Recently, the Cybersecurity & Infrastructure Security Agency (CISA) collected its recommendations to best protect against threats for MSPs and their customers in an alert, which included:
- Prevent initial compromise.
- Enable/improve monitoring and logging processes.
- Enforce multifactor authentication (MFA).
- Manage internal architecture risks and segregate internal networks.
- Apply the principle of least privilege.
- Deprecate obsolete accounts and infrastructure.
- Apply updates.
- Backup systems and data.
- Develop and exercise incident response and recovery plans.
- Understand and proactively manage supply chain risk.
- Promote transparency.
- Manage account authentication and authorization.
All these recommendations point to one blaring truth: it’s imperative to define your security posture and take decisive action to ensure it’s as strong as possible. My time in the military gave me a new perspective on effective cybersecurity, and I think it can help you too.
Lessons from the Battlefield
Prior to getting into IT security, I served six years in the United States Army, 10th Mountain and 101st Airborne Divisions, where I was deployed to Iraq and Afghanistan. My time in the military taught me many lessons about leadership, work ethic, and security — lessons that have served me well in my professional life.
Midway through my second deployment — this time in Afghanistan — I knew I was getting out of the army soon and I had to figure out my next career. I always had a passion for technology and knew that was a direction I wanted to go, but which path?
I was fascinated with the internet, so I explored networking. I bought Todd Lammle’s CCNA Study Guide and must have read the first few chapters three or four times, trying to fully understand the concepts. It wasn’t until I got to the section on security that it started to make sense.
I realized I could apply the same tactics I use for securing battle positions to secure computer networks. However, instead of using Claymores and machine guns, I would deploy anti-virus and intrusion detection systems. After all, the challenges we face in combat aren’t much different to the ones we face in cybersecurity: in both digital and physical warfare, we must manage for the unknowns.
Preparing for the Unknowns
In the Infantry, addressing the unknowns starts with building a battle plan. The objective is to understand the battle space, visualize where all the pieces on the board will be, and anticipate how they will be maneuvering throughout the battlefield.
Figure 1. Typical Army battle plan range card.
As we get deeper into the trenches, we build range cards for every battle position which allows us to draw out and manage each position’s sectors of fire. These cards are created and managed by the defenders in these battle positions. They’re carefully crafted, documenting every tree, ditch, or obstacle in the way. They also help us ensure overlapping sectors of fire, meaning these positions can see portions of the other position’s sector to ensure full coverage of the battle space.
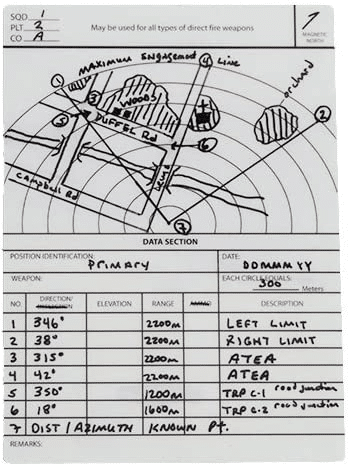
Figure 2: Typical Army range card.
Like all things, regardless of preparation, unknowns always occur so you must quickly identify and close security gaps. One of the methods used in the army to prepare for this is OCOKA: Observation of field of fire, Cover and concealment, Obstacles, Key terrain, and Avenues of approach. Although the battlefronts may differ, the same tactics should be used when securing your computer networks:
Observation of Field of Fire
When assessing a battle position, start with field of fire (mentioned earlier about overlapping sectors of fire applies here). Ensure you have full 360-degree coverage of your position. Likewise, in cybersecurity you can’t protect what you can’t see. Ask yourself: Will I know a new asset is spun up in my cloud environment? Will my security tools be able to see it? Do I have all my points of ingress and egress covered?
Cover and concealment
Each battle position needs to be properly concealed with good cover — don’t leave them exposed! Provide good protection against incoming rounds if their position were revealed and under attack. Similarly, ask yourself: How is our segmentation working? Are the firewall rules effective? Are applications behind our IPS?
Obstacles
Look for obstacles that could limit your ability to protect your position, as well as those that block the enemy from taking on your position. Relating to your IT environment ask yourself: What limitations do we have and what obstacles does the enemy need to navigate? Both have an impact to your security posture.
Key terrain
Identify critical terrain in the battle space that can be used to your or the enemy’s advantage. For example, during a mission in Afghanistan, my unit assessed our battlespace and noted a mountain about 800 meters west of our position with significant height advantage. We knew it was a risk and plotted coordinates to that location, creating pre-set variables with our mortars and F-15s. This would allow us to quickly call for air support if we were attacked from that location without the need to plot coordinates while under fire. I’ll save the rest of this story for another time, just know soldiers are still alive because of diligently planning for the unknown. For your organization you should ask: What are my critical assets? If an attacker were to gain access to certain aspects of our network, what’s the impact and what will be our response?
Avenues of approach
Finally, look at avenues of approach. If an attacker were to try to overtake your position, from which direction would they likely come? What are the ways a malicious attacker could gain access to your network, data, or key resources?
Following this method allows you to assess your security posture by modeling threats and identify exposures and risks BEFORE they impact you.
Assessing Your Security Posture
After running this process many times, I have concluded there are three key pillars which compose a security posture: Visibility, Exposures, and Threats.
Visibility
Observation of field of fire, avenues of approach, and key terrain are analyzed in OCOKA with an emphasis on visibility. In cybersecurity you must have solid visibility into your battle space. You can’t protect what you can’t see, so visibility is crucial!
Ask yourself: Do I know when a new asset is spun up in AWS, Azure, or our data center? Are the security tools aware? Are there agents installed and properly configured? Are we confident in how our perimeter devices are configured? Are our scanning tools able to access them?
Visibility is a tough problem to solve, especially when we contemplate the breadth of detection across the myriad assets.
Exposures
Once you understand your state of visibility it’s important to understand your exposures. You don’t need 100% visibility to start measuring, either. Visibility is arguably the most important of the three, but the objective is to know your current state as you consider the other pillars.
Exposure is equivalent to cover and concealment. You need to understand weaknesses in your battle positions. In other words, are your assets properly hardened and tucked away?
When evaluating exposures, look to better understand your risks. The word ‘exposure’ is intentional here as it broadens our conversation. We’re not just talking about out-of-date applications or services, but also misconfigurations, exposed S3 buckets, over-privileged IAM roles, and more. You need a full understanding of the breadth of your exposures and regularly monitor and report on them.
Threats
Threats are what you’re preparing for when using OCOKA and — based on how you’re being attacked — bring additional light to your assessment of the battle space. Considering your observations, are there any visibility issues or previously unknown exposures?
Your organization is under constant attack; constantly being probed from every direction for weaknesses. The question is: Do you know the types of attacks you’re experiencing and what assets they’re targeting? All too often I see businesses absorb these attacks and brush off successfully blocked attacks, chalking it up to “the tool doing its job”. That’s their known activities being actively dismissed. Instead, ask yourself: How can we use this data to manage our unknowns? Which assets take on most of the attacks? What types of attacks are we experiencing? How well are the controls working? How can we adjust because of these findings?
Understanding how you’re being attacked is critical in helping you prioritize your work. For example, how often do you consider your threats when prioritizing your patches? Can you determine the effectiveness of your email gateway by evaluating your reported and successful phishing attacks? As an industry, we often talk about layered defense and can overlook opportunities to measure the efficacy of these solutions.
Alert Logic Helps Drive Good Security Posture
An in-depth understanding of your visibility, exposures, and threats is critical when assessing your security posture. Applying this concept consistently will help you achieve measurable security outcomes and enable you to make decisions and prioritize projects based on data.
Fortra’s Alert Logic offers unrivaled managed detection and response (MDR) capabilities to help you gain visibility to the most pressing threats which could impact your organization and respond quickly and effectively. With our team of security experts monitoring your environment 24/7, your security posture is our top priority.
Fortra’s Alert Logic MDR dashboard brings security insights to your fingertips with real-time access to information on risk, vulnerabilities, remediation activities, configuration exposures, and compliance status. And coming soon, the unique ability to quantify your security posture for the first time.
To learn more about Alert Logic’s managed detection and response solution, visit Alert Logic and schedule a live demonstration.
