Malware attacks are on the rise. According to ITRC, in 2023, there were 3,205 publicly reported data compromises that impacted an estimated 353,027,892 individuals.
The increasing digitization of businesses and whole industries over the previous few decades has emboldened black-hat actors and made organizations more susceptible to attack. The prevalence of malware attacks has skyrocketed since COVID-19 when many organizations moved their operations completely online.
Many businesses don’t take malware attacks seriously until it’s far too late. Contrary to what many believe, malicious actors don’t just target organizations with deep pockets — they cast wide nets and exploit any vulnerabilities they find.
For that reason, it’s important for every organization to understand the basics of malware attacks: What they are, the common malware types and what to do to prevent them from happening.
What Is Malware & Why Is it Important to Understand?
Malware, or malicious software, is a type of software designed to intentionally cause damage to computers, systems, servers and networks, typically (but not exclusively) to extract some form of monetary payment from the owner.
It’s important for individuals and organizations to understand malware attacks. The incidence and success rate of these security breaches have been on the rise in recent years, making them one of the biggest — yet most preventable — expenses for businesses. The average cost of a ransomware attack in 2023 was $5.13 million. They can put enormous financial strain on organizations, erode trust in their brand and ultimately cause permanent damage that they may struggle to recover from.
The Most Common Types of Malware
There are numerous different types of malware, each with their own attack profiles, objectives and even end-goals. Here are the most common:
Trojan
This form of malware tricks unsuspecting users into downloading and configuring apparently legitimate software applications. Once the program has been executed, the trojan installs the malware into the host system and begins exfiltrating data and encrypting passwords.
Spyware
Spyware is one of the most harmful types of malware. In the event of an attack, users are often unaware that their servers have been infected. Spyware can enter a system in a variety of different ways, including an app installation, downloading malicious attachments or visiting a malicious website. Once inside, spyware runs in the background of the device, collecting reams of user information and relaying this to third parties.
Ransomware
Ransomware attacks have grown exponentially in recent years, making them one of the most lucrative sources of income for cybercriminals. This style of cybersecurity breach happens in a number of ways, but the most common attack vector is through phishing.
Unsuspecting users receive prompts to exchange personal information, usually through an email from a purported trusted source. Cybercriminals use this information to penetrate networks, encrypt sensitive data and, ultimately, demand huge ransoms from their victims.
Adware
Among the least harmful types of malware, adware works by bombarding users with pop-up ads paid for by third parties. Although adware is typically more of a nuisance to users than a serious threat to their private information, failure to remove adware could lead to browser slowdown that may eventually render the device inoperable. Adware programs usually gain access to devices after a user downloads a malicious program.
Worms
Computer worms infect devices by exploiting security vulnerabilities and replicating themselves to infect other devices. Unfortunately, even after the device owner has identified and removed the worm, most of the damage might already be done. The primary objective of the worm is to remain on the host server for as long as possible and infect as many other systems as it can, so even if users have recovered the initial device, many others in their network will likely already be infected.
Fileless malware
Fileless malware attacks are a more sophisticated means hackers use to penetrate systems. This malware type gains access to the host computer system through legitimate software or applications downloaded via a malicious link, usually through email. Fileless attacks operate strictly in memory, leaving no digital footprint and making it extremely difficult for security systems to detect them.
How Malware Impacts Businesses
In many cases, malware is more than a straightforward problem that businesses can quickly pay to have fixed and removed. At its worst, malware can infect entire networks and steal huge sums of sensitive data information, requiring costly interventions to remediate.
Even when handled successfully, the impact of malware attacks can permanently damage a business’s operations, brand image and revenue flows. Here are some of the ways malware can affect organizations:
Slows operations
One of the hallmarks of a malware infection from the user perspective is that devices and browsers become so slow they’re rendered almost inoperable. In worst-case scenarios, malware can make critical systems and data completely inaccessible, meaning employees are unable to use the devices and access the programs they need to do their jobs.
Damages customer relationships
Business relationships in the digital economy are founded on trust. Customers share huge amounts of their personal data with the brands they buy from, and that means data privacy is a top priority. When companies are subject to a malware attack, it demonstrates to customers that they aren’t taking the right precautions to protect data, potentially signaling to them that they’re careless with their private information. This can have a permanent effect on trust and brand reputation.
Depletes resources
Probably the most obvious and harmful effect of malware attacks, malicious actors often demand massive sums of cash to decrypt sensitive information. Although security experts strongly advise against it, many companies simply choose to pay the ransom and hope the problem goes away. Even if they heed the warning, they will often still have to pay huge amounts to recover lost data and undo the damage to their brand.
Creates more vulnerabilities
Most malware attacks work by either stealing sensitive information, gathering data in the background of regular browsing sessions, or encrypting account login credentials. Even if an organization keeps backups of its sensitive information (which is a key part of any recovery effort), malicious actors will often retain access to stolen information, which they could use to advance other nefarious purposes.
How to Identify and Prevent Malware Attacks
Understanding what a malware infection is and how it can affect businesses is the necessary starting point. Even more important, however, is knowing how to identify when an attack has taken place and what steps security analysts can take to maximize their organization’s resistance to security breaches. While specific identifiers don’t necessarily apply to all types of attacks, there are a few worth noting. These include:
Pop-up ads
Adware infects devices and enables third parties to push advertisements to browsers. If you’re being bombarded with pop-up ads that’s a telltale sign your device has been infected by malware.
Browser slowdown
Malware attaches itself to your device’s internal systems and uses them to fuel its malicious activity. Over time, this can cause your browser to slow substantially below normal levels. If your devices are operating much slower than normal or are frequently crashing, that could be a sign of malware.
Ransom demands
One of the most conspicuous indicators that you’ve fallen victim to a malware assault is receiving ransom demands from unidentified individuals asserting they’ve encrypted your data. It’s never advised to pay to resolve a ransomware attack as doing so encourages further criminal activity and there is no guarantee you will get your stolen data back.
Unusual activity
As PC users become more adept at identifying and preventing malware attacks, threat actors have developed more subtle ways to infect host computers. Any activity that seems especially unusual — like getting ads on government websites or an inability to remove certain software — is likely a sign of a malware attack.
Losing account access
In the event of a ransomware breach, cybercriminals typically pilfer login credentials and extort a ransom in return for decryption keys. If you find yourself locked out of vital accounts, such as banking portals, it’s probable you’ve fallen victim to malware infiltration.
The better hackers get at penetrating devices, the more difficult malware detection is. Even if you don’t detect any unusual activity on your network or device, it’s still important to be on guard to ensure malware isn’t secretly stealing sensitive information in the background of your browsing session.
Malware Prevention
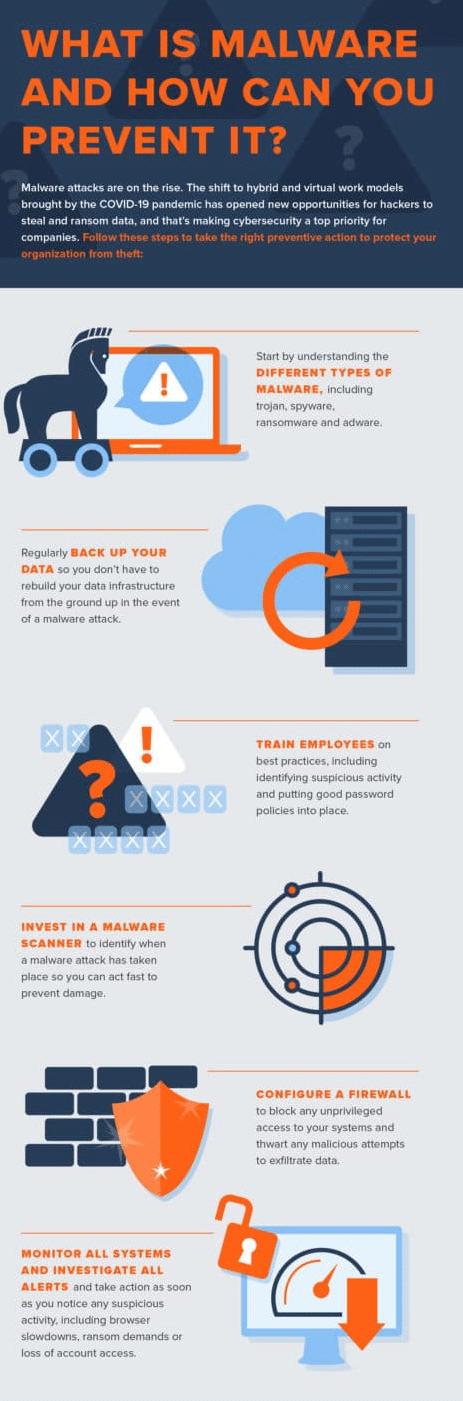
Preventing a malware attack before it occurs is the optimal strategy. Although some organizations perceive malware prevention as demanding costly and extensive security measures, significant strides can be made through the implementation of essential best practices, alongside security systems.
Keep backups
Successful malware attacks rely on gaining exclusive access to your data, so keeping backups is one of the most effective ways to thwart malware attacks. Make sure you back up your data as frequently as possible and, ideally, storing it in a secure, offsite storage location. In the event of a malware attack, you won’t have to rebuild your data infrastructure from the ground up, saving precious time, money, and stress.
Educate users
One of the most prevalent and easily manipulable avenues for attack is user error. Individuals, unaware of potential threats, may unknowingly interact with harmful elements, such as clicking on links or downloading files from seemingly familiar sources, thus inadvertently activating malicious software. It’s imperative to provide comprehensive education to all staff members regarding optimal practices, which encompasses instructing them on recognizing dubious emails or online solicitations and implementing more rigorous password protocols.
Invest in a malware scanner
Preventive measures such as maintaining backups and providing user education are crucial. Despite our best efforts, unforeseen events may occur. In such instances, it becomes imperative to have reliable security software in place to promptly detect malware attacks, enabling swift intervention to mitigate potential long-term harm.
Configure a firewall
It’s imperative to invest in a comprehensive firewall to block unauthorized users from accessing your systems to protect against a wide range of malware attacks.
Malware attacks are on the rise. Businesses need to be prepared with the latest solutions and technology to enhance their security posture and protect their sensitive information from attack. And that starts with having the right team of cybersecurity professionals on your side. Fortra’s Alert Logic’s global security operations center (SOC) experts monitor your systems 24/7 and leverage a diverse range of data collection and analytics methods for rapid threat detection. The comprehensive coverage provide by our managed detection and response (MDR) solution utilizes a combination of people, processes and tools to reduce the likelihood of successful attack.
Schedule a demo today to get started.