Now more than ever, organizations are struggling with understaffed, overwhelmed security teams and a lack of effective security tools. As a result, many are seeking to automate response to cyberthreats to lessen the load on their teams while maintaining their security posture.
But this isn’t as simple a solution as you may think.
Every organization is unique, and environments are dynamic. So, it’s important to understand that automated response is not a one-size-fits-all solution. In fact, fully automated response may bring you an even larger headache in certain scenarios.
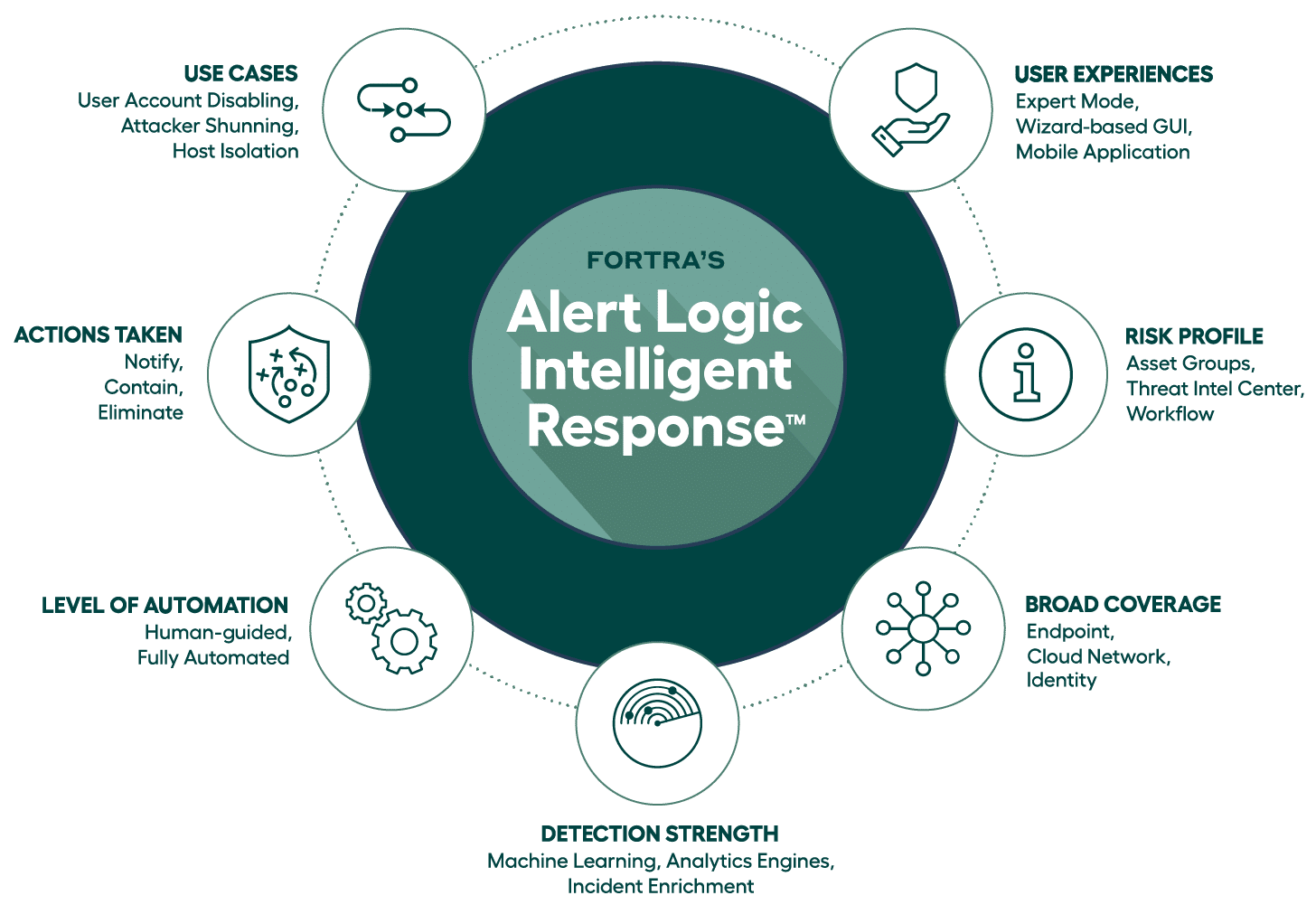
Alert Logic MDR with Intelligent Response is a solution that combines response automation with the appropriate breadth and depth of detection coverage and human expertise. The threat intelligence element – based on in-house research by our threat intel teams – ultimately enables custom response actions and allows you to deploy automation where appropriate.
What are the Benefits of In-house Threat Research?
Threat intelligence helps you stay abreast of known attacks and response actions. But what is the advantage of in-house threat research?
Simplicity
To achieve automated response capabilities, organizations are typically faced with implementing a SOAR (security orchestration, automation and response) solution – a process that can be very complex. And every minute spent implementing a solution is time not being spent analyzing security events, building security policies, and hardening the organization.
With Fortra’s Alert Logic MDR, we’re able to greatly simplify this process, getting our customers from setup to automation quickly.
How? Our in-house threat research ensures the latest threat data and responses are already incorporated into our solution, and therefore, the solution is always up to date. It eliminates the struggle organizations often face when integrating numerous disparate solutions into a single SOAR platform.
Scalability
Because security analysts are few in number and already overwhelmed, scalability is a challenge. The question many organizations ask is, “How can I get more data in front of our analysts to help them be more efficient, make decisions faster, and lower the amount of time spent on every alert?”
Reducing their workload through automated response is the key. After all, basic scanning and reconnaissance type-of incidents should not be handled by a human. It’s a waste of their time.
This doesn’t mean it isn’t important to get ahead of these incidents, but automation at this level is a great way to address them. By doing so, you’re able to greatly reduce the opportunity for attackers to identify a vulnerability in your environment, all without having to apply a human to the task. They then have the bandwidth to focus on what’s really important.
Noise reduction
Chasing down false positives is one of the leading timewasters for security analysts. Unfortunately, some security solutions are noisy, generating a huge volume of alerts without enough information or context to be able to make definitive decisions on what should be done.
Our Threat Intel Center correlates and curates data coming from your security products and provides only the most important information to our global Security Operations Center (SOC). We handle the routine attacks and put the most pertinent information in front of your analysts. With a <1% false positive rate, teams can be confident that automating an incident from Alert Logic will be meaningful and won’t have a negative impact on your business.
Rich response
Many organizations have invested in a vast array of security technologies, including endpoint detection (EDR), firewalls, intrusion detection systems (IDS), and more. Each technology serves a purpose to help guard against cyberattacks. But at the end of the day, they’re disparate solutions carrying different information.
Alert Logic is adaptive. Our threat research and intelligent response capability is not limited only to certain vendor products. We use data from many different vendors and platforms to deliver a comprehensive detection and response solution that enhances your security investment.
Learn More
Ultimately, automated response isn’t always enough. Our SOAR solution available through Intelligent Response equips you with the best understanding of your environments, the threat landscape, and any current or potential vulnerabilities.
That way, you can be confident in automated response where appropriate and devoting your resources where they’re most needed.
Learn more about intelligent response and the extended SOAR capabilities in our MDR solution.