ideal for organizations with a high-volume log collection
- Not as effective a security solution for contextual awareness and understanding; detection and response capabilities; scalability; and real-time analysis
- Challenges/gap with SIEM include that it requires additional security technology to get value from it
Continued learning: What is SIEM? >
EDR: Delivered as a tool or a managed service, it has investigative, threat hunting and response capabilities when part of a managed service and can be used in conjunction with anti-virus (AV).
- Coverage is limited to endpoint telemetry
- Ideal when flexibility for integration with other security technologies is needed, primarily a prevention tool
- Not an idea choice for organizations that require multi-vector monitoring or those that are cloud heavy
- Gaps include a lack of visibility for cloud threats and it only covers a fraction of an IT estate
Continued learning: What is EDR? >
MDR: A solution that identifies security threats across an organization’s entire environment by combining technology, security operations, and human expertise to deliver actionable guidance to remediate and eliminate security threats.
- Coverage includes endpoint, network, and cloud
- Ideal for organizations that are resource or knowledge gapped; have 24/7 monitoring and threat mediation as a security outcome; need prevention and detection
- Not an idea choice for organizations with an established internal security operations center (SOC)
- Gaps include that while it acts as an extension of an internal team to provide actionable guidance, hands-on support may not be available
Continued learning: What is MDR? >
XDR: Providing broad coverage to more than one telemetry source, it provides centralized analytics include data collection and correlation and visibility; automation aspect includes playbooks and workflows with an ability to coordinate against multiple security tools.
- Coverage is full IT environment
- Ideal for organizations looking for a unified view of their environment or want to leverage their existing security tools
- Not idea for organizations lacking a defined security strategy
- Gaps include that the definition of the solution and its requirements are very inconsistent and vary significantly between vendors which can result in not achieving the security outcomes needed
Continued learning: What is XDR? >
The Managed vs. Unmanaged Debate
Deciding if you need a security solution that is managed by you versus a service provider can really come down to the skills set and experience of your internal team. Do you really want to have complete responsibility for the tools that give you visibility, detection and response or do you want another team to manage that for you? Can you commit to 24/7 monitoring with your internal team or just during standard business hours? Do you have the right tools and the personnel who can successfully manage and maintain them? Do you have security experts who are keeping track of the evolving threat landscape that could impact your business?
4 Key Areas to Evaluating a Detection and Response Solution
When examining potential security solutions, consider the following four areas:
Visibility and coverage
“It’s not unusual for a mid-sized company to have 50 to 60 security tools or an enterprise to have 130 tools,” said Dhamankar. “And even with all these tools, they may not be achieving their security outcomes when it comes to visibility.” When evaluating a security solution, make sure to learn:
- Do they provide comprehensive visibility across an entire IT environment?
- Do they have a growing base of threat intelligence and analytics to keep pace with the evolving threat landscape?
- Will you have access to subject matter experts and resources to obtain actionable context?
People, process and tools
A holistic, comprehensive security strategy goes well beyond the tools that are in place. Instead, it needs to be a balanced strategy including people, process, and tools if you are to achieve your desired outcome. With the right combination of these three areas, you should have an effective detection and response solution. Questions you need to be able to answer about your organization before even looking at solution providers include:
- Are you watching all potential points of entry or compromise?
- Do you know and understand your cloud security gaps?
- Does your internal team know how to respond efficiently?
- Can you identify misconfigured cloud services?
You also need to determine if your organization has any current gaps that a detection and response solution can fill:
- Knowledge gap: Internal team has limited knowledge and experience in security
- Resource gap: Tools are in place but you don’t have the people to deliver on the potential of the tools
- Outcome gap: You’ve made the investment in people and tools but you’re not achieving the security outcomes you need
Defense in depth (DID)
To achieve your security outcomes, embracing a defense in depth strategy – a multi-layered approach that acknowledges the complexity of the threat landscape and applies multiple countermeasures to achieve security objectives – is imperative. Two important defense-in-depth elements a security solution should include are:
- Products and controls are cohesively integrated which can lead to greater outcomes from signals.
- Significant third-party integrations to increase visibility and broaden the security scope
Focus on outcomes
“Effective detection and response solutions focus on delivering a meaningful security outcome meant to ease both pre-breach and post-breach concerns,” said Villarreal. “Solutions that just focus on prevention – that claim they can stop every attack – can lead to dire consequences.” Make sure the solution you choose is strong in both prevention and response:
- Reduce likelihood of an attack: Maximum visibility and the ability to detect and respond to threats combines with capabilities to minimize the impact of vulnerabilities, configuration issues, and attacks.
- Reduce the impact of the attack: Rapid detection and an automated response to contain the impact.
3 Steps to Security Service Success
Selecting a detection and response solution provider can be somewhat overwhelming, both in the steps leading up to even being able to evaluate a provider and then making sure you have all the information you need. Ensure you find out the answers to these three questions:
- Does the solution extend coverage and visibility across the entire attack surface?
- With the tools I already have, can I use them in a cohesive fashion and integrate them into a security strategy on my own or do I need help to accomplish this?
- How does the potential solution help achieve your identified security outcomes?
Improving your security posture and achieving your identified security outcomes is achievable with a detection and response security solution. The key is ensuring you’ve asked the right questions, delved into the solution providers approach, and know what you can – and cannot – expect from the provider.
Additional Resources:
Webinar: Understanding XDR, EDR and MDR 6 Key MDR Vendor Criteria SIEM Solutions for Security: What Vendors Won’t Tell You
